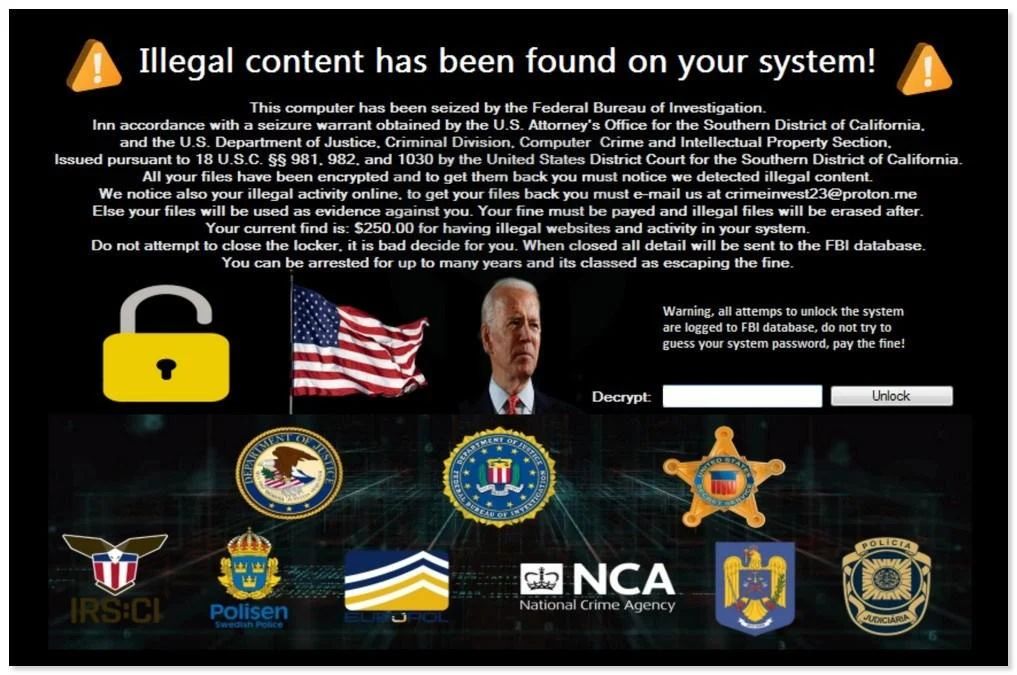
Ransomware is a form of malicious software that encrypts files on a device and demands payment in order to decrypt them. FBI ransomware is a specific type of ransomware that pretends to be from the FBI and accuses the victim of illegal activities. Getting rid of FBI ransomware can be challenging, but is possible with the right approach.
What is FBI ransomware?
FBI ransomware is a type of malware that locks access to a computer or mobile device and displays a message claiming to be from the FBI. This message accuses the user of illegal activities, such as viewing child pornography or distributing copyrighted material online. The message demands that the user pay a “fine” in the form of a ransomware payment to unlock their device.
This is a scare tactic used to extort money from victims. The ransomware is not actually from the FBI – it is distributed and operated by cybercriminals. The threats of legal action or imprisonment are fraudulent.
How does FBI ransomware infect my device?
FBI ransomware is often distributed through spam email campaigns, malicious advertisements, fake software updates, infected external drives, and illegal streaming or torrent websites. Once installed, it will encrypt personal files on the infected device and make them inaccessible.
Some common infection methods include:
- Opening email attachments or clicking links in spam emails
- Visiting compromised websites that trigger a download
- Clicking on malicious ads or pop-ups
- Installing “cracked” or pirated software
- Plugging in an infected USB flash drive
- Downloading files from unsafe sources
What happens when infected with FBI ransomware?
Once installed, FBI ransomware will scan your device for files to encrypt. It targets documents, photos, videos, databases and other important file types. The ransomware encrypts the files using complex algorithms so they cannot be accessed without the decryption key.
It will then display a fake FBI message accusing you of illegal cyber activity and demanding payment to decrypt the files. The message is designed to scare victims into paying quickly. It threatens criminal charges, imprisonment, and other legal consequences if the ransom is not paid.
The ransom demand is usually for payment in cryptocurrencies like Bitcoin because they are difficult to trace. The ransom amount varies but is often hundreds or thousands of dollars worth of cryptocurrency.
Should I pay the FBI ransomware ransom?
No, you should never pay the ransom demand. The cybercriminals operating the ransomware cannot actually take legal action against you. Paying the ransom simply funds their illegal operation and encourages more attacks. There is also no guarantee your files will be recovered after payment.
Some key reasons not to pay the ransom include:
- Your money funds more ransomware campaigns
- There is no guarantee you’ll get decryption keys
- You may be targeted again by the same group
- It encourages more ransomware attacks globally
- The criminals cannot legally enforce their threats
How can I remove FBI ransomware from my device?
Removing FBI ransomware requires a combination of malware scanning, system restores, decryption tools and other methods. The exact approach depends on the variant. Here are some steps to take:
- Disconnect from the internet – This prevents remote communication with command servers
- Boot into Safe Mode – Starts Windows with only essential programs and services
- Run anti-malware scans – Use programs like Malwarebytes to detect and remove infections
- Delete associated files – Manually delete any suspicious files, folders or registry entries
- Restore from backup – Rollback to an uninfected system image if available
- Use decryption tools – Some ransomware variants have free decryption tools available
- Recover files from Shadow Copies – Use Windows Previous Versions to restore individual files
In some cases, the ransomware is too complex to fully remove. You may need to wipe the system and reinstall the OS to completely eliminate it.
How can I get my encrypted files back without paying?
There are a few methods that may work to restore encrypted files without paying the ransom:
- Use ransomware decryption tools – Check sites like NoMoreRansom.org for free decryptors when available.
- Restore from backups – Clean backups made before infection let you recover files.
- Try third party decryption – Some security firms offer ransomware decryption services.
- Extract files from Shadow Copies – Windows may have file snapshots stored you can restore from.
However, if the ransomware utilizes strong encryption these options likely will not work. Damage from complex ransomware variants can be difficult or impossible to reverse without the encryption keys.
How can I protect myself from FBI ransomware?
You can avoid FBI ransomware and other threats by taking proactive security measures:
- Install anti-malware software and keep it updated
- Be extremely cautious of emails from unknown senders
- Avoid clicking links or attachments in unsolicited emails
- Backup important data regularly
- Use caution with downloads and avoid illegal software
- Keep all systems and software fully updated
- Turn off macros in Microsoft Office
- Use ad and script blocking browser extensions
- Use firewalls to limit exposure to malicious traffic
Cybersecurity awareness training can also teach you how to identify and avoid ransomware threats before they can infect your system.
What should I do if infected with FBI ransomware?
If you become infected with FBI ransomware, follow these steps:
- Isolate the infected device – Unplug from network to prevent spread
- Take screenshots – Document the ransom message and demands
- Check for decryptors – Search for free decryption tools for the variant
- Restore files from backup – Rollback to clean versions you have saved
- Scan with anti-malware software – Run a thorough scan to locate and remove infections
- Reset passwords – Change passwords for all accounts accessed on infected device
- Contact authorities – Report the attack to law enforcement and cybersecurity professionals
Do not communicate with the attackers, pay ransoms or click anything within pop-up ransomware screens. Removing the infection should be priority before permanent damage is done.
Can I decrypt my files without the encryption key?
It is very difficult to decrypt files encrypted by ransomware without access to the encryption keys. Ransomware uses complex asymmetric encryption algorithms that require the private key to reverse.
However, there are some cases where files can be recovered without decryption:
- If you have unencrypted backups or file snapshots, you can restore from these
- Some ransomware is poorly implemented and scrambles rather than encrypts files. You may be able to restore scrambled files using data recovery tools.
- If the ransomware encrypts file names and metadata but not the data sections, the files can be restored.
- Some security firms can crack weaker encryption used by older ransomware variants.
But modern ransomware uses military-grade encryption making direct decryption without keys extremely difficult. Preventing the attack is better than trying to decrypt after the fact.
Should I reformat my computer if infected?
Reformatting and reinstalling your operating system is an option if you cannot fully remove an FBI ransomware infection through other means. However, it should only be done as a last resort.
Potential downsides of reformatting include:
- It will wipe out all files stored on the system, not just encrypted ones.
- You will need to reinstall all programs, applications and operating system.
- Valuable files may be lost if backups are not available.
- It can be a time consuming process.
If anti-malware scans, system restores and other methods cannot clean the ransomware, then reformatting may be your only option. Make sure to backup any important files you may need before taking this step.
Should I report FBI ransomware to law enforcement?
You should report any FBI ransomware attack or infection to law enforcement, specifically the FBI Cyber Crime division. Even if you resolved the infection yourself, reporting helps provide information that can assist investigations and cyber crime prevention efforts.
Contact information to report FBI ransomware:
- FBI Cyber Division: www.fbi.gov/contact-us/field-offices
- Internet Crime Complaint Center: www.ic3.gov
Make sure to include all relevant details such as how you were infected, ransom amounts, ransom note screenshots, bitcoin wallets, and specific variant details. Your report helps build cases against ransomware operators.
Whatcrimes am I accused of in FBI ransomware?
FBI ransomware accuses victims of serious cybercrimes to scare individuals into paying. Some common false accusations include:
- Possession or distribution of child sexual abuse material
- Download or sharing copyright protected content (movies, music, books)
- Computer hacking crimes
- Financial fraud crimes
- Terrorism or extremism charges
- Distributing classified or illegal pornography
The ransomware displays fake wanted posters, legal notices, law enforcement emblems and other content to make the accusations seem real. However, the accusations are completely fraudulent. Do not take them seriously or panic.
The ransom note is authored by the cybercriminals operating the ransomware, not legitimate law enforcement. Any threats of fines, imprisonment or other legal consequences for not paying are also fraudulent.
Can the FBI directly decrypt files?
The FBI does not have backdoor keys or ways to directly decrypt files locked by ransomware, even in cases where the ransomware claims to be the FBI. Sophisticated ransomware uses cryptographic encryption algorithms that require the private key to decrypt.
If the FBI obtains the private keys through criminal investigations of ransomware operations, then they may be able to release them to victims for file recovery. Otherwise, direct decryption requires cooperation of the ransomware developers themselves. Do not count on the FBI or law enforcement directly decrypting ransomware.
The most reliable ways to recover encrypted files are:
- Restoring from clean backups
- Using ransomware decryption tools when available
- Hiring data recovery firms in some cases
Rather than relying on law enforcement decryption, individuals and organizations should take preventative measures to avoid ransomware attacks before they occur.
Can I be arrested or go to jail for not paying FBI ransomware?
You cannot be arrested or criminally charged for not paying ransomware demands, even when accompanied by threats from groups claiming to be law enforcement. The FBI ransomware warnings of prosecution, lawsuits, or imprisonment for non-payment are completely fake.
Refusing to pay ransomware is perfectly legal. Groups distributing ransomware operate as for-profit cybercrime organizations, not legitimate authorities. The FBI recommends refusing ransom demands and notifying authorities rather than paying criminals.
Some key facts on the legality of non-payment:
- Ransomware distributors cannot legally enforce anything, they are acting criminally themselves.
- You have committed no actual crimes, even though ransomware accuses you of illegal acts.
- Law enforcement actively advises against paying ransomware demands.
- Groups demanding payment cannot legally identify or take action against you for refusing payment.
Do not let fears of criminal consequences prevent you from seeking removal and recovery options. Non-payment of fraudulent ransom demands is completely within your legal rights.
Should I hire an expert to remove FBI ransomware?
In some cases it may be advisable to hire a cybersecurity professional to assist with ransomware removal and system recovery. This is recommended if:
- You do not feel technically able to remove the infection yourself
- Antivirus scans are unable to fully clean the ransomware
- The strain encrypts your backups or prevents typical recovery methods
- You need help assessing damage, restoring data, and strengthening security
Experts like managed service providers can help terminate processes, decrypt files if possible, perform forensic analysis, and harden systems against future threats. This generally comes at significant cost, however.
Individual users can often remove basic infections themselves using free resources online. But companies or victims without technical skillsets may need outside help with reliable ransomware cleanup and file decryption.
Should I use Safe Mode to remove FBI ransomware?
Booting into Safe Mode can be very useful when trying to remove FBI ransomware from an infected Windows computer. Safe Mode loads only essential drivers and services, preventing ransomware from loading.
Benefits of using Safe Mode to remove ransomware include:
- Prevents ransomware processes from running
- Allows removal tools to access locked files and registry entries
- Stops ransomware interfering with anti-malware scans
- Allows you to locate and delete hidden ransomware components
- Boots the system in a minimal environment to focus on removal
Follow these basic steps to use Safe Mode for ransomware removal:
- Restart computer and press F8 while booting to access Safe Mode
- Once loaded into Safe Mode, run comprehensive anti-malware scans
- Check Task Manager and Processes to identify any suspicious executables
- Search for ransomware files and registry keys and delete any that are found
- After removal, reboot normally and run scans again to verify cleanup
Running scans in both Safe Mode and normal startup can help ensure the ransomware is completely removed. Safe Mode gives full access needed for thorough elimination.
Conclusion
While FBI ransomware can be frightening and disruptive, there are ways to deal with it without paying the ransom. Isolating infected devices quickly, using available decryption tools, restoring from backups and employing anti-malware software are all critical steps. Avoiding high risk behaviors and keeping good backups provides the best protection.
Do not panic if infected. The FBI ransomware threats of arrest for non-payment are fake. Report incidents to authorities so they can help build cases against the ransomware gangs. With patience and the right approach, most victims can recover from infections without enriching criminals.