What is a denial of service attack?
A denial of service (DoS) attack is a cyber attack that aims to make a website or computer system unavailable to its intended users. The attackers flood the target with superfluous requests to overload the server and network infrastructure. As a result, legitimate requests cannot be processed, and the service becomes inaccessible.
DoS attacks are a serious threat to any organization with an online presence. They can cost a tremendous amount of money in terms of lost revenue, productivity, and reputation. According to a report by Cloudflare, DoS attacks cost businesses over $20 billion annually.
What are the different types of DoS attacks?
There are several techniques attackers use to execute denial of service attacks:
Volume-based attacks
These attacks aim to flood the network with traffic. Examples include:
– ICMP floods: The attacker overwhelms the victim with ICMP echo request (ping) packets. Each packet requires a response, eventually overloading network resources.
– UDP floods: The attacker sends a huge number of UDP packets to random ports on the victim system. The target system gets bogged down trying to determine which application is supposed to receive the UDP traffic.
– SYN floods: The attacker sends repeated SYN packets to a host to fill up the TCP connection queue from a spoofed IP address. This prevents legitimate users from establishing new connections.
Protocol attacks
These attacks target the protocol stack and resource allocation mechanisms. Examples include:
– Smurf attack: The attacker spoofs the victim’s IP address and broadcasts a large amount of ICMP echo traffic to the subnet broadcast address. This triggers all devices on the subnet to reply to the victim, overloading the system.
– Ping of Death: The attacker sends malformed or oversized ICMP packets that crash the target system when reassembling the ICMP packet fragments.
– SYN flood: Discussed earlier.
Application layer attacks
These attacks target application resources such as sockets, memory, CPU, and disk. Examples include:
– DNS amplification attack: The attacker spoofs the victim’s IP address and sends a DNS name lookup request to an open DNS server. The server responds with a much larger DNS record, swamping the victim’s network.
– Slowloris: The attacker opens multiple connections to the target web server but sends partial HTTP requests very slowly. This starves the server of resources for legitimate users.
– Zero-day DDoS attacks: These target unknown vulnerabilities in applications, allowing the attacker to crash services with a small number of requests.
Permanent DoS attacks
These are rare attacks that can destroy hardware and disable devices permanently. Examples include:
– Firmware attacks: Overwriting a device’s firmware and rendering it unusable.
– Light attacks: Shining bright lasers, microwaves or electromagnetic pulses to damage hardware.
– Voltage spikes: Causing power surges that fry circuitry.
How do denial of service attacks work?
To execute a successful DoS attack, the attacker follows these steps:
1. Identify a potential victim. The attacker may select targets based on political motives, financial incentives, personal vendetta, random selection or as a decoy.
2. Obtain control of an attack network. The attacker infects thousands of Internet-connected devices with malware to form a botnet. Each bot becomes a source of attack traffic.
3. Disguise the source of the attack. The attacker spoofs the IP address of the packets sent to the victim. This hides the location of the botnet and prevents blocking a single source.
4. Find a traffic amplification method. The attacker chooses an attack vector that maximizes the amount of traffic directed at the victim. DNS amplification, Smurf attacks and ping floods are common choices.
5. Launch the attack. The attacker sends malicious requests from across the botnet towards the victim in a coordinated barrage, overloading network capacity.
6. Repeat attack. Once the victim recovers, the attacker can repeat the attack in recurring waves that prevent full recovery. This extends the denial of service.
What are the impacts of a denial of service attack?
DoS attacks can severely disrupt business operations and cause major financial and productivity losses. Impacts include:
– Website unavailability – Customers cannot access the website to perform transactions or access services.
– Loss of sales & customers – Online transactions are disrupted, and customers may switch to competitors.
– Suspension of communications – Email, VoIP and other business systems are disabled.
– Productivity loss – Employees cannot perform tasks that rely on the affected IT systems and internet connectivity.
– Reputation damage – The company suffers embarrassment, loss of customer trust and negative publicity.
– Recovery costs – Considerable staff effort is required for server monitoring, implementing mitigations, public relations actions, and restoring affected systems.
According to Cloudflare, the average cost of infrastructure downtime from a DoS attack is over $100,000/hour. The more severe and prolonged the attack, the higher the costs incurred.
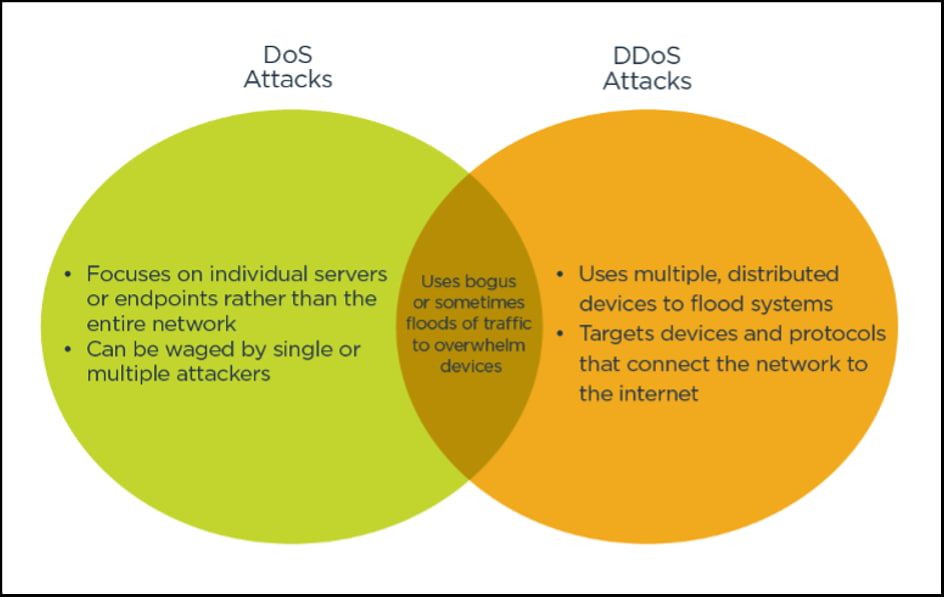
What is a DDoS attack?
A DDoS or distributed denial of service attack operates on the same principle as a DoS attack – overwhelm the target with traffic to make it unreachable. However, instead of using a single source, a DDoS attack uses multiple distributed sources of malicious traffic.
This offers the following advantages to attackers:
– Increased attack bandwidth – More devices means more traffic directed at the target, resulting in greater disruption.
– Harder to filter – Blocking a single IP has no effect when hundreds or thousands of bots are attacking simultaneously.
– Greater anonymity – The traffic comes from so many sources, it is difficult to identify the controlling botmaster.
– Access to more targets – A larger botnet allows DDoS attacks on a wider range of targets.
– Resilient threat – Taking down bots has limited impact as new bots can be recruited to replace them. The attack continues regardless.
DDos attacks represent the majority of DoS attack threats today due to the widespread availability of botnets for hire. Attackers can simply rent a botnet online and point it at their target.
What are common DDoS attack tools and methods?
Cybercriminals use a variety of methods and tools to carry out DDoS attacks:
Botnets
Botnets are the most common vehicle for DDoS attacks today. These consist of Internet-connected computers infected with malware that allows a remote attacker to control them. Typical infection methods include:
– Phishing emails with malware attachments
– Drive-by downloads from malicious websites
– Exploiting unpatched vulnerabilities
– Default or stolen login credentials
Major DDoS botnets today include Meris and Mēris. These leverage security flaws in routers, IP cameras and other Internet of Things (IoT) devices.
Stresser/Booter services
These services provide on-demand DDoS attack capabilities for a fee, allowing anyone to rent a botnet for launching attacks. Customers specify the target, attack method, bandwidth and duration. Prices range from $10 to $1000 per attack.
Popular stresser services include Bootyou, Netbooter and HULK Stresser. Law enforcement efforts have shut down some services, but new ones constantly emerge.
DDoS tools
Hacker tools like LOIC (Low Orbit Ion Cannon) allow launching DDoS attacks directly from a compromised computer. But the limited traffic makes standalone tools ineffective vs. botnets. However, they are sometimes used to supplement botnet attacks.
Popular DDoS tools include HOIC, DDOSIM, DRSYN and MR. DOS. Usage often represents inexperienced, “recreational” attackers rather than serious cybercriminals.
Weaponized spyware/malware
Some spyware and remote access trojans have distributed denial of service capabilities built-in, allowing cybercriminals to manipulate large numbers of infected machines for DDoS attacks.
Examples include njRAT, Xtreme RAT, SpyEye and Zeus P2P which have all been used to power botnet-driven DDoS attacks.
Who carries out denial of service attacks?
There are various motivations behind DoS and DDoS attacks, which helps categorize the attackers:
Hacktivists
Hacker activist groups wage cyber warfare for political or social reasons. Anonymous is notorious for DDoS attacks on government, corporate and religious organization websites. Groups like Lizard Squad have similarly targeted gaming networks.
Publicity is often a goal, meaning hacktivist attacks are announced online for maximum exposure and embarrassment of the victim.
Cybercriminals
Profit-seeking cybercriminals use DDoS as a means to an end – extortion. By overwhelming critical e-commerce or financial systems, the attackers can demand large ransoms to stop the attacks. Reported payouts range from $40,000 to $650,000.
Ransom DDoS is a lucrative criminal enterprise, with threat actors offering DDoS services or collaborating in layered “ransomware + DDoS” campaigns.
State actors
Nation-states weaponize DDoS capabilities for conducting cyber warfare and espionage against foreign governments. DDoS disrupts operations, facilitates data theft and also provides cover for more stealthy attacks.
China, Russia, Iran and North Korea actively develop cyber warfare techniques including DDoS. Attacks are rarely claimed by government agencies.
Insiders
Current or former employees and contractors represent an internal DDoS threat. Access to internal systems offers knowledge of vulnerabilities that could enable denial of service scenarios.
Like state actors, insider DDoS attackers are difficult to identify. But analysts suspect some major service outages to be insider sabotage rather than purely external attacks.
Thrill seekers
A class of unsophisticated recreational attackers simply DDoS websites and networks for fun, curiosity or boasting rights. Lizard Squad’s attacks on Xbox Live and PlayStation fall into this category.
These attackers often announce their attacks publicly. But the small scale limits the damage, and their lack of finances rules out sustained campaigns.
What are common DDoS attack targets?
Though any internet-connected system is vulnerable, some organizations face a higher risk of being DDoS targets due to the mission-critical nature of their online operations:
E-commerce companies
Online retailers rely completely on website availability for sales. A DDoS attack can cost millions per hour in lost transactions, especially during peak seasons like Cyber Monday.
Banks & financial institutions
Banks need 24/7 public access to banking applications which are mission-critical for transactions. DDoS disruptions even for minutes can affect client relationships, revenues and market reputation.
Gaming servers
Gaming companies like Xbox, PlayStation and Steam provide convenient targets for hacktivists seeking publicity by disrupting popular online services.
Cloud services
Amazon AWS, Microsoft Azure and other cloud providers power thousands of websites and services. A DDoS incident can cause collateral damage for all their hosted clients.
Government agencies
Critical public services like tax filing, passport applications and civil administration portals are frequent DDoS victims, often as collateral damage from hacktivist campaigns.
Media companies
News, social media and entertainment websites are prime targets for hacktivists and nation-state actors motivated to suppress or manipulate information.
DNS services
A successful attack on a top-level domain name server or popular DNS provider like DynDNS can take down thousands of companies simultaneously.
How can businesses defend against DDoS attacks?
A multi-layer DDoS defense strategy is key. Tried and tested protecting measures include:
Overprovision bandwidth
Maintain surplus capacity to absorb traffic floods without slowdown. But this can get costly, and large DDoS attacks can overwhelm any fixed capacity.
Cloud-based DDoS mitigation
Route all traffic through cloud scrubbing centers that filter DDoS traffic before it hits your data center. Service providers like Cloudflare absorb and dissipate attacks upstream.
Blackhole suspect traffic
Routers detect and block known attack vectors like SYN floods through protocol analysis before traffic accumulates. But blackholing also blocks legitimate user traffic.
Rate limiting
Limit total connections and new connections per second from any IP to contain attacks from spoofing sources. But legitimate users can also suffer denied access.
Keep software updated
Attackers exploit known software flaws, so prompt security patching closes doors. But zero-day attacks can still succeed.
Have an emergency response plan
Document steps for attack response like contacting providers, rerouting traffic and crisis communications. Practice drills to refine procedures and decision making.
A blend of these strategies can provide strong DDoS protection. But continuous monitoring and improvement is vital to counter the evolving DDoS threat.
Conclusion
Denial of service attacks present an ever-growing threat landscape as attackers leverage larger botnets, better tools and new techniques. With DDoS-for-hire, anyone can now wage attacks for a small fee.
To manage risk, organizations must take a defense-in-depth approach using on-premise and cloud-based systems. Prompt incident response and public communication are crucial for minimizing disruption. As DDoS evolves into a potent cyber weapon, developing resilience against attacks becomes an imperative.