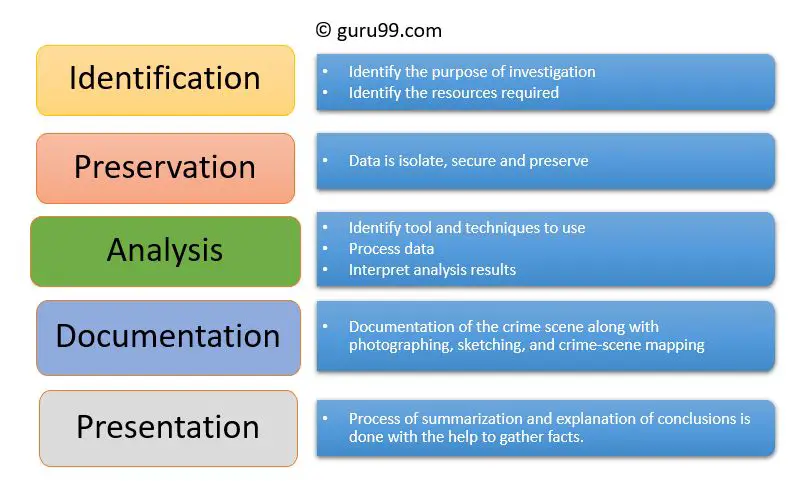
The digital forensics scientific process refers to the systematic approach followed by digital forensics experts to investigate cybercrimes and ensure the integrity of digital evidence. This process typically involves three key steps:
Step 1: Acquisition
The first step in the digital forensics process is to acquire the digital evidence. This involves identifying, collecting and preserving potential digital evidence while maintaining its integrity. Some key aspects of the acquisition phase include:
- Identifying sources of potential digital evidence like computers, mobile devices, networks, cloud storage etc.
- Using approved tools and techniques to collect the evidence without altering the original data.
- Ensuring proper chain of custody documentation for maintaining integrity of evidence.
- Preserving the state of digital devices by creating forensic duplicates/images.
- Collecting relevant contextual information about the systems and storage locations.
- Documenting the entire acquisition process as per standards.
Proper acquisition of digital evidence while avoiding contamination is critical as it lays the foundation for the rest of the investigation process. Failing to do so can make the evidence inadmissible in legal proceedings.
Step 2: Examination and Analysis
Once the potential digital evidence has been acquired, the next step is a systematic examination and in-depth analysis of the collected data. This involves:
- Recovering deleted, encrypted or corrupted files using forensic tools.
- Thoroughly combing through the evidence to identify artifacts and elements of interest.
- Categorizing the artifacts (emails, documents, images etc.) to determine their relevance.
- Analyzing metadata, logs, network traffic, registry entries etc. for clues.
- Establishing connections and timelines between various events and actions.
- Assessing whether additional analysis is needed by experts.
- Documenting the process with detailed analysis reports.
The examination phase focuses on extracting all possible relevant information from the acquired evidence. The analysis phase draws conclusions from this information to determine how events occurred and whether the findings implicate any individuals.
Step 3: Reporting and Presentation
The final step is to report the findings from the examination and analysis in a clear, comprehensive and coherent manner. The key aspects are:
- Summarizing the background, acquisition process and investigative methodology.
- Logically structuring and presenting the significant findings from analysis.
- Providing clear documentation such as timeline charts, data logs and forensic reports.
- Recommending improvement areas in policies, processes and technologies based on lessons learned.
- Preparing to communicate technical information to both technical and non-technical audiences.
The reporting phase converts the low-level forensic minutiae into an accessible narrative. This concise and consistent story can hold up in legal proceedings and steer executive decisions on actions to be taken.
Benefits of Following the Digital Forensics Process
Adhering to this systematic digital forensics process provides several benefits including:
- Preserving integrity of evidence – Meticulous acquisition and handling ensures evidence quality.
- Unbiased analysis and reporting – Standard methodology provides objectivity.
- Legal admissibility – Following forensic best practices enables court acceptance.
- Faster investigations – Structured process leads to efficient turnaround.
- Enhanced outcomes – Thorough examination supports accurate findings.
- Improved security – Lessons learned enable strengthening defenses.
Challenges in Digital Forensics Process
While following this standardized approach is advantageous, digital forensics experts also face some key challenges including:
- Expanding attack vectors – Investigating new technologies like IoT and cloud environments.
- Sophisticated anti-forensics – Advanced data hiding, obfuscation and tampering techniques.
- Encryption and passwords – Cracking encryption or accessing password protected data.
- Jurisdictional issues – Regulation differences across geographic boundaries.
- Volume and diversity of data – Huge data storage and various formats.
- Maintaining software/tools – Regularly updating to handle new systems and stay ahead of criminals.
By being aware of these challenges and continuing education, digital forensics experts can become even more effective at investigating cybercrimes.
Digital Forensics Standards and Frameworks
To promote consistency and agreement on best practices, several standards and frameworks have been developed to guide the digital forensics process. Some key examples include:
| Standard/Framework | Key Elements |
|---|---|
| ACPO Principles | Guidelines from UK’s Association of Chief Police Officers focusing on evidence integrity. |
| ISO/IEC 27037 | International standard covering identification, collection, acquisition and preservation of digital evidence. |
| NIST SP 800-86 | Guidance from US National Institute of Standards and Technology for digital forensics. |
| EC-Council Computer Forensics Model | Model covering acquisition, examination, analysis and reporting. |
| DFIRM | Digital forensic investigation framework focusing on preparation, incident response, data collection etc. |
Adoption of these standards lends credibility to the digital evidence and the forensic process. Organizations should ensure their practices align with proven guidelines and frameworks.
Role of Digital Forensics in Combating Cybercrime
Digital forensics is a crucial capability in the fight against cybercrime. By providing systematic and standards-based investigation capabilities, it enables:
- Detection, tracing and attribution of cyberattacks.
- Uncovering evidence like malicious code, breach footprints and insider activity.
- Establishing timelines and correlating evidence to attackers or their sponsors.
- Aiding legal prosecution and law enforcement actions against cyber criminals.
- Extracting cyber threat intelligence to bolster future defenses.
Without digital forensics, law enforcement would struggle to reliably track cybercriminals or bring them to justice. Digital forensics capabilities are thus vital for any effective cybersecurity program.
Skills Needed for Digital Forensics
Conducting digital forensic investigations requires a diverse skillset including:
- Computer and networking concepts – In-depth knowledge of IT systems, storage, cloud etc.
- Data recovery and analysis – Identifying hidden artifacts and reconstructing timelines.
- Software and programming – Using scripts and database queries to extract forensic data.
- Investigative ability -Asking right questions and piecing together evidence.
- Attention to detail – Careful evidence handling and documentation.
- Legal knowledge – Following protocols for submitting court-admissible reports.
Both foundational IT expertise as well as specialized forensic tools training are needed to become proficient. Hands-on lab practice is essential to develop practical investigative skills. Some common digital forensics certifications that can validate capabilities are Certified Computer Examiner (CCE), GIAC Certified Forensic Analyst (GCFA) and Certified Cyber Forensics Professional (CCFP).
Digital Forensics Tools
Digital forensics experts use a variety of software tools and technologies for acquiring, examining and analyzing evidence. Common tool categories include:
- Imaging tools – Hardware/software for forensic duplication of digital storage media. E.g. Tableau TD2u, Rapid Action Imaging Device (RAID).
- Analysis tools – Software to systematically search, categorize and recover forensic artifacts. E.g. Autopsy, Magnet AXIOM.
- File recovery tools – Tools for restoring deleted or corrupted files and partitions. E.g. Recuva, Foremost.
- Mobile forensics tools – Tools to extract data from mobile devices like smartphones. E.g. Oxygen Forensic Detective.
- Network forensics tools – Solutions for capturing and analyzing network traffic for forensic evidence. E.g. Wireshark.
- Specialized tools – Tools focused on areas like decryption, steganography detection, password cracking etc.
Leveraging both commercial and open source tools provides extensive evidence extraction capabilities. But human expert analysis is still needed to interpret results meaningfully. Tools should thus augment and not replace the digital forensics expert.
Types of Digital Evidence
Digital forensics examines many diverse sources of potential electronic evidence associated with cybercrimes or incidents. Common evidence types include:
- Computer data – Files, hard disks, slack space, memory, registry entries etc.
- Mobile devices – Call logs, messages, apps, location data from smartphones, tablets etc.
- Network activity – Firewall logs, intrusion detection data, packet captures, network flows.
- Database information – Audit logs, financial transactions, access records.
- Cloud data – Virtual machine images, access logs, application data from cloud infrastructure.
- IoT device data – Smart home device logs, embedded system memory, sensor readings.
- Digital multimedia – Security camera footage, audio recordings, image files.
Each source requires specialized tools and techniques to acquire and analyze appropriately while avoiding data corruption.
Best Practices in Digital Forensics
To ensure defensible and high-quality digital forensics, experts recommend some best practices including:
- Use forensic images not original evidence during analysis.
- Validate integrity via cryptographic hashes like MD5, SHA-1.
- Isolate analysis systems to avoid contamination.
- Document the chain of custody comprehensively.
- Record observations consistently and completely.
- Draw conclusions conservatively based on evidence.
- Provide clear opinions based on facts not assumptions.
- Follow standard operating procedures and methodologies.
- Stay up-to-date on tools, techniques and industry best practices.
Adhering to forensic best practices elevates the credibility and admissibility of the expert findings.
Careers in Digital Forensics
There is growing demand for digital forensics jobs across both public and private sectors, creating attractive career opportunities including:
- Law enforcement – Roles in police and government agencies to support cybercrime investigations.
- eDiscovery/Litigation support – Assist lawyers and legal teams with forensic evidence for cases.
- Incident response – Employed by organizations for timely forensic investigation of breaches and cyberattacks.
- Security analyst/engineer – Apply digital forensics as part of cyber threat detection and response.
- Consultants – Technical experts providing forensic analysis and testimony for clients.
With cyberattacks on the rise, demand for digital forensics expertise promises to accelerate. Specialized certification and hands-on experience will be key to starting and advancing in this exciting field.
The Future of Digital Forensics
Digital forensics faces growing opportunities and challenges as technology advances. Some key trends shaping the future of this field include:
- Harnessing artificial intelligence and machine learning to automate evidence analysis and enhance detection of anomalies.
- Adapting to new technologies like 5G networks, drones, VR/AR systems and advanced IoT environments.
- Developing capabilities to handle analysis of massive volumes of data from enterprise and cloud sources.
- Employing sophisticated analytics to identify behavioral patterns, timelines and systemic issues.
- Overcoming anti-forensics like disk wiping, encryption and evidence tampering via technical and legal means.
- Expanding scope from individual endpoint analysis to comprehensive approaches encompassing networks, databases, applications and users.
As technology shifts, so will digital forensics. But its fundamental pillars of evidence integrity, rigorous methodology and expert analysis will remain critical for the future. With adequate investment in skills and solutions, digital forensics will continue enabling cybercrime prevention and response for years ahead.