Ransomware is a type of malicious software that encrypts files on a device or network, preventing access until a ransom is paid. The average ransom amount paid to cybercriminals continues to rise each year as ransomware attacks become more targeted and sophisticated.
What is ransomware and how does it work?
Ransomware is a form of malware that encrypts files on a system, rendering them inaccessible to the rightful user. The attackers then demand ransom payment in cryptocurrency, such as Bitcoin, in exchange for the decryption key to restore access. Most ransomware is spread through phishing emails, infected software apps, compromised websites, and vulnerability exploits.
Once inside the system, the ransomware locates and encrypts critical files and data. It may target documents, media, databases, and other file types. The encryption algorithms used by ransomware are often complex and difficult to crack. Many ransomware strains also search connected drives and networks to maximize damage and leverage higher payment.
Users are presented with a ransom note demanding payment within a short timeframe. If the ransom is not paid by the deadline, the attackers threaten to delete encryption keys, make data inaccessible, or publicly release sensitive data. However, paying the ransom does not guarantee files will be recovered.
What is the average ransom amount?
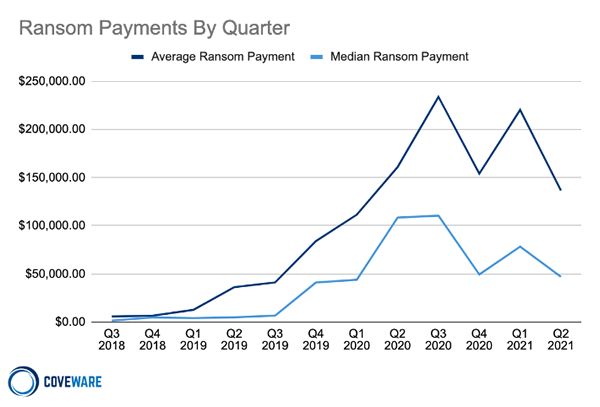
According to cybersecurity firms who track ransomware payments, the average ransom payment has substantially increased over the past several years:
- In 2020, the average ransom payment was around $150,000 USD.
- In 2021, the average payment grew to $540,000 USD.
- In the first quarter of 2022, the average ransom payment spiked to over $2 million USD.
Some key factors contributing to the rising costs include:
- Ransom demands are based on how much attackers believe the victim organization can pay. Attacks on larger enterprises, hospitals, and critical infrastructure result in higher ransom demands.
- Newer ransomware strains are more sophisticated, leverage automation, and have greater damage/disruption potential, commanding higher payments.
- Extortion tactics like threatening to release data raise payment amounts.
- Ransomware-as-a-Service lowers barrier to entry, increasing number of attacks.
Most expensive ransomware payments
While the average payment may be in the six-figures range, some organizations have paid ransoms in the tens of millions due to the critical need to regain access and mitigate reputational damage. Some of the largest publicly reported ransomware payments include:
| Organization | Ransomware Type | Payment |
|---|---|---|
| Colonial Pipeline | DarkSide | $4.4 million |
| JBS Foods | REvil | $11 million |
| CNA Financial | Phoenix CryptoLocker | $40 million |
These record-setting payments indicate that large critical infrastructure companies and regulated industries like energy, food, and finance may have little choice but to meet ransomware demands to maintain operations and limit fallout.
Industries most impacted by ransomware
While no industry is immune to ransomware, attackers tend to target organizations that are more likely and able to pay significant ransoms. According to cybersecurity research, the top 5 industries most impacted include:
- Healthcare – Hospitals and medical facilities tend to have critical data and systems that cannot afford extended downtime, making them willing to pay. Healthcare ransomware attacks increased in 2020 and 2021.
- Education – Schools, colleges, and universities house sensitive student data and intellectual property that serve as leverage for higher ransom payouts.
- Government – State and local government agencies have paid some of the highest reported ransoms to recover citizen data and restore public services.
- Manufacturing – Manufacturers rely on operational technology and production lines that necessitate fast recovery, leading to ransom payments.
- Retail – Retailers’ need to maintain customer data confidentiality and business continuity makes them ransomware targets.
Most common ransomware variants
While new ransomware strains emerge frequently, several established variants are responsible for a majority of attacks. The most prevalent include:
- Sodinokibi (aka REvil) – This ransomware-as-a-service allows affiliates to customize attacks, increasing infections globally.
- Conti – Uses advanced encryption methods and also threatens to leak data if ransom isn’t paid.
- DarkSide – Known for “big game hunting,” it focuses on large critical infrastructure organizations.
- Phobos – Targets healthcare, software, and IT companies worldwide.
- Ryuk – A targeted, highly-lucrative variant often manual deployed on networks.
These strains utilize robust encryption, are offered via ransomware-as-a-service, and many operate on the dark web. Their techniques and capabilities continue advancing to maximize criminal profits.
Factors that influence ransom amounts
Cybercriminals determine ransom amounts based on a variety of factors related to the victim organization:
- Company size – Larger firms with higher revenues get charged larger ransoms.
- Industry – Public utilities, healthcare, and other essential services often pay more to quickly restore function.
- Data sensitivity – Threat of exposing trade secrets or personal data results in higher ransoms.
- IT sophistication – Perceived ability to pay factors into ransom demands.
- Insurance coverage – Criminals increase ransoms for insured entities since insurers may cover the payments.
Attackers also gauge ransom based on their own business models and objectives. Affiliates in ransomware-as-a-service schemes may be required to pay a cut to malware creators, reducing their ultimate take.
Ransom payment methods
Cybercriminals overwhelmingly demand ransom payments in untraceable cryptocurrency, primarily Bitcoin. Monero is another alternative. This preserves attacker anonymity and makes payments hard to track or recover.
Victims are given a Bitcoin wallet address to send payment. Keys are released after the transaction is verified on the blockchain. Attackers may also require victims to use mixers or tumblers to launder cryptocurrency payments first.
In rare cases, ransomware gangs have also requested ransom amounts in the form of gift cards, prepaid cash cards, or wire transfers. This tends to involve less sophisticated attackers who have difficulty cashing out large cryptocurrency payments.
Should ransomware payments be made?
Paying ransomware is a complex dilemma organizations must weigh carefully. There are arguments on both sides:
Reasons to pay:
- Quickest way to regain access and resume operations
- Prevents threat actors from leaking or selling data
- Cheaper than downtime and recovery without keys
- Shows employees and customers the problem is being addressed
Reasons not to pay:
- No guarantee files will be decrypted
- May fund criminal entities to conduct more attacks
- Paints a target on organization as one willing to pay
- Other options exist like backups that don’t fund criminals
There are merits to both perspectives. Each organization needs to weigh the specific circumstances, legal/regulatory obligations, costs, and ramifications involved.
How are ransom payments tracked?
Security researchers and blockchain analysis firms closely track ransomware payments to identify trends and cybercrime monetization. Some ways ransom transactions are monitored include:
- Dark web forums – Criminals discuss attacks, ransom amounts, and payments.
- Blockchain forensics – Following the flow of cryptocurrency payments on the blockchain.
- Honeypots – Fake systems that simulate ransom payments for surveillance.
- Industry reporting – Mandatory cyber incident reporting in sectors like healthcare.
- Public records – Securities filings, breach notifications, leaks.
By profiling payments clusters, attack indicators, and conversations, researchers can accurately estimate average payments. Public reporting also sheds light on record ransoms.
Law enforcement actions against ransomware
Combating ransomware is an increasing priority for law enforcement and international cooperation to disrupt the economic models. Actions taken include:
- Takedowns of major ransomware variants like REvil.
- Charging ransomware operators for crimes.
- Seizing ransomware extortion sites.
- Cracking down on money laundering infrastructure.
- Banning ransomware payments by some governments.
- Establishing cybercrime task forces to enhance collaboration.
Despite these efforts, the ransomware economy persists driven by cryptocurrency enabling pseudo-anonymous payments. The high profitability continues to drive new threat actors, malware innovations, and countless new victims.
Should ransomware payments be banned?
Some policymakers have proposed legally restricting ransomware payments, but a ban raises additional problems:
- It removes one recovery option for desperate victims.
- Attackers may ignore bans and still demand payment.
- Threat actors could increase harmful data leaks or cyber vandalism.
- Blanket ban could affect non-ransom cyber insurance claims.
- Companies may try to pay covertly anyway.
- Difficult to enforce across global private companies.
- Does not fix root problems that allow breaches.
Before pursuing payment bans, we need enhanced cyber resilience, reporting mechanisms, and centralized coordination against ransomware. Payment restrictions could be considered once international collaboration matures.
What are alternatives to paying ransomware?
Instead of paying the ransom, organizations can pursue options such as:
- Restore from clean backups – Ensure current, offline backups are available.
- Investigate decryption – Some ransomware is crackable by cyber firms.
- Hire incident response – Forensics experts can analyze options.
- Rebuild systems – Completely rebuilding compromised systems removes malware.
- Monitor credit – Finance firms can watch for misuse of stolen data.
Prevention is still the best medicine through practices like:
- Employee security training
- Endpoint and email security
- Vulnerability management
- Privileged access controls
- Incident response planning
Organizations willing to invest more in proactive cybersecurity are less likely to be severely impacted by ransomware events.
Conclusion
Ransomware presents an evolving threat to organizations of all types and sizes. While early attacks focused on consumers, modern ransomware is highly targeted and financially motivated against enterprises. Record payments now routinely are in the millions to restore critical systems and data.
Tracking ransomware payment trends provides insight into the cybercriminal economy. However, bans on ransom payments face challenges in implementation and may unintentionally cause additional harm. The most effective path forward relies on continuously improving cyber defenses, updating regulations, digital forensics, and fostering collaboration between public and private sectors to make ransomware less profitable.