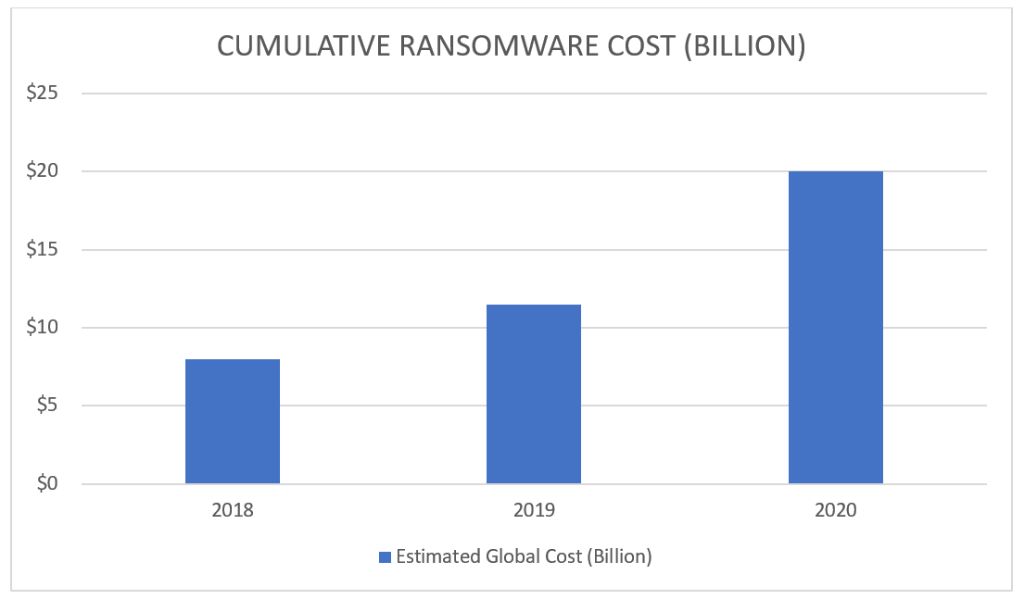
Ransomware attacks have been on the rise in recent years, with criminals using malicious software to encrypt victims’ files and demand large sums of money to decrypt them. Some of the ransom amounts demanded have totaled millions of dollars. Here we look at the 5 biggest confirmed ransomware payouts to date.
What is ransomware?
Ransomware is a form of malicious software or malware that encrypts files on a victim’s computer or network. The attackers then demand a ransom payment in cryptocurrency, such as Bitcoin, in exchange for decrypting the files. If the ransom is not paid, the files remain encrypted and inaccessible.
Ransomware attacks often target businesses, hospitals, and government agencies where access to files and data is critical. By locking these entities out of their systems, the attackers create enormous pressure to pay the ransom to resume operations. The average ransomware payment in 2021 was over $800,000, a 171% increase from 2020.
Biggest known ransomware payouts
Here are the 5 biggest publicly reported ransomware payments to date:
1. Colonial Pipeline – $4.4 million
In May 2021, a ransomware attack shut down the Colonial Pipeline, which supplies nearly half the fuel consumed on the U.S. East Coast. The operators paid a ransom of 75 Bitcoin, then worth around $4.4 million, to regain control of systems. The attack led to fuel shortages and panic buying across the region.
2. JBS – $11 million
Just weeks after the Colonial attack, ransomware criminals hit JBS, the world’s largest meat processing company. The Brazil-based company disclosed that it paid an $11 million ransom in Bitcoin to prevent further disruption and get its plants operational again.
3. CNA Financial – $40 million
In March 2021, CNA Financial, one of the largest insurance companies in the U.S., was hit by a Phoenix CryptoLocker ransomware attack. The company later admitted to paying a $40 million ransom, the largest confirmed payout at the time.
4. MediaMarkt – $240 million
In November 2022, German retailer MediaMarkt was hit by a Hive ransomware attack. The group demanded $240 million to decrypt the company’s systems. MediaMarkt has not confirmed if the full amount was paid.
5. Acer – $50 million
Taiwanese electronics giant Acer was attacked by the REvil ransomware gang in March 2021, with the criminals demanding $50 million. Acer has not officially confirmed if the ransom was paid.
Notable mentions
Some other large, unconfirmed ransomware payments include:
- Brenntag – $4.4 million
- University of California – $1.14 million
- Axa Asia – $20 million
Many ransomware payments go unreported, so it’s likely even larger payouts have been made. The criminals often negotiate payments and offer victims discounts for quick payment.
Why do companies pay ransoms?
There are several reasons organizations agree to pay ransoms, even with FBI advice not to pay:
- To quickly restore IT systems and resume business operations
- If backups are inadequate or non-existent
- To prevent sensitive company data or customer info from leaking online
- If cyber insurance policies agree to cover the ransom payment
Paying the ransom is seen as the most efficient way to mitigate damage and recover files, although it encourages further criminal ransomware activity.
Steps organizations can take
Companies can take several steps to improve ransomware resilience, including:
- Backing up data regularly and keeping backups offline
- Installing security software to detect malware and unauthorized access
- Using email filtering to block phishing attacks that deliver ransomware
- Educating employees on cybersecurity best practices
- Limiting user permissions and access controls
- Developing an incident response plan for attacks
Improving overall cyber hygiene and defense can help reduce the risk and impact of ransomware incidents.
Recent trends
Some recent ransomware trends include:
- Ransom amounts increasing dramatically, into the millions of dollars
- Shift from “big game” hunting of large organizations to targeting mid-size companies
- Triple extortion tactics combining encryption, data theft, and DDoS attacks
- Ransomware-as-a-service model allowing greater access
- Cryptocurrency enabling hard-to-trace ransom payments
Cybercriminals continue to innovate their techniques, requiring organizations to take ransomware threats seriously and invest in robust defenses.
Impact of ransomware payments
Paying ransoms has several effects:
- Incentivizes more attacks as a profitable criminal enterprise
- Funds development of more ransomware tools and infrastructure
- Drives up average payment amounts
- Puts organizations at further risk of repeat attacks
- May violate regulations prohibiting payments to sanctioned entities
There are also ethical considerations in paying ransoms. While it may help the victim recover files, rewarding criminal acts can encourage further damaging attacks globally.
Law enforcement efforts
Law enforcement is ramping up efforts to combat ransomware, including:
- FBI forming a new ransomware task force
- Department of Justice creating a ransomware specific task force
- Coordinated global law enforcement operations to identify attackers
- Sanctioning crypto exchanges that launder ransomware funds
- Seizing ransomware extortion profits
However, the decentralized nature of attackers and anonymizing methods makes enforcement challenging. More international cooperation is needed to crack down on safe havens for ransomware criminals.
Conclusion
Ransomware presents a severe, growing threat to organizations as evident in the multi-million dollar payouts to date. Companies must take concrete steps to enhance security and prevent successful attacks. Paying ransoms should be an absolute last resort, but many victims feel compelled to pay for data recovery and business continuity.
Global law enforcement efforts need bolstering to deter ransomware groups, cut off criminal profits, and avoid incentivizing further attacks. Ultimately, reducing the financial incentives and increasing the risk to attackers is essential to curtailing the soaring impact of ransomware.