Malware, short for “malicious software”, refers to any program or code intended to cause damage to a computer, server, client, or computer network. Malware includes computer viruses, worms, trojan horses, ransomware, spyware, adware, scareware, and other malicious programs. It is designed to disrupt, damage, or gain unauthorized access to computer systems and networks. Malware poses a major threat to individuals and organizations by stealing sensitive data, interfering with critical systems, monitoring user activity, corrupting files, and even taking control of computers.
Once malware infects a network or computer system, it can quickly spread to other connected devices and systems, sometimes without any action by the user. This makes malware extremely dangerous and difficult to remove once it gets a foothold. The financial toll of malware attacks can be enormous, costing businesses and consumers billions of dollars per year in damages. For these reasons, understanding how malware spreads and implementing effective preventative measures is crucial for protecting networks and endpoints.
Email Attachments
Email attachments are one of the most common ways for malware to spread through a network. Cybercriminals will send emails with malicious attachments, hoping the recipient will open them. According to a Statista report, .doc and .dot files accounted for 37% of malware attachments in spam emails in 2018 (Statista). Once opened, the attachment can unleash malware onto the user’s computer and network.
Some of the most common types of malicious email attachments include:
- Infected Word, Excel, and PDF documents that contain embedded macros or scripts
- “Droppers” which are attachments that install malware when opened
- Compressed or executable files (.zip, .exe) containing malware
To prevent the spread of malware via email attachments, organizations should have security awareness training for employees, email security solutions that scan attachments, restrict certain file types, and sandbox unknown files before allowing them to be opened.
Infected Websites
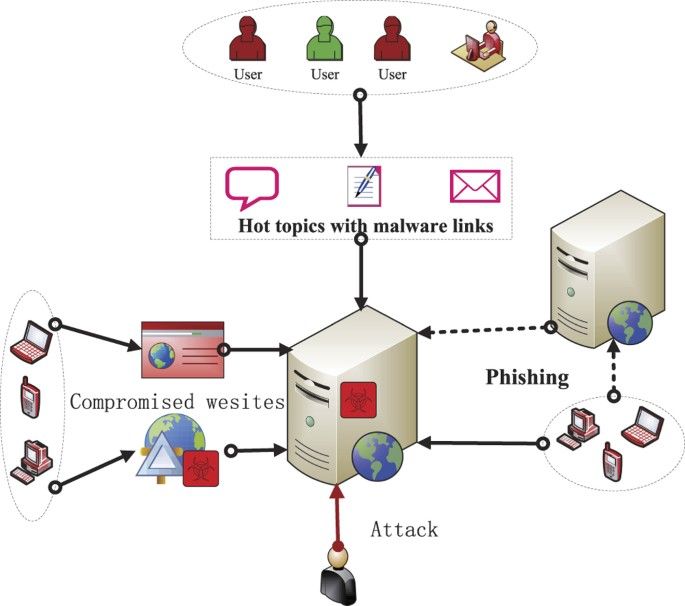
Malware can spread through drive-by downloads that happen when a user visits an infected website. Drive-by downloads refer to the unintentional download of malicious code onto a computer or mobile device without the user’s consent (1). They take advantage of vulnerabilities in web browsers, plugins or other components to automatically download and install malware simply by visiting a website (2, 3).
Attackers exploit drive-by downloads to infect unsuspecting users who visit compromised sites. The malware can install through security holes in the web browser or plugins like Java and Adobe Flash (2). Users may not even notice the malware installation since it happens quickly in the background. Once installed, the malware can steal data, take control of the system, or spread to other devices on the network.
Drive-by downloads often originate from legitimate websites that have been hacked. The hackers inject malicious code into the sites that trigger downloads and installations on visiting devices (3). Users can avoid drive-by downloads by keeping their software up-to-date and using ad blockers. Being cautious around suspicious sites can also reduce exposure.
File Sharing
File sharing, particularly via USB drives, is another common vector for malware to spread throughout a network. When an infected USB drive is plugged into a computer, any malware on it can automatically launch and infect that system. From there, it can spread further if additional USB drives or shared folders are accessed from the infected computer.
According to recent statistics, approximately 37% of data breaches originate from malicious cyber attacks and insider threats [1]. File sharing allows malware to spread rapidly between systems, whether intentionally in the case of an insider attack, or unintentionally through infected external drives. Properly securing file sharing methods like USB drives and network folders is crucial to limiting the spread of malware.
Solutions like endpoint security software, access controls, and user education can help minimize the malware risks from file sharing. But ultimately, users need to exercise caution when transferring files peer-to-peer or plugging in external drives to avoid inadvertently introducing malware.
Exploits
Exploits take advantage of vulnerabilities or bugs in software applications or operating systems to spread malware. When vulnerabilities are discovered, malware authors race to create exploits before patches are released. According to Comparitech, over 560,000 new malware samples were detected daily in 2020, indicating a high volume of new exploits (source). Even widely used software like Microsoft Office or web browsers can contain vulnerabilities that are targeted by exploits. Malware often spreads through drive-by downloads, where visiting a malicious site triggers an exploit that installs malware without any action by the user. Keeping software updated with the latest security patches is critical to preventing exploits. Antivirus programs also rely on vulnerability databases to identify and block malicious exploits. With new vulnerabilities constantly emerging, exploits represent a common vector for malware infection.
Phishing
Phishing is a social engineering attack that tricks users into disclosing sensitive information such as usernames, passwords, and credit card details by masquerading as a trustworthy entity. Cybercriminals use extremely clever social engineering tactics and mimic websites to make phishing emails and websites appear authentic. According to a report, 323,972 internet users fell victim to phishing attacks in 2021.
In a phishing attack, the attacker sends an email that appears to come from a legitimate organization the victim trusts, such as a bank, credit card company, or social media platform. The email will typically include a deceptive call-to-action encouraging the victim to click a malicious link or download an infected attachment. If the victim falls for the scam, they will be led to a fraudulent website and asked to enter sensitive information. This information is then stolen by the cybercriminal.
Some of the most common phishing scams involve emails pretending to be from banks asking users to verify account information, emails impersonating popular streaming and social media platforms requesting users re-enter their password, and messages posing as package delivery companies with links to download shipping labels or tracking information.
According to research from IRONSCALES, 81% of organizations have experienced an increase in email phishing attacks in recent years. Cybercriminals continue to leverage increasingly sophisticated phishing tactics, but user education and advanced email security solutions can help organizations defend against phishing.
Remote Access Tools
Remote Access Tools (RATs) are a type of malware that allow attackers to remotely control a victim’s computer. RATs like RDP (Remote Desktop Protocol) give adversaries full access to a system, allowing them to install additional malware, access sensitive files, log keystrokes, activate webcams, and more.
According to a recent report from Any.Run’s Malware Trends Tracker, RATs were the third most common malware type in 2022, making up 13% of all samples analyzed [1]. WatchGuard’s research also points to the growing use of RATs, with a 12% increase in RAT detections from Q2 to Q3 2022 [2].
One reason for the prevalence of RATs is that they allow attackers easy access to compromised systems. Tools like RDP are meant to provide remote assistance but can be abused by cybercriminals. Once they gain access through stolen credentials or exploits, attackers have free rein over the infected device.
Defending against RATs requires securing remote access tools and detecting unauthorized logins. Multi-factor authentication, VPNs, disabling RDP if not needed, and monitoring network traffic can help prevent RAT infections and disrupt malicious remote sessions.
Insider Threats
One way malware can spread through a network is via insider threats. This refers to employees who intentionally spread malware within an organization, either through malicious intent or negligence. According to research from Tessian, insiders are responsible for around 22% of security incidents (https://www.tessian.com/blog/insider-threat-statistics/). Some alarming statistics on insider threats:
- Careless insider threats account for 62% of data breaches, according to Ponemon. (Source: Proofpoint)
- Malicious employee activity can result in an average cost of $8.64 million for organizations. (Source: IBM)
- 90% of organizations feel vulnerable to insider attacks. (Source: Cybersecurity Insiders)
Insiders may spread malware by emailing infected attachments to co-workers, uploading malware to shared drives or servers, using remote access tools to install malware on systems, or physically inserting infected USB drives into office computers. They take advantage of their access and knowledge of internal systems and processes to distribute malware efficiently before detection. This intentional human element makes insider threats difficult to fully safeguard against.
Mitigation Strategies
There are several ways organizations can mitigate the spread of malware on their networks:
Antivirus Software
Installing antivirus software on all devices connected to the network is one of the most basic but critical steps. Antivirus software can identify and block many types of malware before they can infect devices (Wheelhouse). However, it’s important to keep antivirus software updated and running real-time scans regularly, as its effectiveness depends on having the latest threat definitions (CISA). Studies have shown that antivirus solutions can detect and prevent a significant portion of malware, though not 100% (Maimon).
Firewalls
Firewalls help control what traffic is allowed in and out of a network. They can be configured to block connections to known malicious sites and sources of malware. Firewalls provide an additional layer of protection against malware entering from the outside.
User Education
Training end users on cybersecurity best practices is critical. Users should be educated on risks of opening email attachments, clicking links in emails and messages, downloading files from unverified sources, and using unauthorized programs or devices. Promoting awareness helps prevent users from falling victim to common malware infection tactics.
Conclusion
In summary, malware can spread through a variety of digital pathways. Email attachments containing malicious code, drive-by downloads from compromised websites, infected files on peer-to-peer networks, software vulnerabilities, phishing links, remote access tools, and malicious insiders all enable malware to propagate. To guard against infection, organizations should implement email security filters, employee security training, up-to-date patched software, restricted user permissions, and intrusion detection systems. No single solution can catch all malware, but layering complementary safeguards and keeping users informed can significantly reduce risk.
The cyberthreat landscape will continue to evolve, but vigilance and proactive security measures can help protect systems from malicious software. This overview looked at common infection vectors and key defensive strategies. With thoughtful precautions, organizations can better secure their networks and avoid disruptive malware incidents.