What is encryption and decryption?
Encryption is the process of encoding data or information in such a way that only authorized parties can access it. Decryption is the reverse process of converting encrypted data back into its original, readable form. The use of encryption/decryption has been traced back to 1900 BC in Egypt. One of the earliest records of encryption was the Caesar cipher used by Julius Caesar to communicate with his generals. encryption ensures data security when stored digitally or transmitted over networks.
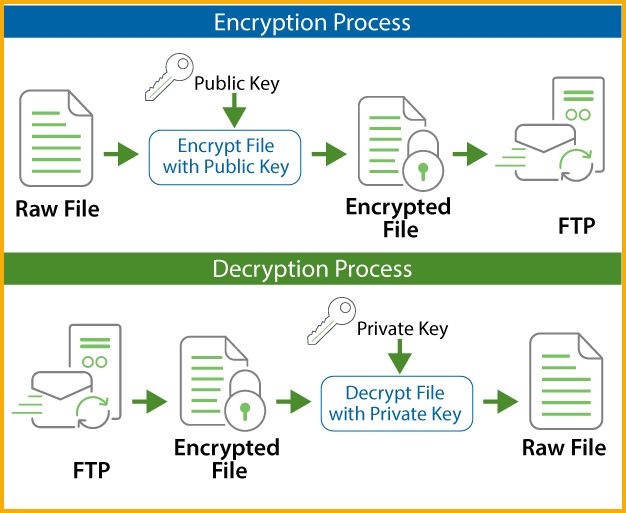
Modern encryption is based on cryptographic algorithms that use mathematical techniques to scramble data into an unreadable format called ciphertext. The intended recipient must have the right encryption key to decrypt the ciphertext back into plaintext. There are two main types of encryption: symmetric-key encryption uses the same key to encrypt and decrypt data, while public-key encryption uses a public key to encrypt and a private key to decrypt.
Some commonly used encryption algorithms include AES, RSA, and Blowfish. Encryption is widely used today in technologies like SSL/TLS, VPNs, cryptocurrencies, and messaging apps.
Sources:
History of cryptography – Wikipedia
A brief history of encryption – Thales
Why files get encrypted
Files often get encrypted for several important reasons:
To protect against ransomware attacks. Ransomware is a type of malware that encrypts files on a device and demands payment for decryption. Encrypting files makes it harder for ransomware to render files inaccessible.
To keep sensitive data private and secure, like financial records or personal information. Encryption transforms data into unreadable ciphertext so that unauthorized users cannot access the contents if files are intercepted. As noted in this article, encrypted file sharing helps prevent data breaches and cyber attacks.
To comply with data protection laws and industry regulations. Regulations like HIPAA and GDPR require encryption of personal data like medical records or customer information. Encryption enables organizations to securely store regulated data and avoid violations, as explained here.
Types of encryption algorithms
Encryption algorithms generally fall into two categories: symmetric encryption and asymmetric encryption. Both types are commonly used to encrypt files and data.
Symmetric encryption algorithms use the same cryptographic key for both encrypting and decrypting data. Some common examples include AES, DES, 3DES, Blowfish, Twofish, and RC4. Symmetric algorithms tend to be faster and are used to encrypt large amounts of data. However, the main downside is that the sender and recipient need access to the same secret key which presents a key distribution challenge.
Asymmetric encryption algorithms use a public-private key pair for encryption and decryption. The public key is used to encrypt data while only the paired private key can decrypt it. Prominent asymmetric algorithms include RSA, ECC (Elliptic Curve Cryptography), and Diffie-Hellman key exchange. The advantage of asymmetric encryption is solved key distribution since the public key can be widely distributed without compromising security. However, asymmetric encryption tends to be slower than symmetric encryption.
Where Encryption Keys are Stored
Encryption keys need to be stored securely and protected from unauthorized access. There are several common methods for storing encryption keys:
Key Databases – Keys can be stored in secure databases or key management systems. These provide centralized storage and lifecycle management of keys. According to the NIST Guide to Storage Encryption Technologies, “A well-designed key management system greatly enhances the security of a cryptosystem by centralizing key generation, storage, distribution, and replacement.”[1]
Hardware Security Modules (HSMs) – HSMs are physical devices that provide secure generation, storage and usage of encryption keys. Keys are stored in tamper-resistant hardware and protected by access controls. HSMs allow applications to use encryption while keeping the keys securely isolated. As per the OWASP Key Management Cheat Sheet, “If you are planning on storing keys in offline devices/databases, then encrypt the keys using Key Encryption Keys (KEKs) prior to the export of the key material.”[2]
Password Managers – Password managers provide secure encrypted storage of passwords, keys, and other sensitive information. The data is encrypted and decrypted using a master password or key known only to the authorized user. Leading password managers use zero-knowledge architecture so the service provider cannot access the encrypted data.
How to Decrypt a File
The first step in decrypting an encrypted file is obtaining the correct decryption key. Encryption keys are usually generated when the file is first encrypted and can be derived from a password or passphrase. Without the proper key, it is essentially impossible to decrypt the file (source: https://www.microsoft.com/en-us/windows/learning-center/decrypt-files).
Once you have the encryption key, you will need to use the appropriate decryption software or tools. Windows 10 has built-in utilities like the Certificate Manager that can decrypt files encrypted with certificates or public keys. For other types of encryption, you may need to use third party software like VeraCrypt or GPG (source: https://www.makeuseof.com/windows-10-ways-to-decrypt-files/).
If you forgot the password used to encrypt a file or are dealing with ransomware, there are decryption options available. Password recovery tools like Passware can crack encryption by brute forcing all possible passwords. For ransomware, some security companies release free decryption keys that can decrypt files without paying the ransom (source: https://www.microsoft.com/en-us/windows/learning-center/decrypt-files).
Decryption software options
There are a few built-in decryption tools provided by operating systems as well as third party decryption software that can help decrypt encrypted files.
Windows
Windows includes the Encrypting File System (EFS) to encrypt files and folders. To decrypt EFS-encrypted files on Windows, you can use the Certificate Manager tool. Just right-click on the encrypted file, select Properties, click Advanced and then select Decrypt contents to secure data. The decryption key is tied to your Windows account so you will need to log into the same account used to encrypt the files [1].
Mac OS
On Mac OS, you can right-click on an encrypted file and select Decrypt to access the file contents using your user account login keychain. The FileVault encryption system used by Mac OS X also enables decryption via account password [2].
Linux
Linux distributions like Ubuntu provide the Built-in GnuPG encryption/decryption tool which can decrypt files if you have the correct private key for that file [3].
Third Party Decryption Tools
Some popular third party decryption tools include:
– Emsisoft Decrypter – offers a free decryption tool for many ransomware variants.
– Avast Decryption Tools – provides free ransomware decryption tools for certain strains.
– Kaspersky Ransomware Decryptor – can decrypt some forms of ransomware infection for free.
These tools leverage databases of ransomware signatures, behavior patterns, and encryption keys contributed by security researchers to enable decryption capabilities. However, newer ransomware variants may not yet have decryptors available.
Recovering lost or forgotten keys
If you lose or forget the encryption key for a file or drive, there are several options for trying to recover access:
Password recovery tools like Passware Kit Forensic [1] can help recover passwords and encryption keys in some cases by analyzing encrypted data and metadata.
Brute force attacks may work for weaker encryption by systematically trying all possible passwords and passphrases. But this becomes infeasible for stronger 256-bit or higher encryption.
Some operating systems and third party services use key escrow to keep a copy of encryption keys for recovery purposes. For example, Stanford University has a self-service [2] to retrieve lost BitLocker keys.
If the encrypted data is very important, you may need to consult a professional forensic data recovery service. But they tend to charge high fees with no guarantee of decryption.
Unfortunately, if you used strong encryption and don’t have the key, decryption may not be possible by any practical means.
Alternatives if Decryption is Not Possible
If you are unable to decrypt your files using the encryption key or recovery software, there are a few options left:
File Recovery from Backup
If you have a recent backup of your files from before they were encrypted, you may be able to restore your data from backup. Having regular backups is the best defense against ransomware attacks. If you use cloud backups, disconnect the storage from your system before attempting any decryption to avoid the backup files from getting encrypted as well. Make sure the backup is from a version before any encryption took place.
Negotiate with Ransomware Attackers
Some ransomware schemes provide an option to negotiate with the attackers by communicating through their provided website or emails. There is no guarantee this will work, and it gives money to criminals, but it is an option as a last resort to recover critical files. Always proceed cautiously when dealing with cybercriminals.
Accept Data Loss
If unable to decrypt and backups aren’t available, you may have to accept permanent data loss. Attempting decryption through unverified methods could make files unrecoverable. You can try formatting the drive and reinstalling the OS if the data is not critical. For personal files, they may be gone for good without the decryption key.
Best practices to avoid encryption problems
To avoid issues with losing access to encrypted data, it is important to follow best practices around key and data management:
Backup keys and data – Be sure to keep backup copies of encryption keys as well as the encrypted data itself. Store these backups in a safe, secure location in case you lose access to the originals. Some options are to store backups on an external hard drive or cloud storage. Just be sure to protect backup copies with strong passwords or encryption.
Escrow keys with trusted provider – Many companies offer key escrow services where they securely store copies of customers’ encryption keys. This provides a backup if keys are lost or unavailable. When choosing a key escrow provider, be sure they are reputable, use strong security practices, and allow access to keys only under certain approved conditions.[1]
Use encryption judiciously – While encryption provides important data security, overusing it can lead to situations where you encrypt things unnecessarily. Avoid encrypting backup files, low-risk data, or items needed for daily work. Develop policies on what data absolutely must be encrypted versus what can remain unencrypted.[2]
Summary
In summary, encryption is used to protect and secure files by scrambling the contents so they cannot be read without the proper decryption key. There are many different encryption algorithms, with AES and RSA being common standards today. Encryption keys are usually stored separately from the encrypted files, either in a designated key management system or sometimes embedded within the file metadata.
To decrypt a file, you need access to the original encryption key or password. Specialized decryption software can automate the process if you have the proper key. If the key is lost, recovery options are limited but may include using password cracking tools or contacting the encryption provider. Ultimately, not having the key may make decryption impossible.
The best practice is to proactively plan your encryption and decryption needs. Store keys securely, use key management tools, and have contingency plans to prevent losing access to encrypted data. With the right preparation, decryption does not need to be a significant hurdle.