Endpoint detection and response (EDR) and antivirus are two important cybersecurity tools that serve different but complementary purposes. While both aim to detect and block malware and other threats, they go about it in different ways.
What is antivirus?
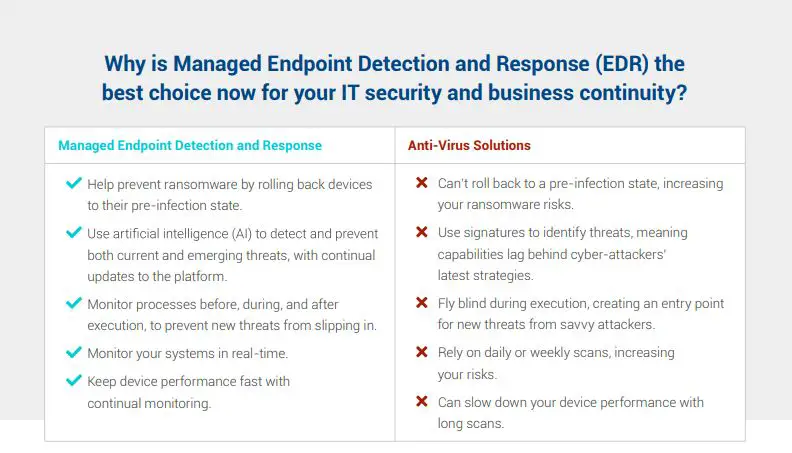
Antivirus is a traditional endpoint security tool that has been around for decades. It uses signature-based detection to identify known malware. Antivirus relies on having a database of malware signatures that it can match against files and programs on an endpoint.
When a file is created or downloaded on a device, the antivirus scanner checks it against its database of malware signatures. If it finds a match, the antivirus will block the file from running and attempt to quarantine or remove it. Antivirus may also use heuristics, a technique that analyzes code for suspicious characteristics associated with malware, even if the exact malware variant is not a known signature.
Antivirus provides real-time scanning and monitoring of endpoints to catch potential malware. It is a critical line of defense against common and widespread malicious threats. However, antivirus only protects against known threats that it has signatures for in its database. It cannot detect or protect against new, unknown malware or fileless and memory-based threats that do not have observable signatures.
What is EDR?
EDR provides more advanced threat detection and response capabilities compared to traditional antivirus. EDR uses additional techniques beyond signature-based detection to identify suspicious activity that may indicate malicious behavior:
- Behavioral analysis – monitors processes, memory, network connections, etc. for anomalous activity that resembles malware
- Machine learning – statistical models are trained to detect malware based on abnormal characteristics
- Deception technology – traps and fakes are set up to attract and detect malware
- Memory scanning – scans RAM actively for indicators of compromise
EDR does not rely on known threat signatures. It can potentially detect never-before-seen malware and advanced threats by analyzing their behavior and characteristics. EDR also provides visibility into the full scope of an attack. It can trace back malware execution flows and lateral movement to determine root cause and impact.
Key Differences Between EDR and Antivirus
Here are some key differences between antivirus and EDR:
Detection Methods
Antivirus – Signature-based detection primarily. Checks files against a database of known malicious file signatures.
EDR – Uses behavioral analysis, machine learning, deception, memory scanning, and other techniques to detect malicious activity and anomalies.
Protection Against Unknown Threats
Antivirus – Cannot detect newly developed threats until signatures are added to its database.
EDR – Can potentially identify never-before-seen malware using behavioral and anomaly detection.
Impact Analysis and Threat Hunting
Antivirus – Provides limited capabilities to trace back malware execution flows and lateral movement.
EDR – Advanced threat hunting capabilities to determine root cause, scope, and impact of threats after detection.
Detection of Fileless/Memory-Based Malware
Antivirus – Challenging to detect fileless or memory-only malware since traditional signature scanning focuses on files.
EDR – Actively scans memory/RAM to identify indicators of attacks that don’t touch disk.
When is antivirus alone not enough?
While antivirus still provides critical protection against common malware, it has significant blind spots against advanced threats that organizations need to be aware of:
- Unknown malware – Antivirus cannot detect new malware until signature updates are pushed out, which can take hours or days. EDR uses behavioral analysis to try to identify malicious activity even without specific signatures.
- Advanced persistent threats (APTs) – Sophisticated targeted attacks often use custom malware or exploit zero-day vulnerabilities that antivirus does not have signatures for.
- Polymorphic malware – Advanced malware can mutate constantly to evade signature detection. EDR behavioral analysis tracks malware even as it evolves.
- False negatives – No antivirus solution is 100% effective. Malware with new signatures or techniques can slip past antivirus detection and compromise endpoints.
- Root cause analysis – Antivirus sees only isolated threats on individual endpoints. EDR can trace malware pivoting between systems and identify patient zero.
- Compliance mandates – Regulations often require more advanced threat detection than just traditional antivirus.
Antivirus vs. EDR Summary
| Capability | Antivirus | EDR |
|---|---|---|
| Signature-based detection | Yes | May optionally utilize |
| Behavioral analysis | Limited heuristics | Full suite of capabilities |
| Machine learning detection | No | Yes |
| Memory scanning | No | Yes |
| Impact analysis/threat hunting | Minimal | Full suite of capabilities |
| Detection of unknown threats | No | Yes |
In summary, while antivirus still provides fundamental protection against known attacks, EDR provides a more advanced layer of protection and response against sophisticated, unknown threats that evade traditional security controls. EDR equips security teams with threat hunting capabilities to determine the root cause and full impact of intrusions before they become significant data breaches.
Many organizations are deploying EDR tools in conjunction with antivirus to benefit from the core strengths of each. Used together, they establish a robust defense-in-depth security posture against both commodity attacks and targeted threats.
How does EDR complement an antivirus solution?
Here are some of the key ways an EDR solution augments and strengthens the protections provided by antivirus:
- Advanced threat detection – EDR uses behavioral analysis, machine learning and other techniques to detect advanced threats that evade signature-based detection.
- Accelerated incident response – EDR integrates and correlates security event data to accelerate incident investigation and remediation.
- Threat hunting – EDR enables proactive threat hunting to identify intrusions that have evaded existing defenses.
- Visibility into threats – Detailed EDR telemetry and data capture provides visibility into the root cause and full impact of attacks.
- Memory protection – EDR scans memory and RAM to detect in-memory attacks and fileless malware.
- Automated containment – Detected threats can be automatically isolated and shut down via EDR integrations with other security controls.
- Compliance support – EDR provides audit trails, system activity details, and reporting to support compliance requirements.
By implementing EDR in addition to antivirus, organizations gain advanced threat protection, faster incident response, proactive threat hunting, and improved security visibility – key capabilities beyond what traditional antivirus alone can provide.
Choosing an EDR solution
Here are some key criteria to evaluate when selecting an EDR product:
Detection capabilities
- Strength of behavioral analytics and machine learning for detecting unknown threats
- Memory scanning to detect in-memory attacks
- Cloud-based machine learning that leverages global threat intelligence
- Deception technology and honeypots to proactively detect threats
Investigation and response functionality
- Incident management and workflow integrations
- Visual timelines and drilling down into events
- Built-in threat intelligence feeds
- Root cause and impact analysis
Proactive hunting
- Threat hunting toolsets and queries to uncover hidden threats
- Ability to ingest and parse logs from multiple data sources
- Automated detection of lateral movement and internal reconnaissance
Integration and automation
- Open API for custom integrations into other security tools
- Built-in integrations with leading tools like firewalls and SIEMs
- Automated response actions like isolating infected hosts
Performance and scalability
- Minimal impact on endpoint performance
- Management console that can scale across many endpoints
- Optimized for speed in detecting and responding to threats
Selecting the right EDR solution involves finding the right mix of advanced threat detection, rapid incident response, proactive hunting capabilities, ease of integration, and scalable architecture to suit an organization’s specific security requirements and resources.
Conclusion
While antivirus software plays an important role in defending endpoints, it has significant blind spots around advanced threats that organizations need to be aware of. EDR platforms complement antivirus by using sophisticated behavioral analytics, machine learning, memory scanning, and other techniques to detect unknown and sophisticated attacks.
EDR strengthens an organization’s security posture by enabling accelerated incident response, proactive threat hunting, increased visibility into malware and attacks, and automation of containment actions. With malware and cyber attacks continually evolving, EDR provides critical capabilities to detect, analyze, contain, and respond to advanced threats that evade traditional endpoint security controls like antivirus.
By implementing a robust EDR solution in conjunction with antivirus, organizations can establish a layered endpoint security approach that covers the full spectrum of malware and attacker techniques they are likely to encounter. EDR closes critical detection and response gaps, serving as an indispensable tool for modern security teams dealing with today’s advanced threat landscape.