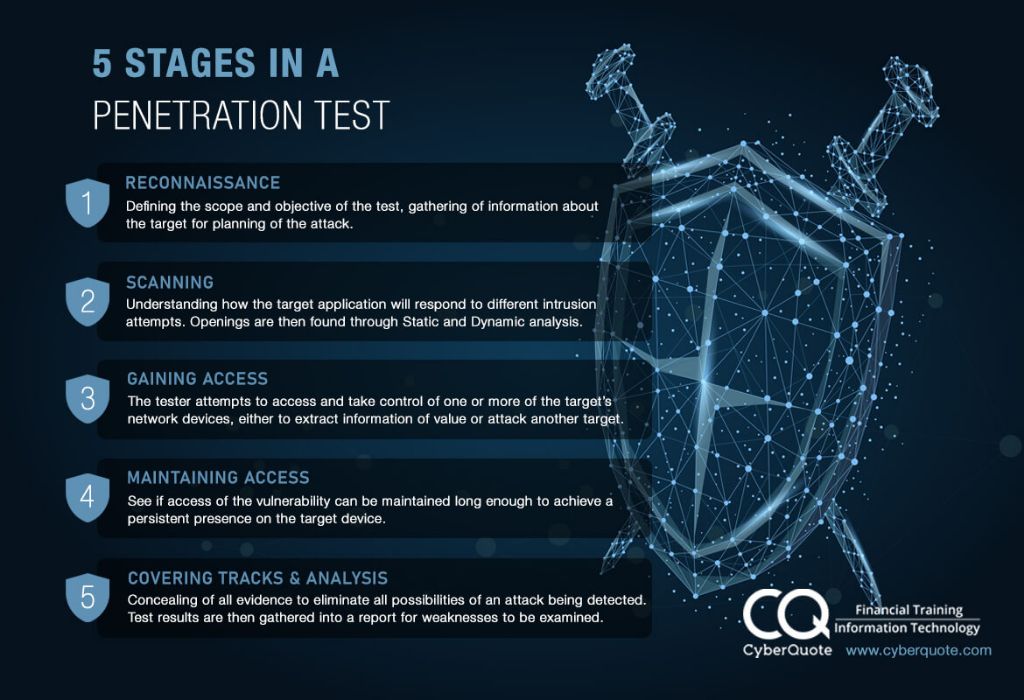
Penetration testing, also known as pen testing or ethical hacking, is the practice of testing a computer system, network or web application to find security vulnerabilities that an attacker could exploit. The goal of penetration testing is to identify security weaknesses before malicious hackers can detect and compromise the system. Penetration testing involves using the same tools and techniques that hackers employ to breach security controls and gain unauthorized access to systems and data. The insights gained from penetration tests allow organizations to fix vulnerabilities and strengthen their cyber defenses. There are generally 5 stages or phases to a comprehensive penetration test:
Stage 1: Planning
The planning stage is crucial for defining the scope, goals, timing, rules of engagement and success criteria for the penetration test. Key activities in test planning include:
- Defining the scope and boundaries of systems, networks and applications to be tested.
- Identifying the purpose and goals, such as meeting compliance requirements, assessing a new system, or hardening security defenses.
- Determining the type of tests to conduct, such as network, application, social engineering, wireless, etc.
- Creating a schedule for tests that minimize disruption to business operations.
- Establishing rules of engagement that specify the levels of probing allowed, out-of-bound conditions and process for escalation.
- Deciding on a reporting methodology and defining metrics for success.
- Coordinating with affected parties to ensure they understand the nature and timing of testing activities.
Careful planning sets the stage for an effective penetration test that delivers valuable findings while avoiding issues from poorly scoped or scheduled tests. The planning phase involves discussions between the penetration testing team and key stakeholders within the organization to ensure alignment on the goals, timing and rules of engagement.
Stage 2: Reconnaissance
The reconnaissance or information gathering stage involves learning as much as possible about the target systems and environments before attempting exploitation. Reconnaissance aims to build an accurate map of the scope and vulnerabilities that exist within the tested infrastructure. Key reconnaissance activities include:
- Confirming the scope of IP addresses, domain names, networks segments and applications in scope.
- Mapping out trusted connections between systems, such as VPNs and partner networks.
- Identifying domain names, mail servers, user accounts and other assets associated with the target.
- Performing DNS queries, zone transfers and open source research to find information about the target.
- Scanning ports and services using nmap and other tools to profile the network.
- Fingerprinting operating systems and detecting vulnerabilities with automated scanning tools like Nessus.
- Enumerating user accounts, shares, databases and other application elements.
The more comprehensive the reconnaissance, the better prepared the tester will be to find and exploit vulnerabilities within the subsequent stages of the penetration test.
Stage 3: Scanning and Vulnerability Detection
The scanning phase involves the active probing and analysis of systems to detect vulnerabilities such as unpatched software flaws, misconfigurations, and weak passwords. This stage goes deeper than the reconnaissance conducted earlier to discover specific security gaps that may be exploited. Common scanning and vulnerability detection activities include:
- Scanning for vulnerabilities with automated tools like Nessus, OpenVAS and Qualys.
- Analyzing misconfigurations on servers through default or missing security settings.
- Assessing patch levels on operating systems and applications.
- Detecting weak passwords and insecure access controls.
- Scanning source code for security flaws within custom web applications and software.
- Evaluating mobile applications for data leakage issues.
- Conducting password cracking attacks through brute force, dictionaries and rainbow tables.
The list of vulnerabilities yielded from scanning provides a blueprint for the later penetration and post-exploitation stages where the goal is to demonstrate weaknesses through active compromise of systems.
Stage 4: Exploitation
The exploitation phase involves penetration testers actively compromising and demonstrating the impact of vulnerabilities found earlier through reconnaissance and scanning activities. Once a vulnerability is confirmed, it will be exploited using tools and techniques similar to those of real world attackers. This stage allows an organization to understand the true business risk of security flaws based on their exploitability and potential impact. Common exploitation activities include:
- Gaining unauthorized access to systems by exploiting unpatched software vulnerabilities.
- Escalating privileges to gain administrator or root access on compromised machines.
- Extracting password hashes and cracking them offline to reveal plaintext passwords.
- Hijacking user sessions and accounts using password cracking or credential theft.
- Demonstrating the impact of denial of service attacks against infrastructure.
- Proving data exfiltration of sensitive information is possible.
- Pivoting through trusted connections and lateral movement between systems.
- Compromising backend and database servers housing sensitive data.
Actual exploitation demonstrates the extent to which threats can spread internally and impact critical business systems, rather than just highlighting theoretical vulnerabilities. However, exploitation activities must occur in a responsible manner adhering to agreed rules of engagement to avoid outages or damage.
Stage 5: Reporting and Remediation
The final phase of penetration testing focuses on documenting findings, presenting results and guiding remediation of security issues. The reporting stage includes the following key activities:
- Documenting all relevant details about vulnerabilities found and exploited during testing.
- Summarizing the key findings, risks, and recommendations for management in a high-level report.
- Presenting the results to key stakeholders within the organization.
- Providing technical vulnerability details and evidence to the security operations team.
- Helping plan and prioritize remediation roadmaps to address weaknesses.
- Validating that vulnerabilities have been remediated through retroactive testing.
- Highlighting residual risk where remediation may not be feasible.
The goal is to educate the organization about risks and encourage prompt remediation of vulnerabilities. Successful remediation will strengthen the organization’s security posture against the threats modeled by the penetration test.
Conclusion
In summary, penetration testing is conducted in 5 main phases including planning, reconnaissance, scanning, exploitation, and reporting. Planning sets the scope and rules. Reconnaissance gathers information about the target. Scanning detects potential vulnerabilities. Exploitation demonstrates vulnerabilities through compromise. Finally, reporting presents insights that allow the organization to remediate weaknesses and improve security defenses against real-world attacks.
A well-planned and thorough penetration test spanning these 5 stages will provide invaluable results to enhance an organization’s cybersecurity posture while identifying areas for security improvements. With persistent and sophisticated threats attacking businesses today, penetration testing offers a proactive way to evaluate an organization’s security controls before attackers attempt their own unauthorized penetration.