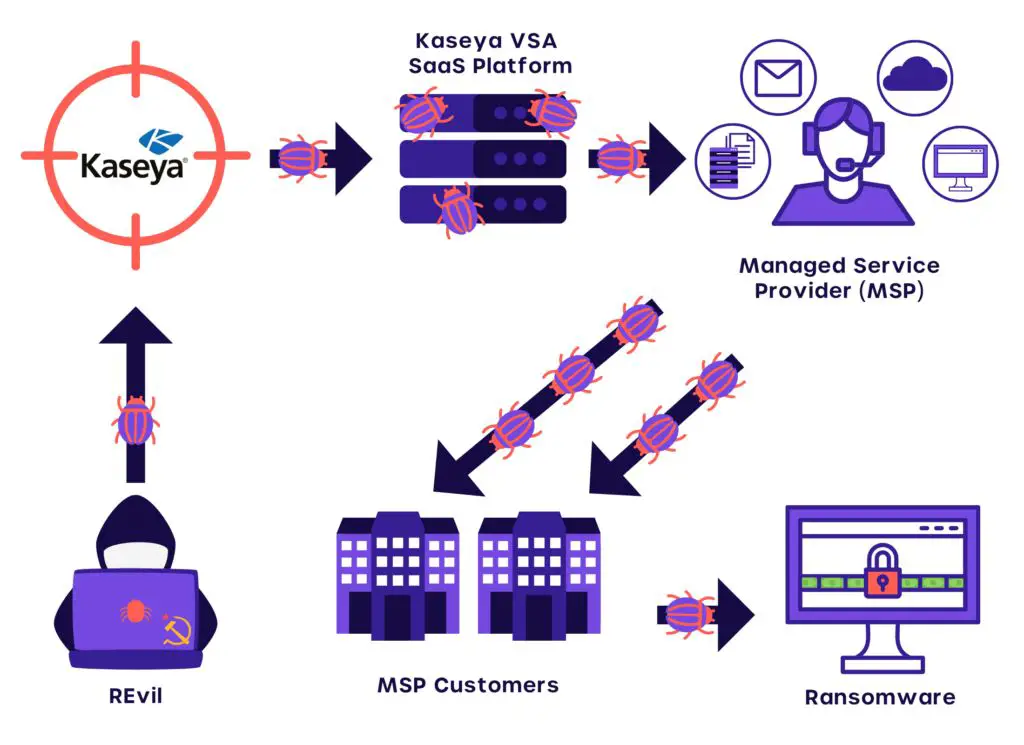
Kaseya is an IT management software company that provides remote monitoring and management, system management, and network monitoring solutions for managed service providers (MSPs) and small to mid-sized businesses. Their flagship product is Kaseya VSA, which allows MSPs to monitor and manage IT infrastructure for multiple clients from a central location.
In July 2021, Kaseya was the victim of a major ransomware attack that impacted an estimated 800 to 1,500 businesses that relied on Kaseya’s VSA software to manage their networks and endpoints. The attack has been attributed to REvil, a notorious Russia-based ransomware group. Hackers were able to exploit vulnerabilities in Kaseya VSA to push ransomware onto the systems of businesses that used the compromised software. This led to widespread disruption, encrypted systems, and demands for millions of dollars in ransom payments from victims.
The Initial Compromise
The cyberattack on Kaseya began in early July 2021 when threat actors exploited a zero-day vulnerability in Kaseya VSA software. This vulnerability, tracked as CVE-2021-30116, allowed the attackers to bypass authentication and execute arbitrary code on vulnerable servers. Specifically, the attackers were able to abuse a code injection flaw in the VSA web interface to deploy ransomware payloads disguised as software updates to connected endpoints.
This zero-day vulnerability provided the initial foothold into Kaseya’s systems that the attackers leveraged to compromise up to 1500 downstream businesses that relied on Kaseya’s IT management tools. According to researchers, the attackers were able to exploit this vulnerability in VSA because Kaseya did not follow standard software development practices around input validation and access controls. This allowed the attackers to easily gain high level permissions to distribute malicious payloads across Kaseya’s customer base.
While technical details of the vulnerability have been made public, it’s clear that the lack of basic cybersecurity hygiene around software development and patching enabled the wide-reaching impacts of this breach. Identifying and fixing these systemic gaps will be key for Kaseya and other software vendors looking to avoid similar supply chain attacks moving forward.
Lateral Movement
Once inside Kaseya’s network, the attackers needed to move laterally to find and access critical systems and data to carry out their attack. As explained in detail by CyberArk https://www.cyberark.com/resources/blog/in-kaseya-supply-chain-ransomware-attack-history-repeats-itself, the attackers were able to leverage Kaseya’s single sign-on solution to authenticate across applications and systems. This enabled broad access across the network without needing to crack credentials for each system individually.
The attackers systematically worked their way through Kaseya’s systems, identifying and taking over critical servers and applications like VSA. Rather than attacking everything at once and triggering alarms, the patient lateral movement allowed them to stay undetected as they methodically identified and took control of the key targets. This surgical precision indicates the attack was carefully planned and executed by a sophisticated, experienced group.
By moving laterally in this controlled way, the attackers could access the specific systems and data needed to orchestrate a massive supply chain ransomware attack impacting many of Kaseya’s customers downstream. Lateral movement was the key phase that enabled the full extent of the breach.
The Payload
The payload deployed by the attackers in the Kaseya breach was the REvil ransomware variant. REvil, also known as Sodinokibi, is an extortion-focused ransomware that exfiltrates data from victims and threatens to publish it online if the ransom demand is not paid. The attackers exploited a zero-day vulnerability in Kaseya’s VSA remote monitoring and management tool to deploy the ransomware to customers via supply chain attack.
The impacts of the attack were massive in scale. According to Wikipedia, REvil claimed to have encrypted over 1 million systems during the incident. Although the true number was likely lower, the supply chain nature of the attack meant thousands of downstream businesses and organizations were compromised. Many victims had their networks and data encrypted and operations disrupted. According to Varonis, impacted victims included grocery stores, schools, manufacturers, and local governments.
The far reaching impacts demonstrate the risks of supply chain vulnerabilities and the ongoing threat of ransomware, especially targeted “big game hunting” campaigns by sophisticated actors. As the most destructive ransomware incident to date, the Kaseya attack highlighted gaps in security, the interdependency of service providers, and the need for enhanced resilience across the IT ecosystem.
The Attackers
The Kaseya cyberattack is attributed to REvil, a prolific Russian-based ransomware group.[1] REvil is known for targeting high-profile companies and demanding large ransom payments, with previous victims including Acer, JBS Foods, and Travelex.[2]
REvil gained initial access to Kaseya’s systems by exploiting unpatched vulnerabilities in their VSA remote monitoring software. They used this to distribute ransomware payloads disguised as legitimate software updates to downstream customers. This allowed the ransomware to quickly spread through Kaseya’s supply chain in a massive supply chain attack.[3]
The attackers demanded a $70 million ransom payment from Kaseya to provide a decryptor for affected systems. However, before negotiations concluded, REvil mysteriously disappeared from the internet, leaving victims without support.[2] The motivations behind the attack appear to be financial gain, but the identity of the individuals responsible remains unknown.
Scope of Compromise
The attack affected a limited number of Kaseya’s customers, with the company estimating only about 50 out of over 35,000 customers were actually breached (Kaseya Responds Swiftly to Sophisticated Cyberattack, n.d.). However, because Kaseya’s clients include IT service providers that serve other businesses, the downstream impact was much wider. In total, researchers estimate 800 to 1,500 businesses may have been affected around the world (The Kaseya ransomware attack: A timeline – CSO Online, 2021).
The ransomware attack had global reach, though it was clustered in certain countries. Ten percent of victims were based in Germany, another 10% in the United Kingdom, 7% in Canada, and 3% in the Netherlands, according to cybersecurity firm Huntress Labs. Other known victims were located in Sweden, South Africa, Indonesia, New Zealand and Kenya (Updated Kaseya ransomware attack FAQ: What we know now, 2021).
The Aftermath
Kaseya responded quickly to the attack, shutting down their SaaS servers as well as customer on-premises servers that use VSA within hours on July 2nd to prevent the malware from spreading (Incident Overview & Technical Details). They also urged companies to shut down their VSA servers immediately. Kaseya released software patches later that weekend to address the vulnerability and bring systems back online safely.
However, many VSA customers suffered significant impacts. Even after patching, some found their systems were still encrypted by REvil and unusable. Restoration was a slow process, with some reporting weeks or months before they were fully operational again. There were also ongoing disruptions as forensic analysis and remediation continued (Kaseya Ransomware Victim Speaks Out). The supply chain nature of the attack compounded difficulties as MSPs worked urgently to secure their own systems and customers.
Liability and Lawsuits
The breach resulted in extensive legal action against Kaseya. Many of Kaseya’s customers that were impacted by the ransomware attack filed lawsuits seeking to hold the company liable for the damages they incurred.
In July 2021, just days after the attack, a class action lawsuit was filed in federal court in Florida on behalf of impacted businesses. The lawsuit alleges that Kaseya failed to take adequate cybersecurity measures to protect its software from a breach.
Additionally, in August 2022, a Miami law firm filed a lawsuit in Florida state court seeking over $15 million in damages from Kaseya. The plaintiff claims that Kaseya’s vulnerabilities resulted in a ransomware attack that crippled their systems and forced them to pay a large ransom.
These lawsuits argue that Kaseya had a responsibility to safeguard its systems and software from criminal exploitation. By failing to do so, Kaseya exposed its customers and their data to significant harm from the ransomware attack.
Lessons Learned
The Kaseya breach highlighted several key security takeaways for both Kaseya and organizations using their products. First, the initial compromise occurred because Kaseya did not have multi-factor authentication enabled for all critical accounts and services. According to analysis from Coretelligent, the attackers were able to leverage stolen credentials to gain initial access [1]. Enabling MFA is a critical baseline security control that could have prevented this breach.
Additionally, there were opportunities to limit lateral movement and scope of compromise. The attackers were able to move from Kaseya’s systems to customer environments. Properly segmenting and isolating development, production, and client environments could have contained the blast radius. Kaseya has since made improvements to its architecture and access controls to better protect customer data and prevent lateral movement [2].
For organizations using Kaseya products, the key lesson is the risk of supply chain attacks. No vendor is bulletproof, so having a defense-in-depth security strategy is essential. UpGuard recommends not putting “all your eggs in one basket” and diversifying vendors to limit exposure from any single point of failure [3].
Conclusion
In summary, the Kaseya breach involved threat actors exploiting vulnerabilities in Kaseya’s VSA remote monitoring and management tool to deploy ransomware across customer networks in what is considered one of the largest ransomware attacks to date. The attackers were able to compromise Kaseya’s software supply chain to impact over 1,500 downstream businesses in at least 17 countries. While Kaseya and law enforcement officials were able to disrupt the attack’s spread, the incident highlighted the immense risk posed by software supply chain compromises and the cascading impacts they can unleash.
The breach has had lasting impacts for Kaseya and its customers. Several businesses faced significant disruption, data loss, and costs for incident response and recovery efforts. Some organizations even had to cease operations entirely. Kaseya faced scrutiny over its security practices and response to the incident. Multiple lawsuits were filed alleging Kaseya did not adequately secure its systems or warn customers in a timely manner. The event underscores the importance of software vendors prioritizing security, quickly patching vulnerabilities, and maintaining effective communication with customers, especially during crisis events.
Going forward, all players in the software supply chain should heed the lessons around adopting a proactive security posture, automating security processes, collaborating across organizations, and planning effective incident response procedures. Though the Kaseya attack caused major disruptions, its full impact was avoided due to the combined efforts of cyber defenders and the security community. With vigilance and cooperation, we can become more resilient against the rising threat of software supply chain attacks.