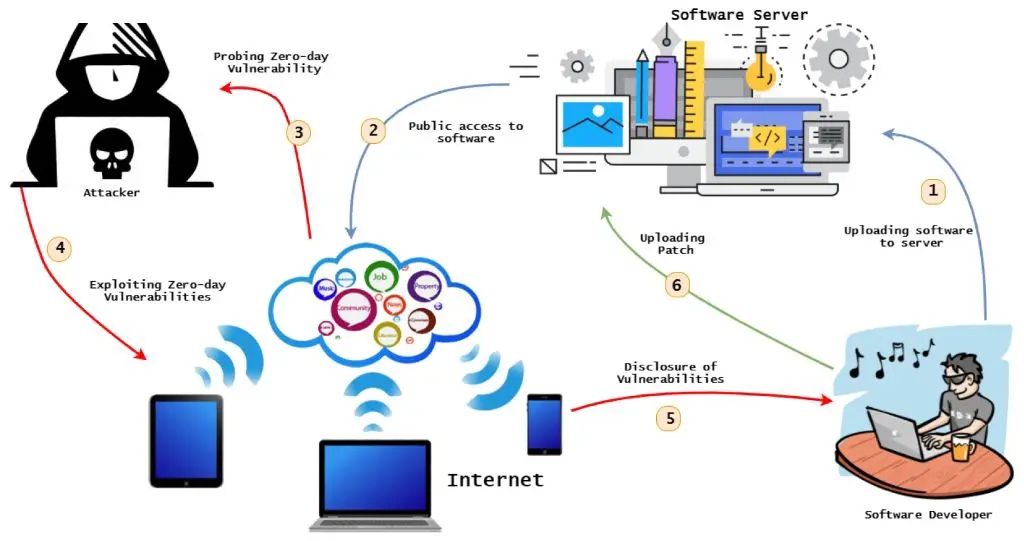
Zero-day attacks refer to cyber attacks that exploit previously unknown software vulnerabilities. Since the vulnerabilities are unknown to the software vendor, there are no patches available to mitigate the attacks. This makes zero-day attacks difficult to defend against. However, there are steps organizations can take to reduce their risk and minimize potential damage from zero-day attacks.
What are zero-day attacks?
A zero-day attack exploits a previously unknown vulnerability in software, firmware, or hardware. The term “zero-day” refers to the fact that the vulnerability is not publicly known prior to the attack. As a result, the software vendor has had zero days to address the vulnerability by releasing a patch or fix.
Zero-day vulnerabilities are valuable to cyber attackers because they can use them to compromise target systems before defenses are in place. In many cases, vendors are unaware of zero-day vulnerabilities that exist in their products until the vulnerabilities are exploited in the wild.
Some key characteristics of zero-day attacks include:
- Exploitation of unknown vulnerabilities
- No patches or fixes available from vendors
- Difficult to defend against proactively
- Can provide full control of target systems if successfully exploited
Zero-day attacks can pose serious threats to organizations since traditional security tools are not capable of detecting or defending against unknown vulnerabilities. This makes it crucial for organizations to take proactive steps to identify and mitigate potential zero-day attack vectors.
How are zero-day vulnerabilities discovered?
There are several ways that zero-day vulnerabilities are discovered, including:
- Internal research: Software vendors and security researchers actively analyze code and systems looking for potential flaws and bugs that could lead to vulnerabilities.
- External research: Security researchers outside of vendor organizations also analyze systems and software for vulnerabilities. Many choose to responsibly disclose discovered flaws to vendors.
- Hacking communities: Vulnerabilities are discussed and traded among hacking groups or sold on dark web marketplaces.
- Reverse engineering: Analyzing compiled software code to uncover programming flaws that could lead to exploits.
- Fuzzing: Using automated testing tools to bombard systems with random data to uncover vulnerabilities.
Once vulnerabilities are discovered, if responsible disclosure practices are followed, they are reported to the vendor for remediation before being publicly announced. However, some entities sell or leak details about zero-days to others with malicious intent.
What are common zero-day attack vectors?
Some of the most common vectors exploited in zero-day attacks include:
- Software vulnerabilities: Security flaws in software applications, operating systems, firmware, and other code can all be exploited as zero-days before patches are available.
- Web browsers and plugins: Browsers are a major target, as browser-based exploits can enable attacks against a broad range of users and systems.
- Email attachments: Malicious files attached to phishing emails allow attackers to exploit vulnerabilities when attachments are opened by users.
- Document files: Vulnerabilities in programs like Microsoft Office or PDF readers can be leveraged via malicious documents.
- Network devices: Bugs in routers, firewalls, VPNs, and other networking hardware can also be valuable zero-day targets.
Staying up-to-date with patching and avoiding unnecessary exposure are key to reducing attack surface for many vectors. For email and documents, security awareness training helps mitigate social engineering risks.
Major historical zero-day attacks
Some significant cyber attacks that leveraged zero-day exploits include:
| Attack | Date | Impact |
|---|---|---|
| WannaCry ransomware | 2017 | Over 200,000 systems infected globally, damages over $4 billion |
| Adobe Flash zero-day | 2015 | Attackers able to remotely compromise Windows and Linux systems |
| Baltimore ransomware | 2019 | City services crippled for weeks after attack, $18 million recovery costs |
| Internet Explorer zero-day | 2014 | Allows remote code execution on vulnerable Windows systems |
These and other high-profile attacks demonstrate the serious disruption zero-days can cause if successfully exploited in the wild.
How can organizations defend against zero-day attacks?
Defending against zero-day attacks presents significant challenges since the vulnerabilities are unknown. However, organizations can take steps to reduce risks and minimize potential impact, including:
- Patch rapidly: Have processes to test and deploy applicable patches as soon as they become available.
- Harden systems: Disable unnecessary functionality, ports, users to reduce attack surface.
- Segment networks: Limit lateral movement after breaches by isolating systems and using DMZs.
- Monitor traffic: Analyze inbound and outbound traffic for signs of compromise or malicious activity.
- Filter web/email content: Block suspicious file types, URLs, attachments, and links.
- Train users: Education on secure practices, identifying social engineering reduces human vector risks.
- Backups: Maintain usable, offline backups to support recovery processes if compromised.
- Emergency response plan: Incident response, crises communications plans can limit damage in case of breaches.
Combining traditional security tools with human-centric defenses provides defense-in-depth against many attack vectors, including zero-days.
Should organizations pay “bug bounties”?
Many major software vendors, including Google, Apple, Microsoft, and Facebook, offer monetary rewards through bug bounty programs to security researchers who discover and responsibly disclose vulnerabilities in their products.
Paying bug bounties can benefit vendors by:
- Incentivizing researchers to report flaws directly instead of selling or exploiting them
- Gaining early visibility into vulnerabilities before they are exploited
- Building relationships with security researcher community
- Demonstrating commitment to security to customers
However, some argue that bug bounties also have potential downsides, such as:
- May encourage researchers/hackers to find more flaws rather than secure code
- Rewards could motivate malicious actors if amounts are substantial
- Companies may come to rely on outsiders for QA and security testing
- Profit motives could discourage responsible disclosure practices
Overall, used carefully, bug bounties are generally seen as a net positive – rewarding security contributions while supplying vendors with actionable data to secure products.
Should vulnerabilities be responsibly disclosed?
Responsible disclosure practices aim to provide transparency about vulnerabilities to affected vendors and users while giving vendors time to develop fixes before details become public knowledge.
Potential benefits of responsible disclosure include:
- Vendors have time to develop patches before exploits occur
- Users receive actionable information to secure themselves
- Researchers get credit for discoveries motivating future work
- Awareness brings attention/resources to resolve issues
- More orderly process than unrestricted disclosure
However, some critics argue that full disclosure of vulnerabilities as soon as they are discovered forces vendors to act more quickly. Others maintain that disclosure should be limited to prevent adversaries from benefiting.
Most experts favor responsible disclosure that balances warning vendors, users, and the public in a reasonable timeframe. Disclosure practices should generally:
- Allow reasonable time for patching based on risk
- Credit discoverers for their work
- Provide actionable details to users once patched
- Work cooperatively with vendors for smooth process
With responsible disclosures, vendors have time to resolve issues before exploits occur in the wild.
Should governments stockpile vulnerabilities?
Some government agencies, such as the US NSA and British GCHQ, are known to stockpile vulnerabilities to use for national security-related surveillance and exploits. However, this stockpiling is controversial for several reasons:
Potential risks of government vulnerability stockpiling:
- Hoarded vulnerabilities could be leaked and exploited by adversaries
- May use for questionable monitoring of domestic targets
- Discourages reporting vulnerabilities to vendors for fixing
- Vulnerable systems remain at risk from other malicious actors
- Undermines vendor relationships and security efforts
Those in favor argue that:
- Critical for gathering intelligence about legitimate targets
- Vulnerabilities unlikely to be discovered otherwise
- Can provide leverage over adversaries using same vulnerabilities
- Some disclosure allowed after intelligence value diminished
In general, non-governmental security experts oppose the stockpiling practice except for narrow espionage applications against advisories. Responsible disclosure that resolves vulnerabilities for all users is widely favored.
Should white hat hacking be encouraged?
White hat hackers are security researchers who hack into systems without malicious intent. Their goals are to discover vulnerabilities and bring awareness in order to improve security.
Potential benefits of ethical white hat hacking include:
- Finds unknown flaws that can be fixed
- Tests effectiveness of defenses
- Demonstrates real-world methods of attackers
- Motivates proactive security improvements
- Rewards help grow community of skilled researchers
However, risks such as accidentally disrupting systems are present. Rules of engagement, authorization, and responsible disclosure minimize downsides.
Most experts believe white hat hacking plays a vital role in cyber security when practiced ethically. Encouraging white hat hacking helps discover vulnerabilities before malicious actors exploit them. Ongoing innovation and care are still needed though to ensure safety.
Overall, white hat hacking is a valuable component of an effective vulnerability management program. But it requires appropriate oversight and responsible disclosure.
Conclusion
Zero-day attacks remain a serious threat given the near impossibility of completely eliminating exploitable flaws from complex, evolving software. Proactive processes to discover vulnerabilities before malicious actors, rapid patching, reducing attack surfaces, training personnel, and effective monitoring help reduce risks. Responsible disclosure and leveraging contributions from white hat security researchers are also key elements of a maturing security posture. While zero-days cannot be eliminated entirely, their disruptive impacts can be minimized through defense-in-depth and focusing on resilience. Ongoing innovation in technology and processes will help make zero-day attacks increasingly rare and manageable.