Ransomware attacks can be devastating for organizations, bringing operations to a screeching halt and potentially resulting in significant financial losses. A key question for any organization that suffers a ransomware attack is: how long will it take to fully recover?
What is ransomware?
Ransomware is a form of malicious software (malware) that encrypts an organization’s files and holds them hostage until a ransom is paid. Once inside an organization’s network, ransomware spreads quickly, encrypting hard drives, shared drives, networks, backups, and any other files it can access.
The ransom demand itself is usually in the form of cryptocurrency, such as Bitcoin, that is difficult to trace. The demand threatens that the encrypted files will be deleted if the ransom is not paid within a short timeframe. Even if the ransom is paid, there is no guarantee the files will be decrypted. This leaves organizations in a difficult position when hit with a ransomware attack.
Immediate response to ransomware
When ransomware is detected in the network, the immediate response should focus on containment. This involves isolating infected systems to stop the ransomware from spreading further and encrypting more files. Steps include:
- Disconnecting infected systems from the network
- Shutting down any shared drives or resources the ransomware may be using to spread
- Stopping services and processes that are known to be associated with the ransomware
While containing the initial infection is critical, the highest priority is securing backups and ensuring they are free of infection. Backups may be the best way to recover encrypted files after a ransomware attack.
Assessing the impact
Once the initial containment is complete, the next step is to fully assess the impact of the attack. This involves determining:
- How many devices are infected
- Whether backups are intact and usable for recovery
- Which systems, servers, and resources are unavailable due to encryption
- What data or files have been encrypted
- How business operations have been interrupted
This impact assessment allows an organization to understand the scope of the attack and create a recovery plan.
Recovery process and timing
The overall recovery process from a ransomware attack involves:
- Containing the initial infection
- Assessing impact to systems and data
- Cleaning infected systems and restoring data
- Hardening security to prevent reinfection
- Resuming normal operations
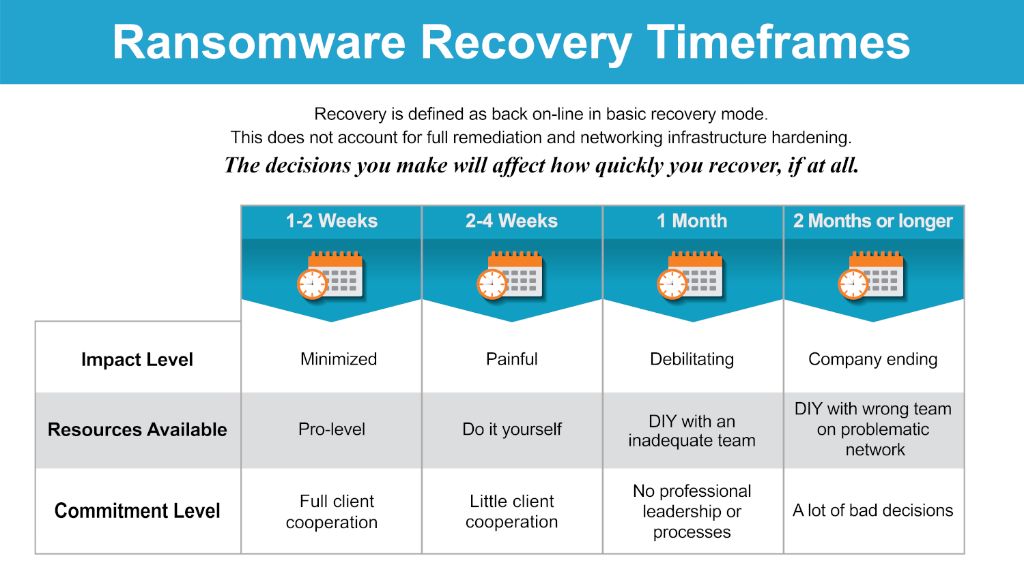
The timing for completing recovery can vary greatly depending on the severity of the attack. Some key factors that influence recovery time include:
| Factor | Description |
|---|---|
| Backup availability | If recent, intact backups are available, data can be restored quickly. If backups are encrypted or unavailable, data recovery will take much longer. |
| Scope of encryption | If only a limited number of devices and files are encrypted, recovery is faster. Widespread encryption across servers, endpoints, networks and backups means a longer recovery. |
| Timeliness of detection | If ransomware is detected quickly before it has time to spread, recovery can begin sooner. A late detection allows more damage and delays recovery. |
| Resources available | Having skilled incident response staff and technology accelerates the recovery process compared to a resource-constrained response. |
According to research, the average recovery time from a ransomware attack is 23 days. However, the recovery timeline can range from as little as a few days to over 100 days depending on the severity of the attack and availability of backups.
Typical recovery timeline
Here is an overview of a typical recovery timeline following a ransomware attack:
| Days 1-3 | Contain infection, disable services/processes, disconnect infected systems, secure backups |
|---|---|
| Days 3-5 | Complete impact assessment, formulate response plan, rebuild servers |
| Days 5-14 | Wipe and reimage infected systems, restore data from backups, implement additional security controls |
| Days 10-30 | Continue monitoring, restore remaining data/services, test systems, validate recovery |
| Days 30-60 | Ongoing security enhancement, staff training, process reviews, resume normal operations |
This shows that while initial containment occurs quickly in the first 1-3 days, full recovery can take over 30 days depending on the complexity of the environment and amount of data to restore. Ongoing security hardening and process improvements continue well beyond 60 days.
Factors that can delay recovery
Some key factors that can greatly lengthen the recovery timeline include:
- No usable backups – Without reliable backups free of infection, recovery of encrypted data may not be possible.
- Extensive cloud service encryption – Ransomware that impacts cloud services and data adds significant complexity to recovery.
- Requirement to rebuild from scratch – If the degree of infection is extremely severe, rebuilding servers and core systems from scratch may be required over attempting to clean infected systems.
- Legacy systems – Recovery takes longer when older legacy systems and applications that may lack backups need to be rebuilt.
- Compliance requirements – In regulated industries like healthcare and finance, compliance requirements can lengthen recovery to ensure security and compliance controls are properly updated.
- Poor response plan – Lack of a documented incident response plan and insufficient resources slows recovery efforts.
Dealing with any of these factors can increase the ransomware recovery timeline from weeks to months in more extreme cases.
Steps to speed up recovery
To help reduce the impact from ransomware and speed up recovery, organizations should focus on these key areas:
1. Maintain reliable, segregated backups
Having recent backups that are kept isolated from the network can provide the ability to restore encrypted data without paying the ransom. Backups should follow the 3-2-1 rule – 3 copies, on 2 different media, with 1 offsite.
2. Install and test detection and response controls
Endpoint detection, next-gen antivirus, and security information and event management (SIEM) tools can all help quickly detect and respond to ransomware attacks to limit damage.
3. Provide malware analysis and remediation training
IT staff trained in malware analysis and containment can act swiftly to isolate infections and start recovery.
4. Develop and test an incident response plan
A detailed response plan that is regularly tested can help organizations quickly follow established processes to contain and eradicate ransomware while minimizing downtime.
5. Segment networks and use access controls
Internal network segmentation, access controls, and the principle of least privilege can help limit the spread of ransomware and reduce the overall impact.
6. Maintain an inventory of critical assets
Knowing exactly where critical data resides, along with its backup status, enables faster data restoration and system rebuilding.
How to prevent ransomware
Ultimately, preventing ransomware infections in the first place is preferable to even the fastest recovery. Organizations should incorporate these critical security measures:
- Security awareness training for staff to recognize phishing and social engineering
- Email filtering and attachment sandboxing
- Regular patching and vulnerability management
- Minimize access permissions and use least privilege
- Next-generation endpoint security tools
- Disable macros in Office products
Ransomware is a continually evolving threat that requires ongoing vigilance to guard against. But with advanced preparation, detection and response capabilities, organizations can minimize both the likelihood and impact of ransomware attacks.
Conclusion
Recovering from a ransomware attack is a complex, multi-stage process requiring time and resources. On average, recovery takes 23 days, but can range from days up to months depending on the severity of encryption and availability of clean backups. Organizations should focus on maintaining reliable backups, training staff in incident response, installing detection tools, and developing a documented response plan to be prepared. With proper precautions and planning, organizations can aim to both prevent ransomware and recover from attacks as quickly as possible.