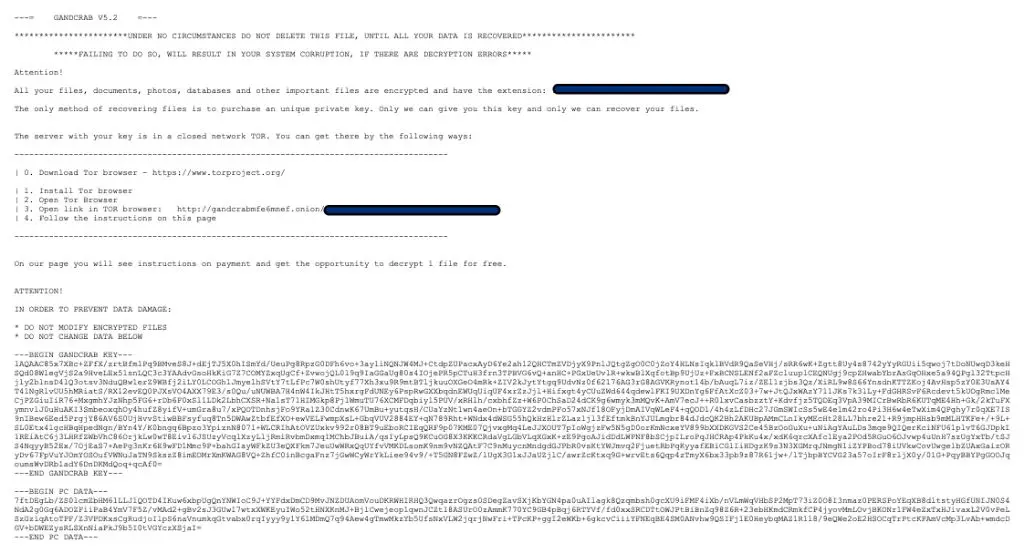
Ransomware attacks have become increasingly common in recent years. One of the most prolific ransomware strains is GandCrab, which first appeared in 2018. Victims of GandCrab find their files encrypted and a ransom demand placed on decrypting them. This raises an important question – is it possible to decrypt files encrypted by GandCrab without paying the ransom?
What is GandCrab?
GandCrab is a ransomware-as-a-service operated by a cybercriminal group. It functions by encrypting files on a victim’s computer and network drives using strong encryption algorithms. The hackers demand payment in cryptocurrency to provide the decryption key. Once installed, GandCrab encrypts a wide range of file types including:
- Documents
- Images
- Videos
- Audio files
- Archives
- Scripts
- Source code
GandCrab stands out for its affiliate model, where the authors sell the malware to other distributors for a cut of the profits. This model helped GandCrab proliferate widely. At its peak, damage estimates exceeded $2 billion.
Can GandCrab be decrypted without paying?
For most victims, decrypting GandCrab encrypted files without the hackers’ private key is impossible. GandCrab uses strong encryption algorithms, often AES and RSA 2048-bit keys. This makes brute forcing the encryption unviable.
However, there are some situations where decryption is possible:
1. Using a decryptor tool
Cybersecurity researchers have periodically developed free GandCrab decryption tools. These work by finding flaws in the malware’s encryption implementation. The tools are based on recovered private keys or coding errors.
Examples of GandCrab decryptors include tools by Ahnlab, McAfee, and Bitdefender. But these tools have limitations:
- Only old versions of GandCrab are affected
- Developers need access to many samples to extract keys
- Doesn’t work if custom settings are used
As GandCrab evolved, later versions patched these flaws, rendering the tools ineffective.
2. Finding the private key
Some victims have successfully located GandCrab’s private encryption keys on their systems. The malware needs to store the keys locally to encrypt files initially.
By thoroughly searching the infected system, it’s sometimes possible to find encrypted key files or trace how GandCrab saves them. This private key can then decrypt without paying the ransom.
3. Flaws in the infection process
In some cases, GandCrab failed to delete original files or missed encrypting certain files. This can happen if the infection gets interrupted or doesn’t propagate fully. Scouring the infected system for leftover unencrypted data can potentially recover some files.
4. Backups
Having offline, uninfected backups can fully decrypt GandCrab by restoring the original files. But many victims discover their backups are also corrupted or non-existent after an attack.
Steps to try decrypting GandCrab
If you’re hit with GandCrab, first isolate the infected system to prevent further damage. Avoid taking steps that could overwrite encrypted data. Then attempt the following decryption methods:
- Identify the GandCrab variant – Knowing the version will tell you if there’s an existing decryptor tool available.
- Thoroughly search for keys – Dig into files, registry, memory, and other locations the malware could have stored keys.
- Check for unencrypted files – Scour the system for files GandCrab missed or failed to delete, especially weird file extensions.
- Restore from backups – Clean backup images can restore files if available.
- Ask the hackers – Some victims have reportedly negotiated a lower ransom, but there are legal and ethical risks.
Unfortunately, most of these methods offer limited success against newer versions of GandCrab. But it’s still worth the attempt before considering paying the ransom.
Should I pay the GandCrab ransom?
Deciding whether to pay the ransom demand is a difficult decision:
Reasons to pay:
- Decryption is essentially guaranteed if you pay
- It may be less expensive than losing the data
- Criminals provide responsive customer service
Reasons not to pay:
- No guarantee you’ll get your data back
- Paying encourages more ransomware attacks
- Funds more criminal activity
- May be legally questionable
Unfortunately, there are reasonable arguments on both sides. It’s a complex decision that depends on your specific situation.
Steps to recover after decryption
If you’re successful in decrypting your files, celebrate briefly then focus on avoiding this in the future:
- Understand how the infection occurred – Thoroughly investigate the root cause so it can be addressed.
- Restore data from backups – If backups weren’t impacted, restore to return to normal.
- Improve security controls – Ransomware often succeeds due to security gaps. Improve defenses.
- Segment networks – Limit lateral movement through segmentation and access controls.
- Deploy new anti-malware tools – Traditional antivirus often fails on new threats. Deploy specialized anti-ransomware.
- Train staff – Human errors often enable ransomware. Better train staff to be the last line of defense.
- Test incident response – Practice and refine your response plan to improve recovery times.
With strong controls in place, you can minimize future ransomware risk.
How GandCrab operated
To understand how to decrypt GandCrab, it helps to know how it operated:
Distribution
GandCrab relied on various distribution methods:
- Exploit kits – Drive-by downloads bundled in hacked sites.
- Malvertising – Malicious ads used for direct installs.
- Email phishing – Infected email attachments.
- Remote desktop access – Brute force attacks on RDP.
- Other malware – Bundled with existing infections.
Once run, the user sees limited clues anything was installed.
Encryption process
The encryption process goes as follows:
- Generates RSA public-private key pair.
- Exports public key to infected system.
- Generates random 128-bit AES key for file encryption.
- Encrypts AES key with RSA public key.
- Enumerates files on local disks and mapped network drives.
- Encrypts files with AES algorithm.
- Adds .CRAB extension to encrypted files.
- Deletes originals leaving only encrypted files.
- Sends encryption keys to command and control server.
This complex process leverages multiple encryption layers for strong protection.
Ransom demands
Once files are encrypted, ransom notes are dropped on the desktop. This includes payment amounts and instructions:
- Demands payment in Dash or Bitcoin cryptocurrency.
- Threatens permanent data loss if unpaid after a deadline.
- Offers to decrypt one file for free as proof.
- In later versions, increased ransom based on system type.
If paid, criminals provide a decryptor tool. But filing for a decryptor is complex, with scant customer support.
Conclusion
Falling victim to GandCrab can be devastating with business critical data encrypted. Unfortunately, few options exist to decrypt without paying in most scenarios.
Your best options are trying availabe decryption tools, meticulously searching for keys left behind, or restoring from backups. But ultimately, preventing the infection in the first place through strong controls offers the best protection against GandCrab and other ransomware strains in the future.