Windows 10 does have some built-in protections against ransomware, but it does not have a complete built-in ransomware block. There are a few key features in Windows 10 that can help detect and prevent ransomware attacks:
Controlled Folder Access
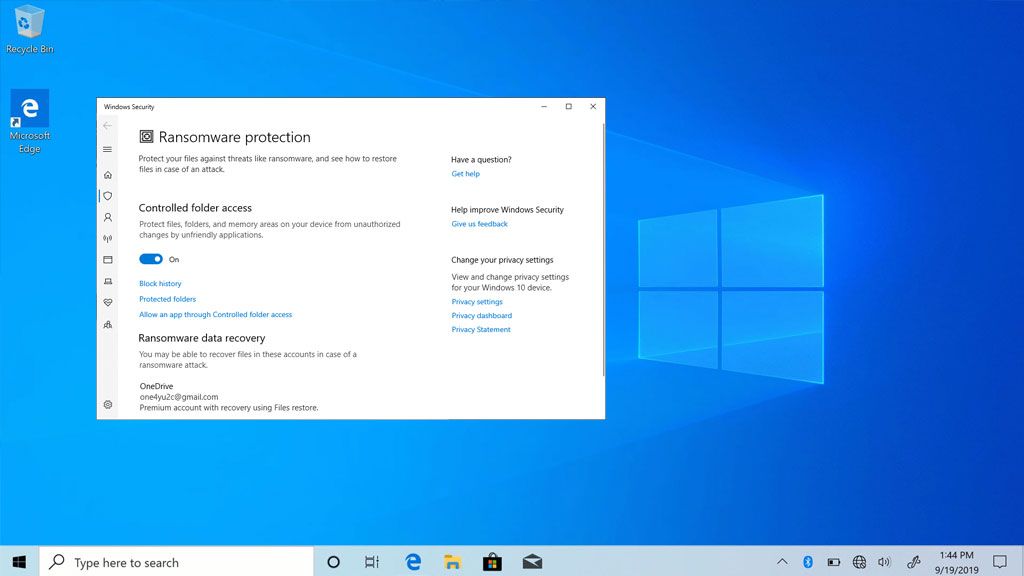
Controlled Folder Access is a feature that was introduced in the Windows 10 Fall Creators Update in 2017. It allows you to protect certain folders from unauthorized changes by apps and programs. This can prevent ransomware from being able to encrypt files in the protected folders.
To enable Controlled Folder Access:
- Open the Start menu and search for “Windows Security”
- Click on “Virus & threat protection”
- Under “Ransomware protection”, turn on “Controlled folder access”
You can then add folders you want to protect from unauthorized access. Common folders to protect include Documents, Pictures, Videos, Desktop, and OneDrive folders.
Windows Defender Antivirus
Windows 10 comes built-in with Windows Defender Antivirus software. Windows Defender can detect and block many types of malware including ransomware. It uses signatures, heuristics, and machine learning to identify ransomware.
Windows Defender is enabled by default in Windows 10. You can check its status by going to Settings > Update & Security > Windows Security > Virus & threat protection. Make sure that “Real-time protection” and “Cloud-delivered protection” are turned on for optimal protection.
While Windows Defender provides good baseline protection, it may not catch every new variant of ransomware out there. So you may want to combine it with another third-party antivirus software for maximum protection.
Microsoft Defender for Endpoint
For enterprise environments, Microsoft offers an advanced endpoint security product called Microsoft Defender for Endpoint (formerly known as Microsoft Defender Advanced Threat Protection).
Defender for Endpoint uses AI and machine learning to monitor for ransomware attacks across a company network. It can identify unusual data encryption activities that may indicate ransomware.
When ransomware is detected, Defender for Endpoint can contain the attack to prevent it from encrypting additional files. It also provides detailed reporting that can support investigation into a ransomware attack.
App & Browser Control
Windows 10 allows you to control which apps are allowed to launch and run in the background on a device. This can prevent untrusted apps like spam email attachments or downloads from running malicious code.
To manage app control settings:
- Go to Settings > Privacy & security > App permissions
- Toggle on/off access for features like background apps, call history, contacts, email, and other permissions
The Microsoft Edge browser also has tracking prevention features to block malicious websites and downloads that could deliver ransomware.
Ransomware Recovery
While the protections above focus on prevention, Windows 10 also has some recovery tools that can help if you do get hit with ransomware.
Windows 10 has Previous Versions functionality that allows you to restore older copies of files from File History backups. This can let you roll back files to before they were encrypted.
The File History feature needs to be enabled and set up ahead of time for this protection to work.
Other Windows ransomware protection features:
- Windows Security Center alerts for ransomware detection
- Windows Defender Offline scan to clean malware from outside the main OS
- Attack surface reduction rules to block ransomware execution and spread
- Network protection to block inbound ransomware activities
- Microsoft 365 E5 includes advanced ransomware detection and response tools
Does Windows 10 have a complete ransomware block?
Based on the protections outlined above, while Windows 10 has decent defenses, it does not have a complete foolproof ransomware block.
Reasons why Windows 10 lacks a full ransomware block include:
- Signatures can miss new ransomware variants
- AI/ML detection can have false negatives
- Some ransomware can disable or evade protections
- Powershell and macros used in attacks may bypass controls
- Requires proper configuration of protections
- Doesn’t protect against all attack vectors like social engineering
For guaranteed protection, a layered security approach is recommended. This can involve using third-party antivirus, firewalls, email security, backups, employee training, and network segmentation.
Ongoing vigilance is required as the ransomware threat landscape continues to rapidly evolve.
Key Features in Third-Party Ransomware Protection Tools
Here are some key features offered in leading third-party endpoint and ransomware protection platforms:
| Product | Key Features |
|---|---|
| Malwarebytes |
|
| Webroot |
|
| Acronis |
|
| Bitdefender |
|
Best Practices for Ransomware Prevention
Here are some top recommendations for organizations and users looking to avoid ransomware infections:
- Keep all software up-to-date, especially operating systems, browsers and plugins
- Be cautious of emails with attachments from unknown senders
- Avoid clicking on ads and pop-ups on disreputable websites
- Enable macro security settings in Microsoft Office
- Use ad blockers in web browsers to avoid malicious ads
- Disable Powershell in Windows if not required
- Back up data regularly and keep a recent backup offline
- Use virtualized environments for risky activities like web browsing
- Install a reputable antivirus solution and firewall
- Use data backup tools with versioning capability
- Control access to shared folders and limit write permissions
User education is also very important for recognizing potential ransomware attacks. Security awareness training can teach employees to identify warning signs such as phishing emails or unusual activity on their device.
What to Do If You Are Infected with Ransomware
If you encounter a ransomware infection, here are some steps to take:
- Disconnect infected devices from any network
- Use ransomware decryption tools to see if the strain can be decrypted
- Restore from clean backups if possible
- Check if shadow copies exist that can restore files
- Consult security experts for recovery options
- Wipe infected devices and reinstall software
- Pay the ransom only as a last resort
It is not recommended to pay ransoms unless absolutely necessary, as this encourages and funds criminal actors. The best approach is to restore from backups that were kept isolated and uninfected.
Conclusion
Windows 10 provides baseline defenses against ransomware through tools like Windows Defender, Controlled Folder Access and App control. However, it lacks a complete ransomware blocker and should be supplemented with additional security layers.
The most effective ransomware protection combines technology like anti-malware software with vigilant backups, training, access controls and segmentation. Preventing ransomware infections in the first place remains the top priority for individuals and organizations.