Digital forensics is the process of collecting, analyzing, and presenting digital evidence in a legal setting. It involves extracting data from digital devices and recovering deleted, encrypted, or damaged file information to be used as evidence in civil or criminal cases. A digital forensics investigation typically follows a standard set of procedures to ensure the integrity of the evidence.
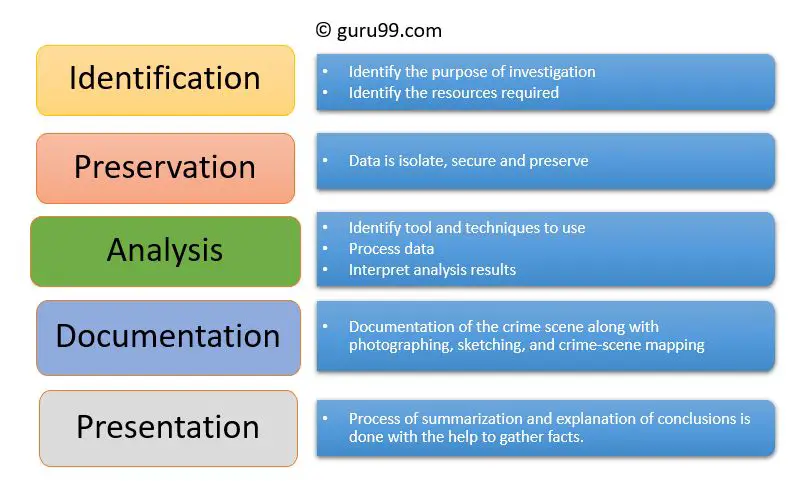
A digital forensics investigation goes through several key phases: identification, preservation, collection, examination, analysis, presentation and reporting of the findings. Properly following these systematic steps preserves the integrity of the digital evidence and ensures its admissibility in legal proceedings.
Briefly, a digital forensics investigation starts with identifying sources of potential digital evidence relevant to the case. The devices and data are then preserved in their original state through forensic imaging. The relevant data is collected, examined thoroughly, analyzed for significant information, and finally presented as evidence in court or in an investigation report.
Identification
The identification stage is the first step in the digital forensics investigation process. This involves recognizing that an incident or crime involving digital devices and technology has likely occurred (Quizlet, 2022). The investigator must identify the potential sources of evidence, considering all the possible storage locations and formats of the digital data. They look for signs of unauthorized access or cybersecurity breaches across the compromised network or devices. The scope of the incident is determined, along with applicable laws and regulations. Potential stakeholders like IT security staff may be consulted to help identify issues.
Once a security incident or cybercrime is suspected, the investigator identifies systems, devices and users involved to determine where evidence may reside. This analysis guides the next steps of preserving and collecting relevant data sources (Dataconomy, 2022). Identification sets the stage for a thorough and legally-compliant investigation.
Preservation
The preservation stage involves isolating, securing, and preserving digital evidence without altering its state. Proper preservation is crucial to maintain the integrity and admissibility of evidence. Key steps include:
Powering down devices according to best practices – abruptly cutting power can damage evidence. Guidelines recommend removing batteries and plugs then bagging devices to transport to the lab (GeeksforGeeks, 2020).
Using write blockers – hardware or software that prevents writing to storage media. This prevents accidentally modifying data (Critical Insight, 2021).
Creating forensic images – exact copies of storage media created without altering the original. Images maintain data integrity for analysis (Realtime Networks, 2021).
Using cryptographic hashes – mathematical fingerprints verifying the forensic image matches the original byte-for-byte.
Proper chain of custody – meticulously tracking who handles evidence to show it wasn’t tampered with.
Following best practices preserves digital evidence for analysis and presentation in court.
Collection
The collection phase involves systematically gathering evidence from all potential sources while maintaining integrity. Proper collection procedures are crucial as evidence can easily be altered, damaged, or destroyed if not handled correctly. Investigators should use forensically sound methods to duplicate data, ensuring the original is unaltered, and establish a thoroughly documented chain of custody. Devices and storage media need to be handled properly to avoid accidental changes. For digital evidence, collection typically involves making a forensic image or copy of a hard drive or device.
According to the Axon article “What Law Enforcement Should Know About Collecting Digital Evidence,” it is important to use specialized tools and techniques to collect digital evidence without altering the original data source. Investigators should also document each step and keep detailed notes about how evidence is collected. The UNODC recommends only trained personnel should collect digital evidence as improper collection can render evidence inadmissible in court.
Examination
The examination stage involves forensically analyzing the evidence that was collected and preserved. This is done using specialized forensic tools and techniques to extract data for analysis. The goal is to uncover information that is relevant to the investigation while preserving the integrity of the original data (https://www.ojp.gov/pdffiles1/nij/199408.pdf, pages 5-10). The examination may involve reconstructing deleted or damaged files, decrypting encrypted data, recovering hidden or obfuscated data, and validating the internal integrity of files. Proper forensic procedures must be followed such as working on copies of evidence rather than originals, to avoid altering the evidence. The tools and techniques used will depend on the type of device or media being examined ( https://www.ojp.gov/ncjrs/virtual-library/abstracts/digital-evidence-standards-and-principles).
Analysis
In the analysis stage, investigators thoroughly examine the collected digital evidence to assess and interpret its significance to the case (Digital Evidence: How It’s Done). This involves carefully combing through the copied data to identify and extract information relevant to the investigation. The process can be extremely tedious and time-consuming, especially when dealing with large volumes of data.
Investigators use a variety of specialized forensic tools and techniques to analyze different types of digital evidence. For example, decryption may be necessary to read encrypted files, while data carving can help recover deleted files. The key is having the right skills and tools to properly decode and interpret the digital information (Issues in Digital Evidence: Risks, Prevention & Protection).
At this stage, the focus is on assessing the evidence to determine how it fits into the timeline of events, corroborates or contradicts theories, and ultimately builds a comprehensive understanding of what occurred. The end goal is to extract probative information from the raw data that will help prove or disprove allegations relevant to the case.
Presentation
The presentation stage involves documenting and presenting the findings from the digital forensics investigation. The investigator prepares a report that thoroughly details the examination process, analyses conducted, tools used, and conclusions reached. According to the Digital Forensics Process by CEMCA (source), the report should include:
– A detailed description of the evidence examined
– An explanation of the tools, techniques, and procedures used during the analysis
– The investigator’s observations, interpretations, and conclusions
– Visual representations of important findings like timelines or data relationships
The presentation aims to communicate technical details clearly to both technical and non-technical audiences. Investigators may present findings in person, in written reports, or through multimedia presentations. The presentation helps stakeholders understand the significance of the evidence and how it relates to the original objectives of the investigation.
Decision
The decision stage involves making conclusions based on the evidence analyzed during the examination phase. The examiner must interpret the results of the analysis and determine if the findings support any hypotheses or address the original objectives of the investigation (James, 2013). This stage requires the examiner to weigh the evidence carefully and avoid confirmation bias by remaining objective. The final conclusions should directly correlate to the facts revealed through examination and analysis (Sunde, 2021).
Key aspects of the decision stage include:
- Making impartial conclusions based on the evidence
- Avoiding biases that could influence interpretation of results
- Ensuring any claims or hypotheses are fully supported by facts and findings
- Maintaining comprehensive documentation to justify conclusions
- Drawing reasoned conclusions limited to what the evidence allows
Proper decision making relies on the examiner’s expertise and ability to logically connect the evidence to reasonable conclusions (James et al., 2013). Reliable and ethical conclusions help ensure the integrity of the entire investigation process.
Admission
Admission refers to the process of submitting digital evidence to the court record so it can be considered during the legal proceedings (Shukla, 2023). For digital evidence to be admissible in court, it must be relevant, authentic, and obtained legally. However, challenges arise due to the technical nature of digital evidence.
To admit digital evidence, investigators must be able to explain how it was collected, preserved, and examined in a forensically sound manner. The party submitting the evidence bears the burden of proving its authenticity and reliability. Additionally, proper chain of custody procedures must be followed to demonstrate the evidence was not tampered with.
Judges act as gatekeepers regarding the admissibility of digital evidence. They assess factors such as whether the correct forensic procedures were followed and if the evidence is hearsay. Authentication of digital evidence can be difficult due to issues like spoofing attacks or metadata manipulation.
Overall, great care must be taken when admitting digital evidence to maintain its integrity and probative value. Investigators should thoroughly document their collection and examination processes. Standardized procedures for submitting digital evidence may help address legal challenges and streamline the admission process (Shukla, 2023).
Prosecution
The final stage of digital forensics investigation involves using the collected evidence to build a legal case and prosecute the suspect in court. The role of the investigator shifts from gathering and analyzing data to preparing reports and presentations that effectively communicate findings to legal teams, judges, and juries. According to the Association of Certified E-Discovery Specialists (ACEDS) 2022 conference brochure, “Prosecutors are increasingly faced with managing large amount of digital data and using that data effectively at trial to present a clear and persuasive case.”
Key aspects of the prosecution stage include:
- Summarizing the investigation in an investigative report.
- Preparing exhibits to use as evidence in court.
- Developing effective visual aids and presentations.
- Testifying as an expert witness on the investigation process, findings, and implications.
- Assisting prosecutors in understanding complex technical evidence and using it to construct arguments.
- Highlighting connections between multiple pieces of digital evidence to reveal a sequence of events or build a theory of the crime.
Ultimately, the goal is to leverage the preserved, collected, and examined evidence to prove unlawful activity, establish motives and means, and attribute actions to specific suspects in order to obtain a conviction. Meticulous documentation and clear communication of the investigation process and conclusions are crucial.