Digital forensics is the process of uncovering and interpreting electronic data for use as evidence in legal proceedings. The goal of digital forensics is to perform a structured investigation while maintaining a documented chain of evidence to find out exactly what happened on a digital device and who was responsible for it.
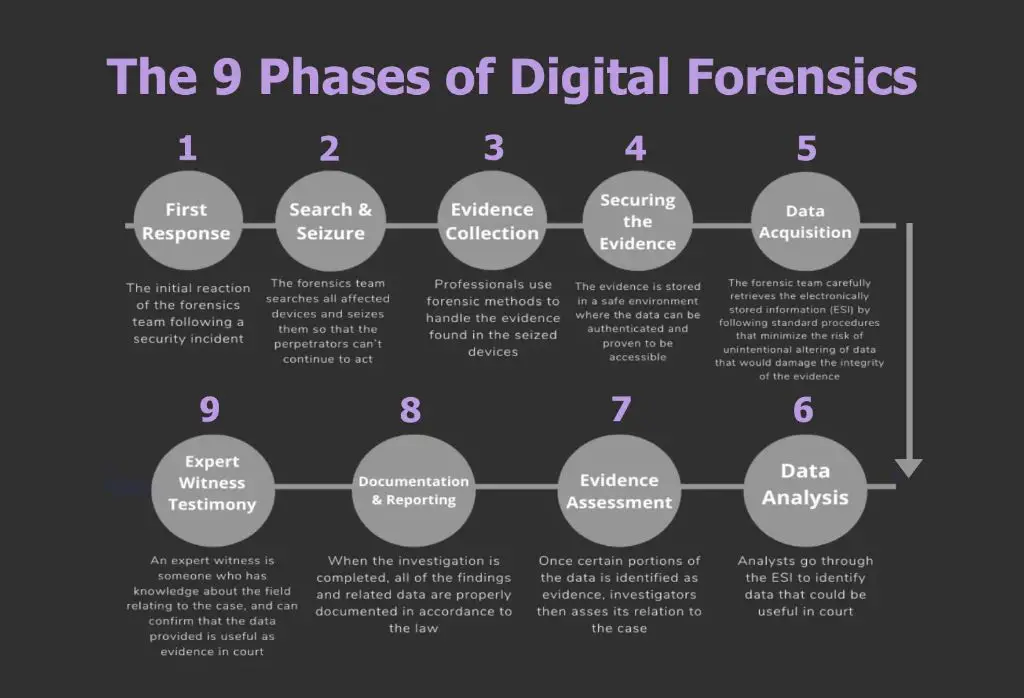
There are four main phases in the digital forensics process:
- Acquisition – identifying, labeling, recording, and acquiring data from the relevant sources, while following guidelines to ensure the data’s integrity is preserved.
- Examination – forensically examining the collected data through data reduction to find relevant facts.
- Analysis – analyzing the results of the examination phase to determine their significance to the case.
- Reporting – reporting the digital forensic findings including processes, procedures and conclusions in a formal report.
Understanding these phases and how digital forensic investigations are conducted is crucial for any cybersecurity or legal professional working with digital evidence.
Acquisition
The acquisition phase involves securing and obtaining data from digital devices and storage media that may contain evidence relevant to the investigation. Proper procedures must be followed to ensure the integrity of the data is maintained. This typically involves imaging or making forensic copies of storage media, such as hard drives, thumb drives, and mobile devices.
Imaging creates an exact bit-for-bit copy of the original data. Specialized tools and hardware write blockers are used to prevent altering the original during imaging. Strict procedures document each step taken to acquire the data. Cryptographic hash values like MD5 or SHA-1 are calculated on the original data and compared to values for the forensic copy to verify integrity.
Meticulous documentation tracks all hardware, software, procedures, notes, and other details related to acquiring the digital evidence. This provides a court-admissible chain of custody record. Following best practices for imaging, hashing, and documentation helps ensure the data integrity is maintained for examination and analysis.
Examination
The examination phase involves extracting and analyzing data from the sources acquired in the previous step. Examiners use various tools and techniques to uncover artifacts and reconstruct timelines of system activity (Source). Some key activities in this phase include:
- Extracting active, archived, and deleted files using forensics tools like EnCase or FTK.
- Carving out data from unallocated disk space to uncover deleted content.
- Analyzing filesystem metadata like access timestamps to build a timeline.
- Looking for evidence of antiforensics like data wiping, encryption, or steganography.
- Recovering and analyzing internet history, chat logs, emails, and other communications.
- Identifying relationships between artifacts to understand the full context.
Timeline analysis is crucial for reconstructing the sequence of events and correlating different pieces of evidence. Examiners carefully document their findings and begin forming hypotheses about the nature of the incident.
Analysis
The analysis phase involves examining the data collected during the examination phase to find specific evidence related to the case. This often involves data mining techniques to identify patterns and reconstruct the sequence of events. According to https://ermprotect.com/blog/what-are-the-5-stages-of-a-digital-forensics-investigation/, examiners will mine the data “looking for specific types of evidence that relate to the particular case.”
Some of the key aspects of the analysis phase include:
- Looking for incriminating or exonerating evidence relating to the specific case
- Using data mining and analytics techniques to identify relevant patterns in large datasets
- Reconstructing timelines of events based on file metadata, system logs etc.
- Correlating evidence from multiple sources to validate findings
- Interpreting and contextualizing findings based on the specifics of the case
The analysis requires expertise to interpret technical evidence and piece together the sequence of events relevant to the case. According to https://www.bluevoyant.com/knowledge-center/understanding-digital-forensics-process-techniques-and-tools, the examiner must “prove or disprove theories” based on the evidence uncovered during examination. The end goal is to prepare the forensic findings to stand up to legal scrutiny in the courtroom.
Reporting
The final phase in the digital forensics process is reporting. The investigator documents all findings from the examination and analysis stages in a report. This formal report serves as the official record of the investigation and evidence discovered. Some key aspects of the reporting phase include:
Documenting findings – The report should provide a clear, factual account of the discoveries made during the investigation. This includes documenting all relevant details about deleted files, internet history, system artifacts, timeline of events, incriminating communications or images, and any other pertinent evidence.
Preserving chain of custody – The report should maintain a detailed chronological log of any evidence collected and how it was handled, in order to prove its authenticity. This chain of custody verifies the integrity of the evidence.
Expert witness testimony – The digital forensic investigator who authors the report often serves as an expert witness if the case goes to trial. Their testimony explains technical details from the report in terms a judge and jury can understand.
Providing analysis and conclusions – Beyond just reporting the facts, the investigator draws qualified conclusions about the significance of the evidence and how it relates to the original objectives of the investigation.
Case closure – The final report allows stakeholders to review the findings, determine next steps, and officially close the case. This report becomes the permanent record of the investigation process and outcome.
(Citation)https://ermprotect.com/blog/what-are-the-5-stages-of-a-digital-forensics-investigation/
Tools
Digital forensics experts utilize a variety of hardware and software tools during the different phases. Some common tools include:
Acquisition phase:
- Hardware write blockers like Tableau T35es Forensic Bridge (https://www.techtarget.com/searchsecurity/tip/Digital-forensics-tools-experts-use)
- Forensic disk imagers like FTK Imager (https://en.wikipedia.org/wiki/List_of_digital_forensics_tools)
Examination phase:
- Forensic analysis software like Autopsy (https://www.bluevoyant.com/knowledge-center/get-started-with-these-9-open-source-tools)
- Password cracking tools like Hashcat
Analysis phase:
- Data carving utilities like Foremost
- Anti-forensics tools like Timestomp
Reporting phase:
- Report generation tools like Belkasoft Evidence Center
There is a mix of proprietary tools like EnCase and Cellebrite UFED, as well as open source options like Sleuth Kit and Volatility (https://www.bluevoyant.com/knowledge-center/get-started-with-these-9-open-source-tools). The choice depends on budget, features needed, and personal preference.
Best Practices
There are several best practices that digital forensics experts follow to ensure the integrity and admissibility of evidence. Maintaining a clear chain of custody is crucial – there should be detailed documentation of how evidence was collected, transported, analyzed and stored at all times (Standards and best practices for digital forensics). Verification of data is also important through methods such as hashing. Ethics must be adhered to, including objectivity, transparency, and confidentiality.
Best practices also include using court-tested tools and methods, following standard operating procedures, undergoing regular proficiency testing and training, and obtaining certification (e.g. EnCE) (Best Practices In Digital Evidence Collection). Documentation should be comprehensive and include notes, photographs, chain of custody logs and technical diagrams. Evidence should be preserved in its original state as much as possible.
Challenges
Digital forensics investigators face several key challenges that can impede investigations:
Encryption – Increased use of encryption poses a major obstacle, as investigators may be unable to decrypt data without the proper keys. This limits the ability to recover evidence (Splunk, 2023).
Anti-forensics – Criminals use anti-forensic techniques like data hiding, trail obfuscation, and evidence destruction to cover their tracks. This requires investigators to use more advanced methods to uncover digital evidence (CISOMAG, 2023).
Large data volumes – The massive volumes of data that must be analyzed and correlated makes digital forensics more resource and time intensive. Investigators must use tools like data triage to handle terabytes or petabytes of data efficiently (DFRWS, 2023).
Legal constraints – Digital forensics must operate within legal bounds related to search warrants, data privacy, jurisdiction, and admissibility. Investigators must follow strict protocols to ensure evidence integrity and compliance (CISOMAG, 2023).
Case Studies
Real world examples provide important insights into how digital forensics is applied in practice. According to a case study from Magnet Forensics, federal agencies have leveraged digital forensics to conduct thorough investigations, such as a case featuring William Stumme, Senior Forensic Examiner of Surefire Cyber (https://www.magnetforensics.com/resource-center/case-studies/).
Another case study from Anomali outlined how their team analyzed a retailer’s site and discovered a sophisticated custom attack used to steal credit card data (https://www.linkedin.com/pulse/digital-forensics-case-study-involving-retail-credit-card). Real world examples like these provide valuable insights into digital forensics best practices.
Additionally, a case study compilation from the National Education Network provides an overview of digital forensics perspectives, methodologies, and sample cases (https://bcuassets.blob.core.windows.net/docs/sndigitalforensics-casestudies-131067565675145068.pdf). By examining diverse case studies, key challenges, approaches, and learnings can be identified.
Conclusion
In summary, digital forensics involves four key phases – acquisition, examination, analysis, and reporting. Collecting and preserving digital evidence properly is crucial in the acquisition phase to ensure its admissibility in legal proceedings. The examination phase involves extracting and assessing the relevant data. Analysis utilizes various techniques and tools to interpret the evidence and recreate the sequence of events. Finally, the investigator documents the findings and processes in a forensic report.
The future of digital forensics looks promising yet challenging. As technology continues to advance rapidly, there is a growing need for more automated tools leveraging AI and ML to help investigators keep pace and efficiently handle large volumes of data 1. However, maintaining data integrity and validation of automated processes is crucial. Collaboration between law enforcement, researchers, and technology vendors will be key in developing best practices and standards for the evolving landscape of digital forensics.