CryptoLocker is a type of ransomware that encrypts files on infected computers and demands payment in order to decrypt them. It first appeared in 2013 and has impacted many individuals and organizations. Unfortunately, once files are encrypted by CryptoLocker, they cannot be decrypted without paying the ransom or finding the cryptographic keys. However, there are some things that can be done to potentially recover files or prevent becoming infected in the first place.
What is CryptoLocker and how does it encrypt files?
CryptoLocker is a form of ransomware, which is malicious software that encrypts files on a computer and demands payment in order to decrypt them. It is spread through infected email attachments, compromised websites, and exploit kits.
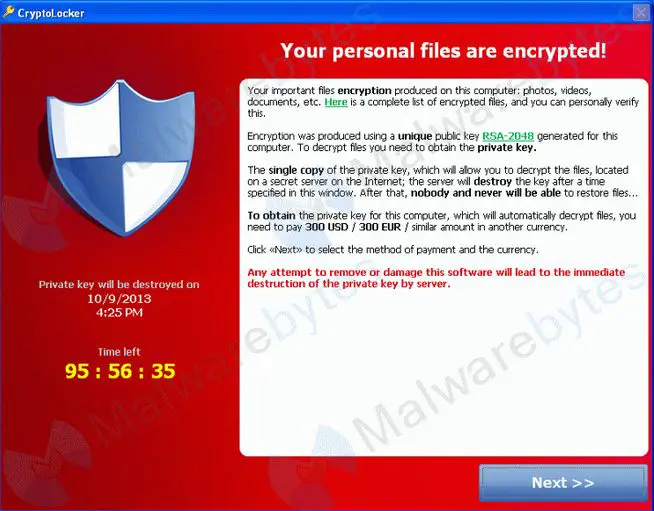
Once installed on a computer, CryptoLocker uses strong RSA-2048 and AES-256 encryption to encrypt files with certain extensions, such as Microsoft Office files, images, videos, and PDFs. The private decryption keys are only known by the attackers. CryptoLocker will skip encrypting files in directories containing certain keywords, such as “windows” or “program files,” to avoid rendering the system inoperable.
A ransom note is displayed demanding payment within 72 or 100 hours before the decryption keys are destroyed. The ransom demand is typically between $200-$700, paid in Bitcoin or pre-paid cash vouchers. If the ransom is not paid in time, the attackers will delete the decryption keys, rendering files inaccessible forever.
Is it possible to decrypt files without paying the ransom?
Unfortunately, without access to the decryption keys held by the attackers, it is virtually impossible to decrypt files encrypted by CryptoLocker. The encryption algorithms used are strong commercial grade schemes that would take an extremely long time to break through brute force alone.
Some methods that have been attempted to recover files include:
Brute forcing the decryption keys
This involves trying every possible decryption key until the right one is found. However, at 2048-bit encryption, there are over 300 trillion trillion trillion possible keys. It would take millions of years to go through all combinations, making this method infeasible.
Exploiting flaws in the encryption implementation
Researchers have analyzed CryptoLocker’s code to look for weaknesses in how the encryption is implemented. So far, no practical vulnerabilities have been found that could lead to easy file recovery.
Looking for leftover keys on infected systems
Some ransomware variants have made mistakes that left decryption keys on the infected system. But the CryptoLocker operators are careful to not leave keys behind.
Identifying the attackers
If the identities of the CryptoLocker operators were known, law enforcement could potentially seize their servers and private keys. However, the group responsible remains at large.
Restoring from backups
If clean backups exist that predate the infection, files can be restored by overwriting the encrypted versions. But many victims find their backups were also encrypted.
Can files be recovered if the ransom is paid?
Paying the ransom is no guarantee of decrypting files. According to the FBI, less than 1% of CryptoLocker victims who paid the ransom reported getting their files unlocked. However, other estimates report a better decryption success rate after payment.
There are a few reasons the decryption process may fail even after paying:
Difficulties paying the ransom
The ransom demands are made in Bitcoin or prepaid vouchers, which can be difficult to acquire quickly. The short payment deadline may expire before victims figure out how to pay.
Attackers simply take the money
The cyber criminals may have no intention of providing working decryption keys after receiving ransom payments. The remote nature of the transaction makes it easy for them to take the money and run.
Flaws in the decryption process
There could be bugs in the decryption software that prevent proper file recovery. The attackers have to manually send working keys and decryption tools to each victim who pays.
Deletion of keys
If the deadline expires before a victim pays, the attackers may delete the private keys before a payment is attempted. This renders files unrecoverable.
So while paying the ransom offers a chance of getting files decrypted, there is a good probability the decryption process will fail. Victims face a difficult choice.
What methods can be used to prevent or recover from CryptoLocker?
While CryptoLocker is difficult to recover from once encrypted, there are some prevention and recovery measures that can be taken:
Antivirus and anti-malware software
Having endpoint security that uses heuristic detection capabilities can block many ransomware variants before encryption occurs. Signature-based detection can also catch known samples.
Email security and spam filtering
Stopping infected emails from reaching end users can prevent infection. Analyzing attachments and blocking emails with certain characteristics can reduce the attack surface.
Popup blockers and ad blockers
Preventing malicious ads and popups can stop ransomware that is distributed through exploit kits on compromised websites. Disable ads in browsers.
Software updates and patches
Keeping operating systems and applications fully updated eliminates vulnerabilities that can be leveraged to deliver ransomware. Turn on automatic updates where possible.
Backups
Maintaining recent backups of critical files on disconnected external media allows for recovery after an attack. Backups should be protected and regularly tested.
User education
Training staff to identify social engineering attempts, suspicious emails, and unsafe browsing practices helps end the infection chain. Teach critical thinking around threats.
Segmentation and least privilege
Following the principles of zero trust and minimizing account and network permissions prevents lateral movement and containment of threats when they occur.
Incident response planning
Having a formal response plan for cases of ransomware allows for efficient containment and recovery following attacks. Know who to call and what steps to take.
How does Cryptolocker encrypt files?
CryptoLocker uses a combination of asymmetric and symmetric encryption to lock files. It follows this general process:
1. Generate RSA public-private key pair
When first run, CryptoLocker generates a unique RSA public-private key pair using the cryptographically secure RSA-2048 algorithm. The private key is stored by the malware operators.
2. Extract files and metadata
CryptoLocker recursively scans local and mounted network drives to build a list of files matching certain extensions to target for encryption. It collects filenames, original paths, sizes and other metadata.
3. Generate AES keys for each file
For each targeted file, CryptoLocker randomly generates a unique 256-bit AES symmetric encryption key. This key will be used to encrypt the file contents.
4. Encrypt AES keys with RSA public key
The randomly generated AES keys are themselves encrypted using the previously generated RSA-2048 public key. This ties the AES keys to the RSA private key needed for decryption.
5. Encrypt files with AES keys
CryptoLocker encrypts the contents of each target file using its unique AES-256 key in CBC mode. The original files are replaced with scrambled ciphertext versions.
6. Delete original AES keys
After the AES encrypted files are written, CryptoLocker deletes the original AES keys, leaving only the RSA encrypted versions for decryption. This minimizes traces of keys left behind.
7. Post ransom note
Finally, CryptoLocker displays its ransom payment demand to decrypt the now-encrypted files. This note contains payment instructions and threats of permanent data loss if ignored.
This hybrid cryptosystem allows the malware to efficiently encrypt files with AES while also tying decryption to the RSA key pair under the attacker’s control. Both components must be present to recover files.
What is the impact of Cryptolocker infections?
CryptoLocker has had a significant financial and operational impact on affected individuals and organizations. Some examples include:
Cost to recover files
Typical ransom demands are $200-$700 per infection, paid in cryptocurrencies or prepaid cards. Organizations can end up paying thousands or tens of thousands to decrypt all computers.
Loss of irreplaceable data
Photos, documents, and other personal files may be lost forever if decryption fails or is not possible. This can have an emotional toll.
Downtime and business disruption
Being locked out of critical files and systems while encrypted causes work and productivity slowdowns. Time is lost cleaning up.
Remediation and recovery costs
Additional IT costs are incurred trying to clean the infection, restore systems from backups, and boost security to prevent future attacks.
Legal and compliance problems
Data loss and system downtimes can lead to breaches of contracts, service agreements, and compliance regulations. Fines may result.
Reputational damage
Being impacted by ransomware can harm an organization’s reputation as a trusted partner and secure custodian of data. This harms future business.
Billions of dollars in combined costs have resulted from CryptoLocker attacks globally. However, the psychological and business operation impacts can be just as significant.
Notable CryptoLocker attacks
Here are some examples of major organizations and agencies that have suffered significant damage due to CryptoLocker ransomware attacks:
University of Calgary
The Canadian university paid a $20,000 ransom in 2013 to decrypt critical systems and student data after becoming infected through an emailed PDF.
Swansea Police Department
This police department in Massachusetts paid a $750 ransom in 2013 after most of their case files were encrypted by CryptoLocker.
Memorial Hospital
An Indiana hospital’s Cancer Care Center lost access to patient records after becoming one of the earliest victims of CryptoLocker in 2013.
C argparserre, PA
This town’s computer systems were hit in 2013 leading to the shutdown of email and delays in paying police and municipal employees. They refused to pay the ransom.
Dell SecureWorks
In 2015, security company Dell SecureWorks advised a client not to pay a $10,000 CryptoLocker ransom, as their backups were intact.
Pittsburgh Public Schools
In 2019, ransomware encrypted half the servers belonging to the Pittsburgh Public School District in Pennsylvania. Many teachers and students lost files.
These examples illustrate how diverse organizations have been impacted by CryptoLocker. Attacks continue to occur regularly, though less frequently in recent years as cyber criminals have shifted to other forms of ransomware.
Recent ransomware trends
While CryptoLocker rose to prominence in 2013, new ransomware families with enhanced capabilities have since emerged. Some current ransomware trends include:
Ransomware-as-a-Service (RaaS)
Developers lease or sell their ransomware code to “affiliates” who then carry out attacks. This model has enabled the rapid spread of ransomware.
Double extortion
In addition to encrypting files, ransomware gangs now also threaten to publish sensitive data stolen from victims who don’t pay the ransom.
High ransom demands
Recent strains like Ryuk and Sodinokibi routinely demand ransoms in the hundreds of thousands or millions of dollars from large organizations.
Sophisticated operations
Many ransomware groups run complex operations including customer service call centers for their victims. Some even publish blogs.
Targeted attacks
Instead of mass spam campaigns, many ransomware operators now hand pick targets and focus on gaining access to high value networks through careful social engineering.
Critical infrastructure targeting
Hospitals, transportation systems, utilities and other critical infrastructure are being targeted by ransomware operators looking to cause maximum impact.
While CryptoLocker itself is not as active today, the ransomware threat landscape continues to evolve. Organizations must remain vigilant and use layered defenses to detect and disrupt these attacks.
Conclusion
In summary, while CryptoLocker used strong encryption that is virtually unbreakable without the decryption keys, there are some preventative measures that can be taken to avoid infection, and automated backups provide the best path to recover encrypted files after an attack. Paying the ransom is risky with no guarantee of getting files decrypted, so should be carefully considered rather than immediately done. CryptoLocker was an early and major ransomware threat, but new families continue to emerge using more sophisticated techniques. Maintaining comprehensive security defenses and user awareness provide the best protection against ransomware attacks. Organizations should take steps to ensure proper incident response plans are in place in case they become a victim.