Protecting your sensitive personal and work data is more important than ever in today’s digital world. From financial records to personal photos and confidential work documents, the data stored on your Mac contains your most private information. Applying encryption and implementing other security measures can help keep your data safe from unauthorized access, even if your Mac is lost or stolen.
In this comprehensive guide, we will explore the built-in tools and best practices for encrypting and securing your data on a Mac.
Encrypt Your Startup Disk with FileVault
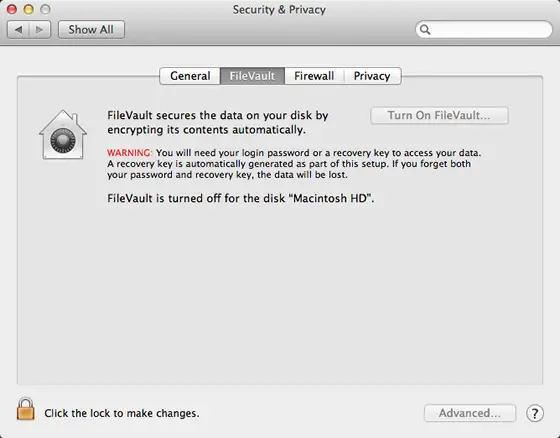
FileVault is the built-in full disk encryption tool in macOS that allows you to encrypt the entire startup disk on your Mac. When FileVault is enabled, all of the data on your startup disk is encrypted using advanced 128-bit AES encryption. This prevents anyone from accessing your data if they gain physical access to your Mac when powered off.
Enabling FileVault
To turn on FileVault:
- Go to System Preferences > Security & Privacy.
- Click the FileVault tab.
- Click the lock icon and enter your admin password to make changes.
- Click Turn On FileVault.
- Follow the on-screen instructions to enable FileVault. You will be asked to set a new password that will be required to unlock the encrypted disk on startup and restart.
Once enabled, FileVault will encrypt the entire drive in the background as you use your Mac. This process can take a while depending on the amount of data on your disk. Your Mac is still safe to use during encryption.
Choosing a Strong FileVault Password
When turning on FileVault, you’ll need to set a strong password that will be required to unlock the encryption on startup. This password should be different than your account login password. Here are some tips for choosing a strong FileVault password:
- Use at least 16 characters or longer if possible. The longer the better.
- Include a mix of letters, numbers and symbols. Avoid common words.
- Do not use any personal information like birthdays or addresses.
- Consider using a passphrase instead of a single password. A passphrase made up of multiple words can be easier to remember but still secure.
- Write your password down and keep it somewhere very safe in case you forget it. Losing the FileVault password means the data is unrecoverable.
- Consider storing your FileVault password in a password manager like 1Password for added security.
Without the FileVault password, there is no way to decrypt and access the data on your startup disk. Make absolutely sure you do not lose this password.
Decrypting Startup Disk with FileVault
When starting up or restarting your Mac with FileVault enabled, you will be greeted with the FileVault login screen. Here you need to enter the FileVault password to decrypt and mount the startup disk.
If you forget your FileVault password, there is no way to recover or reset it. This means the data on the startup disk will remain encrypted forever with current technology. The only options are:
- Take your Mac to Apple and hope they can help recover the password using special tools. There is no guarantee.
- Erase the entire startup disk to remove encryption, but all data will be lost in the process.
- Replace the drive and reinstall macOS if you absolutely need access to the Mac itself, but data on old drive stays encrypted.
The consequences of losing a FileVault password are severe. Make sure you store the password somewhere safe or use a password manager as a backup.
Backing Up an Encrypted Startup Disk
It is extremely important to maintain backups of your FileVault encrypted startup disk. Backups provide a way to recover your data if something ever happens to your startup drive or you lose access to it.
Apple’s Time Machine backup software works seamlessly with FileVault. Simply make sure Time Machine backups are running normally after enabling FileVault. Backups of your encrypted drive will continue as normal.
If you need to restore from a Time Machine backup after reinstalling macOS, you will still need your FileVault password to decrypt the backup data. Time Machine backups do not bypass FileVault encryption.
You can also create encrypted backups using Disk Utility or third party backup software that supports encryption. Just be sure to remember the backup password.
Caveats of FileVault Startup Disk Encryption
While FileVault provides excellent protection for data at rest, there are some limitations to be aware of:
- No protection when Mac is on. Data in memory and use is unencrypted.
- No protection for external drives. FileVault only encrypts the internal startup disk.
- Potential for data loss if password is lost. No built-in reset option.
- Performance impact. FileVault encryption/decryption uses CPU resources which can slow down certain tasks. Typically this is only noticeable on older Macs.
- Keys derived from password. Not as secure as using a random key.
- Requires OS reinstall to turn off. Can’t simply decrypt a FileVault drive, you must erase it.
For maximum security, FileVault should be used in combination with other encryption methods when your Mac is powered on and for external devices.
Encrypt External Drives and Volumes
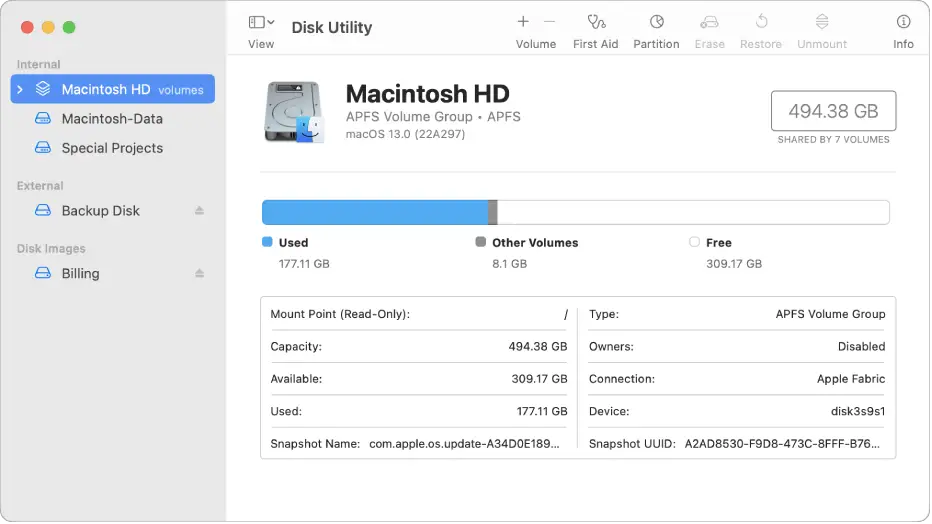
FileVault only encrypts the built-in startup disk of your Mac. To protect data stored on external drives, you need to separately enable encryption for each drive.
Encrypting External Drives with Disk Utility
Disk Utility in macOS provides the option to easily encrypt most external drives and volumes.
To encrypt an external drive:
- Connect the drive to Mac and open Disk Utility.
- Select the external drive in the sidebar.
- Click Erase at the top.
- Choose a name and APFS or Mac OS Extended format.
- Select the Scheme as GUID Partition Map.
- Choose AES-256 encryption for secure protection.
- Click Erase to encrypt the entire drive.
You can also create an encrypted volume instead of the entire drive. During formatting, select Add Encryption Password and then specify the size of the encrypted volume. This will create an encrypted container that mounts as a separate drive.
The encryption password for disks encrypted with Disk Utility is required to mount and access the drive on any Mac. Make sure to safely store this password as there is no way to recover data without it. Use a password manager or written password in a secure place.
Third Party Encryption Tools
There are many third party utilities that can provide advanced encryption options for external drives and volumes beyond what Disk Utility offers. Some popular Mac drive encryption tools include:
- VeraCrypt: Open source disk encryption software that lets you create encrypted containers or partitions. Supports AES, Serpent, and Twofish ciphers.
- Cryptomator: Allows transparent encryption of cloud storage and external drives with AES and HMAC-SHA256. Features a browser vault for convenient access.
- Boxcryptor: Provides client-side encryption for cloud services like iCloud Drive and Dropbox. Uses AES-256 and Whirlpool hashing.
- Encrypto: Drive partitioning and encryption tool for creating multiple encrypted volumes. Comes with useful utilities for wiping drives.
Experiment with a few options to find an external drive encryption tool that provides the right blend of features, security and convenience for your needs.

Encrypt Files and Folders with Secure Enclave
The Secure Enclave in Macs with a T2 security chip provides enhanced encryption capabilities for files and folders. It uses a protected key stored in the Secure Enclave instead of tying encryption to your account password.
Here is how to use Secure Enclave encryption:
- Right click on any file or folder and select Encrypt [name]
- The file or folder will be encrypted using your UserID hash and Secure Enclave Processor.
- To decrypt, right click and select Decrypt [name]. Enter password when prompted.
- Can also encrypt from Finder by selecting file/folder and pressing Control-Command-E.
Secure Enclave encryption is applied at the individual file and folder level for flexible control. It is quick and easy to enable this added protection for your sensitive documents.
The main advantages of Secure Enclave file/folder encryption include:
- Uses protected key stored in hardware – not tied to account password.
- Convenient to apply selectively to individual files and folders.
- Seamless encryption/decryption once enabled. Works like normal files.
- Encrypted items do not count towards Time Machine quotas.
- No additional software required. Uses built-in macOS capabilities.
Secure Enclave encryption provides robust protection for your most sensitive files and documents when your Mac is powered on. It complements full disk FileVault encryption nicely.
Leverage iCloud Keychain for Passwords and Secure Notes
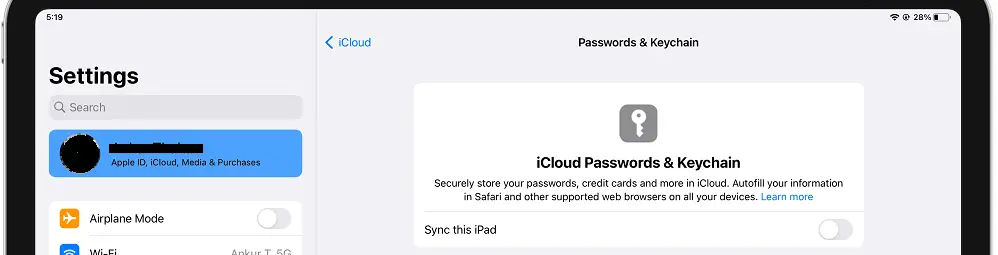
iCloud Keychain is Apple’s built-in password manager that also lets you store encrypted notes and passwords across your approved Apple devices. Leverage iCloud Keychain to improve the security of your logins and create protected notes.
Here are some key features of iCloud Keychain:
- Automatically saves and enters usernames and passwords for websites and apps.
- Syncs passwords across iCloud devices so you can access them anywhere. Requires two-factor authentication enabled.
- Uses end-to-end AES 256-bit encryption to protect all data in Keychain. Keys are stored in Secure Enclave.
- Secure Notes allow you to create encrypted notes that sync through iCloud to approved devices.
- Two-factor authentication required for additional protection and to sync to new devices.
To set up iCloud Keychain:
- Make sure two-factor authentication is enabled for your Apple ID.
- Go to System Preferences > iCloud and enable Keychain.
- Approve your other devices to sync Keychain data.
Once configured, iCloud Keychain will securely store website logins, WiFi passwords, credit card information, and secure notes. This provides easy access across your approved devices while protecting sensitive data.
Encrypt Individual Documents with PDF and Office File Password Protection
Many document file formats like PDFs, Word, Excel, and PowerPoint files support built-in password protection to encrypt their contents.
To password protect and encrypt documents:
PDFs
- Open PDF in Preview
- Click File > Export As
- Select Encrypt option and create password
Microsoft Office Files
- Open file in supported Office app like Word, Excel, etc.
- Go to File > Info > Protect Document/Workbook/Presentation
- Enter password to enable protection
The exact steps may vary in different applications, but look for protect, encrypt or password options when exporting or saving documents.
This type of encryption only protects the individual document with the password. Other files will remain accessible. It is most useful for encrypting sensitive documents to share or transmit securely.
Be sure to communicate the encryption password out-of-band to the intended recipient to allow them to open the protected document. Never include the password directly in an email.

Use SSL/TLS Encryption for Email and Web Browsing
Encrypting web traffic and email is crucial for securing your communications and preventing eavesdropping. Here are some ways to enable encryption:
Web Browsing
- Use HTTPS websites – indicated by lock icon in browser address bar. Information is encrypted between your computer and the website server.
- Install HTTPS Everywhere browser extension to use HTTPS on more sites automatically.
- Avoid public WiFi or use a VPN service to encrypt all traffic on public networks.
- Use an email provider like Gmail that uses TLS encryption for sending/receiving emails. Messages will be encrypted between mail servers.
- For maximum protection, consider end-to-end encrypted email through a service like ProtonMail which fully encrypts message contents and not just transport between servers.
- Encrypt sensitive emails by storing the message in an encrypted document attached to the email instead of in the body content.
Ensuring SSL/TLS encryption is enabled provides vital protection for your web browsing and email communication. This closes major potential security holes where attackers could otherwise access unencrypted data.

Use Encrypted Messaging Apps for Chat and Video Calls
When communicating over chat, voice, or video ensure you use encrypted messaging apps for maximum protection:
- Signal – Free end-to-end encrypted messenger for iOS/Android with secure chat, voice calls and video conferencing. All communications are encrypted in transit and messaging history is encrypted on your devices.
- WhatsApp – Provides end-to-end encryption for messages and calls. All communications are encrypted between you and the recipients. Uses the Signal protocol.
- iMessage – Apple’s iMessage service has end-to-end encryption enabled by default for messages between iOS devices and Macs. Communications are securely encrypted on your devices.
- FaceTime – Utilizes end-to-end encryption to secure FaceTime voice and video calls placed between Apple devices. Communications are encrypted in transit and only viewable by you and recipients.
Avoid standard SMS messaging and regular phone calls as these have no encryption protections by default. Always opt for a secure encrypted messaging or calling service when communications may involve sensitive information. This will ensure only you and the intended recipients can view or listen to the conversation.

Use a Virtual Private Network (VPN) to Encrypt Public Network Traffic
When connecting to public WiFi networks you should always use a VPN service to encrypt your device’s internet traffic and hide your IP address. Here are some top options:
- NordVPN – Fast VPN with over 5200 servers worldwide. Provides military-grade encryption using IKEv2/IPsec protocols and includes useful cybersecurity tools.
- ExpressVPN – Secure and reliable VPN with 3200+ global servers. Uses AES-256 encryption combined with perfect forward secrecy and a kill switch to block traffic if VPN drops.
- ProtonVPN – Run by the same team behind encrypted email provider ProtonMail. Uses AES-256 and ECC ciphers with perfect forward secrecy. No logs policy.
- TunnelBear – Easy to use VPN app with bear-themed interface. Smaller network but provides AES 256-bit encryption.
A VPN routes and encrypts all network traffic between your device and the VPN server before entering the public internet. This prevents snooping on open WiFi networks. Be sure to select a trustworthy provider who will not keep usage logs.
Many antivirus apps also include VPN functionality. For example, Norton 360 plans come with their own VPN service called Norton Secure VPN.
Maintain Proper Encryption Hygiene
While applying encryption is critical to securing your data, proper encryption hygiene is also vital to get the most protection. Here are some key principles of solid encryption hygiene:
- Use strong unique passwords – Never reuse passwords across encryption keys and devices. Use random complex strings of at least 16 characters or passphrases for maximum safety.
- Store passwords/keys securely – Encryption keys should be written down or saved in a secure password manager, but never stored in plain text digitally where they are more easily accessed if a device is compromised.
- Secure unlocking mechanism – Use a PIN code, biometric, or security token to unlock your encryption keys instead of entering the full encryption password each time. Make the password very long and complex and only enter it infrequently when needed.
- Escrow reset keys – Have a backup procedure to re-enable access to encrypted devices and data via recovery keys or a key escrow server in case passwords are forgotten or lost.
- Use two-factor authentication – Enable two-factor authentication (2FA) on online accounts whenever possible. This combines your password with a one-time code tied to a physical device you own.
- Keep encryption updated – Use the latest up-to-date operating systems and encryption software with the most secure algorithms and protocols to prevent compromise. Update promptly when security patches are released.
Following principles of encryption hygiene reduces your risk substantially against data breaches, unauthorized access, and lost keys. Make encryption security processes and habits a routine part of your digital life.
Conclusion
Safeguarding your sensitive data involves both utilizing strong encryption tools and also following security best practices in your computing habits. Enable FileVault and external drive encryption to protect data when your devices are off. Use Secure Enclave file encryption, encrypted messaging, VPNs, and SSL browsing for safe communications when powered on. With the right combination of encryption technology configured thoughtfully, you can dramatically lower your risk of privacy and data breaches.
However, it is important to remember encryption does not fully replace practicing good cybersecurity. Routinely backing up your data, using strong unique passwords, keeping software updated, avoiding malware and more foundational measures are still necessary to complement encryption protections.
Encryption applied properly gives you an added layer of defense but it is not bulletproof. You should still take precautions in how you access and share encrypted data. Ultimately being security conscious across your online behaviors and accounts remains imperative even when leveraging encryption. Used wisely as part of a comprehensive security plan, robust encryption can significantly harden your defenses against unauthorized access.

