NotPetya burst onto the scene in 2017 as one of the most destructive malware attacks in history. Within just a few hours, this vicious ransomware crippled businesses, government agencies, and infrastructure around the world. But where did NotPetya come from, and is it still a threat today? Let’s take a deep dive into the origins, impact, and status of this infamous cyberattack.
What is NotPetya?
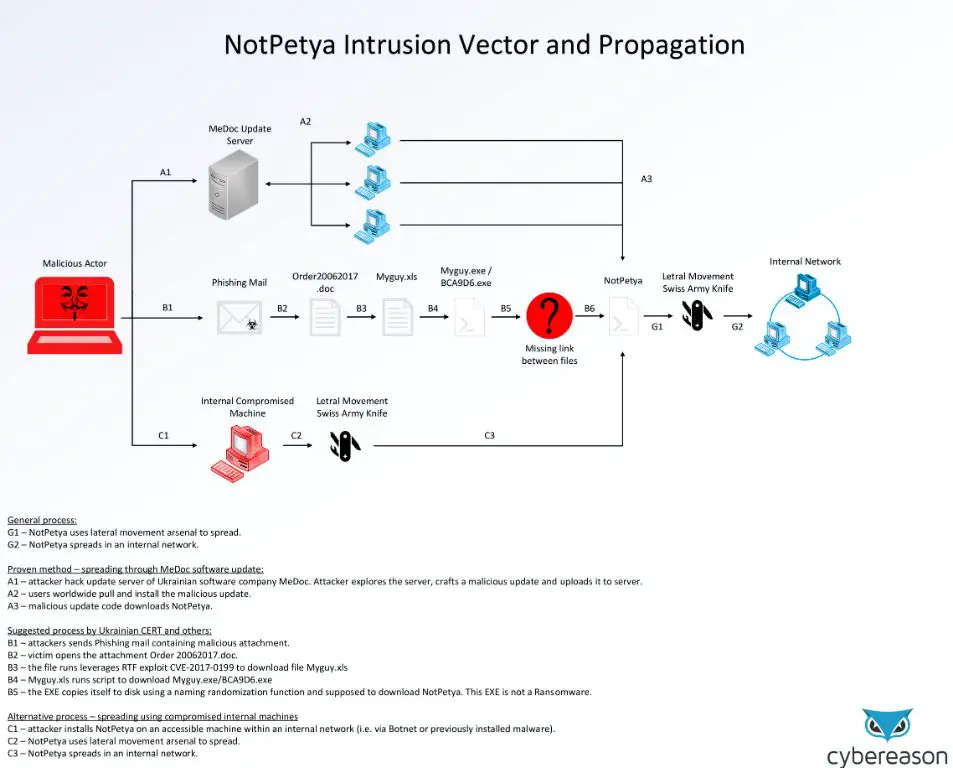
NotPetya is a worm that combines ransomware with features of a computer virus. It is designed to spread quickly within networks while encrypting files and demanding ransom payments in Bitcoin. The malware disguises itself as a software update from a legitimate company to trick users into downloading and activating it.
Once activated, NotPetya overwrites the master boot record of infected Windows computers, rendering them inoperable. At the same time, it encrypts files using AES and RSA encryption algorithms and displays a ransom note demanding $300 worth of Bitcoin. Even if the ransom is paid, NotPetya is designed to permanently damage infected systems.
NotPetya sets itself apart from typical ransomware in a few key ways:
- It propagates using multiple exploit vectors to spread aggressively like a worm.
- It is non-decryptable – paying the ransom does not restore system access.
- It seeks to destroy rather than extort victims.
Due to these nasty attributes, many experts consider NotPetya to be more of a wiper malware designed to destroy data rather than extract ransom payments. The ransom demand appears to be just a facade.
Origin and Attackers
NotPetya first appeared in early 2017, though its origins before that are murky. Some reports suggest the malware has connections to BlackEnergy, a malware toolkit used by the Russia-linked cyber espionage group Sandworm. However, direct responsibility for NotPetya has not been conclusively attributed to any specific group.
The first known NotPetya attack targeted financial, energy, and government institutions in Ukraine. The malware was spread via a corrupted update to the M.E.Doc tax accounting software used widely in the country. This initial attack vector allowed NotPetya to infect over 12,500 Ukrainian businesses and organizations.
From there, the worm spread rapidly using the EternalBlue and EternalRomance exploits leaked from the NSA. These tools allow the malware to leverage vulnerabilities in older versions of Windows’ Server Message Block (SMB) protocol. NotPetya was able to move laterally within networks and infect additional machines without user action.
2017 Global Outbreak
Within just a few hours of the initial Ukraine attack, NotPetya erupted into a worldwide epidemic. Major multinational companies were soon infected, including:
- Shipping giant Maersk – NotPetya disrupted worldwide logistics operations, costing the company over $300 million.
- Pharmaceutical corporation Merck – NotPetya halted production of the Gardasil 9 vaccine, resulting in an estimated $870 million loss.
- Food company Mondelez – NotPetya corrupted 1,700 servers and 24,000 laptops, causing an estimated $188 million in damages.
- Advertising firm WPP – Thousands of systems were decryptlocked, with damages upwards of $15 million.
In total, NotPetya struck organizations in at least 65 countries. Estimates indicate damages exceeded $10 billion, making it the costliest malware attack on record.
Impact in Ukraine
While global businesses suffered from disrupted operations and data loss, Ukraine was crippled by NotPetya. Critical national infrastructure like power stations, airports, hospitals, and the central bank were knocked offline. Radiation monitoring systems at the old Chernobyl nuclear plant were also impacted, temporarily disabling radiation level monitoring capabilities.
An estimated 60% of Ukraine’s computers were compromised. Government agencies had entire networks disabled, forcing workers in some areas to switch to typewriters and paper documents. Overall, Ukraine sustained over $10 billion in NotPetya damages, equivalent to 10% of the country’s gross domestic product.
Is NotPetya Still Active?
Fortunately, NotPetya’s reign of destruction was short-lived. Within just a few weeks, the outbreak had been contained and new infections stopped. This rapid decline was due to multiple factors:
- Patching vulnerabilities – Microsoft quickly released patches for the EternalBlue and EternalRomance exploits used by NotPetya to spread.
- Disabling email – Organizations blocked email attachments which were used to distribute the malware.
- Isolating infections – IT staff limited the worm’s lateral movement by isolating or shutting down compromised systems.
- Built-in kill switch – NotPetya was programmed to stop spreading after a set time period.
Within a month, NotPetya infections had essentially ceased. The malware remains detectable by antivirus software if found, but the worm is no longer spreading or infecting new targets.
Could NotPetya Return?
Theoretically, threat actors with access to NotPetya’s code could re-engineer the malware to reignite infections. However, this is unlikely for a few reasons:
- Patches are now widely implemented for the exploits NotPetya used to spread.
- Targets are more vigilant of cyberattacks using fraudulent software updates.
- Antivirus vendors have thoroughly analyzed NotPetya and can detect new variants.
Attempting to reboot NotPetya now would be difficult and risky. Additionally, the malware’s goal of inflicting wanton destruction (as opposed to financial gain) provides little incentive for attackers to restart such a campaign.
Ongoing Impact
While the NotPetya outbreak was short-lived, the malware continues to have lasting implications today. For example:
- Companies are still recovering financially from the massive costs of system downtime, data recovery, and rebuilding.
- Ukraine suffered long-term economic and infrastructure damage, which weakened their resilience to subsequent cyberattacks.
- The supply chain disruptions highlighted vulnerabilities in global interconnectedness.
- Businesses have invested heavily in security measures to guard against similar attacks.
- Ransomware remains a severe threat, with other worms like WannaCry using similar propagation techniques.
NotPetya also changed the cyber landscape by demonstrating the extreme destruction that is possible from a single piece of malware. This massive global crisis was spawned by just one initial infection in Ukraine. The episode highlighted how a few vulnerabilities can be exploited to cripple companies and countries.
As a result, cyber warfare and malware with “wiper” functionality have become a greater concern post-NotPetya. The attack showed that devastating effects can be achieved without access to advanced military resources.
Defense Against NotPetya-style Attacks
While NotPetya itself may be dormant, its tactics have informed subsequent cyberattacks and highlighted key security weaknesses. Here are some ways organizations can defend against similar worm-based ransomware threats:
- Keep all software up-to-date with the latest patches and updates.
- Exercise caution around software updates – verify authenticity before installing.
- Use antivirus, firewalls, and email scanning tools to block known attacks.
- Back up critical data regularly in offline locations.
- Segment networks to limit lateral movement between systems.
- Disable SMBv1, or limit its use to specific systems.
- Restrict administrator permissions and disable unused remote protocols.
- Test incident response plans and system restore procedures.
With strong technical defenses and user awareness, organizations can reduce their vulnerability to worm campaigns. However, no single solution can completely eliminate risk in the ongoing battle against malware.
Conclusion
The NotPetya outbreak of 2017 stands as arguably the most damaging malware attack to date. This aggressive worm crippled companies and infrastructure around the world through just a single point of entry in Ukraine.
Fortunately, NotPetya was quickly contained before the full extent of its destructive potential was realized. Ongoing patching, security awareness, and incident response preparations have rendered NotPetya obsolete as of today. However, the malware set a dangerous precedent in terms of scale and economic costs of cyberattacks.
Organizations must remain vigilant against the spread of ransomware, while managing vulnerabilities and planning for rapid response. By combining layered technical controls with tested crisis plans, companies can build resilience against the next generation of cyber threats. NotPetya may no longer be active, but its legacy has shaped defensive strategies in the never-ending battle to protect systems against malware.