Digital forensics is the process of preserving, collecting, validating, identifying, analyzing, interpreting, documenting and presenting digital evidence in a manner that is legally acceptable. It is a branch of forensic science that focuses on the recovery and investigation of material found in digital devices, often related to computer crime. Digital forensics has become increasingly important in today’s digital age as more and more crimes involve digital devices and massive amounts of data.
Digital forensic investigators follow a systematic digital forensics process to ensure the best practices for evidence handling. Proper handling and examination of digital evidence is crucial for its admissibility in legal proceedings. With the ubiquity of smartphones, laptops and abundance of digital data, digital forensics provides the tools and framework for authorities to legally obtain, manage and derive insights from digital evidence.
According to a study, over 90% of the world’s data has been created in just the last two years. As the volume of data increases exponentially, the role of digital forensics will continue to grow in importance for both private and public sector organizations.
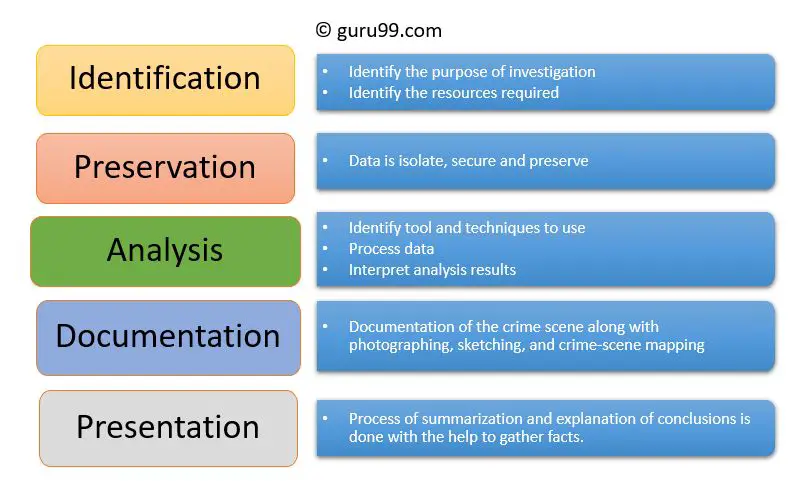
Identification
The Identification step is the first phase of the digital forensics process. This involves detecting potential sources of digital evidence and identifying what type of devices, data, and systems may contain relevant information for the investigation (https://www.eccouncil.org/cybersecurity/what-is-digital-forensics/). The investigator must determine all digital assets that should be included, such as computers, mobile devices, networks, cloud systems, and storage media.
It’s crucial in this initial stage to identify and secure all possible sources of evidence to ensure the integrity of the data. Potential sources of digital evidence that could contain relevant data are documented and collected. Determining the types of devices and systems involved will inform later steps like data acquisition and analysis methodology. Proper identification of all sources lays the groundwork for a complete and thorough investigation.
Preservation
The preservation phase of digital forensics focuses on preserving the integrity of digital evidence and following proper procedures to ensure its admissibility in court. It’s important to preserve evidence in its original state by avoiding actions that could alter data. According to source, evidence should be preserved following the order of volatility, prioritizing evidence that is most volatile like RAM before moving to less volatile storage like hard drives. Proper preservation maintains a chain of custody record and uses cryptographic hashing to validate integrity. Preservation aims to keep digital evidence unaltered until examination.
Collection
The collection phase involves gathering evidence from devices and networks while maintaining integrity. Proper collection requires understanding how to preserve digital evidence and maintain chain of custody (source). Investigators use forensic tools and methods to duplicate data from storage media, being careful not to alter the original data. They document each step to track evidence chronologically.
When collecting evidence, it’s crucial to avoid actions that could damage or alter data. Investigators should not turn devices on or off, access or open files, or run programs unless necessary, as this can modify metadata and timestamps. They must use write-blocking tools to prevent modifying data during acquisition (source). Careful collection and documentation ensures evidence integrity for examination and analysis.
Examination
The examination phase involves forensically examining digital evidence to extract relevant data. This requires specialized tools and techniques to avoid altering the original evidence. Examiners make a bit-by-bit copy of storage media and use write-blocking tools to prevent accidental modification (Forensic Examination of Digital Evidence: A Guide for Law Enforcement).
The examination looks for deleted files, encrypted data, registry entries, internet history, metadata, and other forms of digital information. Advanced techniques like data carving can recover deleted files. Examiners use checksums to validate copied data matches the original. The goal is to extract as much relevant data as possible for analysis.
Analysis
During the analysis phase, investigators carefully examine the forensic copy of the digital evidence to uncover relevant data that can help the case. This involves manually going through files, recovering deleted content, reconstructing fragments of data, decrypting encrypted data, and analyzing the evidence using forensic tools to identify relationships, patterns, and anomalies that have evidentiary value.
One of the biggest challenges is dealing with the typically huge volumes of data found on computers and mobile devices. Investigators need to have a clear objective and scope to focus their analysis, otherwise it can quickly become an unfocused fishing expedition wasting significant time and resources (source).
Advanced forensic tools automate parts of the analysis process through keyword searches, data visualization, and artificial intelligence. But human expertise is still essential to make connections and draw meaningful conclusions from the digital evidence.
By patiently reconstructing fragments of data from unallocated disk space, erased files, temporary files, encrypted volumes, and obscure storage locations, skilled analysts can piece together activities that suspects went through great effort to conceal.
Documentation
Proper documentation is a critical part of the digital forensics process. The investigator must document their methodology and findings in a detailed forensic report. According to the guide “Documenting a Digital Forensic Investigation” (https://www.forensicnotes.com/media/1768/how-to-document-digital-forensic-investigations-with-forensic-notes-ebook.pdf), documentation should include information about the background of the case, procedures followed, hardware and software used, findings, and supporting materials like screenshots. Documentation helps establish a timeline of events, provides transparency, and allows for peer review.
The report produced during the Documentation phase should fully explain the steps taken during the investigation and examination in a way that could allow an independent examiner to reproduce the results. Details about the equipment, software, and settings used should be recorded. Any issues encountered should also be noted. According to the article “What Are the 5 Stages of a Digital Forensics Investigation?” (https://ermprotect.com/blog/what-are-the-5-stages-of-a-digital-forensics-investigation/), comprehensive documentation makes the findings defensible in court.
Presentation
The presentation step focuses on effectively communicating the findings from the digital forensic investigation to the relevant stakeholders or in court during legal proceedings. Forensic investigators must be able to clearly explain technical details in a way that is understandable to non-technical audiences.
When presenting in court, it is important to appear credible and use presentation aids to walk through the evidence. According to an article on the Magnet Forensics website, tips for presenting digital evidence in court include using demonstrative exhibits, avoiding technical jargon, and being prepared to explain how evidence was collected and verified (source).
The analysis and conclusions should be presented through reports, timelines, graphs, videos or other visual means. Succinct executive summaries can help summarize complex technical details for legal teams and investigators. It is also important to be able to explain the methodology and maintain chain of custody records. Proper presentation of analysis and evidence can make or break the case.
Archiving
Once the examination and analysis of the digital evidence is complete, the final step is properly archiving the evidence for long-term storage and retrieval if needed. Archiving involves storing the evidence securely, maintaining the integrity of the data, and allowing for retrieval in the future.
It is crucial to store digital evidence in a manner that preserves the data and maintains the chain of custody. According to research, “The process of collection and archiving digital evidence is outlined in order to maintain its integrity” (source). Proper archiving requires special storage conditions like access controls, data redundancy, and disaster recovery plans.
Best practices dictate that evidence should be stored on reliable media like external hard drives or secure cloud storage. The storage method should protect against data degradation and provide error detection for data integrity. A master copy should be created and access limited to prevent data tampering.
Meticulous logs must be kept regarding storage locations, access records, and chain of custody. Detailed documentation enables retrieval of specific evidence when required. With proper archiving protocols, digital evidence can be safely preserved over long periods while maintaining its integrity.
Common Challenges
Digital forensics investigations face several common challenges that can impede the investigation process and make it difficult for investigators to access and analyze data. Some key challenges include:
Encryption – One major challenge is encryption, which scrambles data so that only authorized parties can access it with the proper cryptographic key. Strong encryption, especially full disk encryption, can prevent investigators from accessing data on devices or networks. This is a significant obstacle in many investigations (https://www.geeksforgeeks.org/challenges-in-digital-forensics/).
Anti-forensics – Criminals often use anti-forensic techniques to cover their tracks and thwart investigations. This can involve deleting, hiding, or tampering with data to avoid detection. Anti-forensics presents a constant “cat and mouse” challenge for investigators (https://www.mailxaminer.com/blog/current-challenges-in-digital-forensics-investigations/).
Jurisdictional issues – Legal jurisdictions and restrictions can pose obstacles, especially with cross-border cybercrime investigations. Conflicting laws, data privacy regulations, and lack of multinational cooperation make it difficult to access data across jurisdictions.