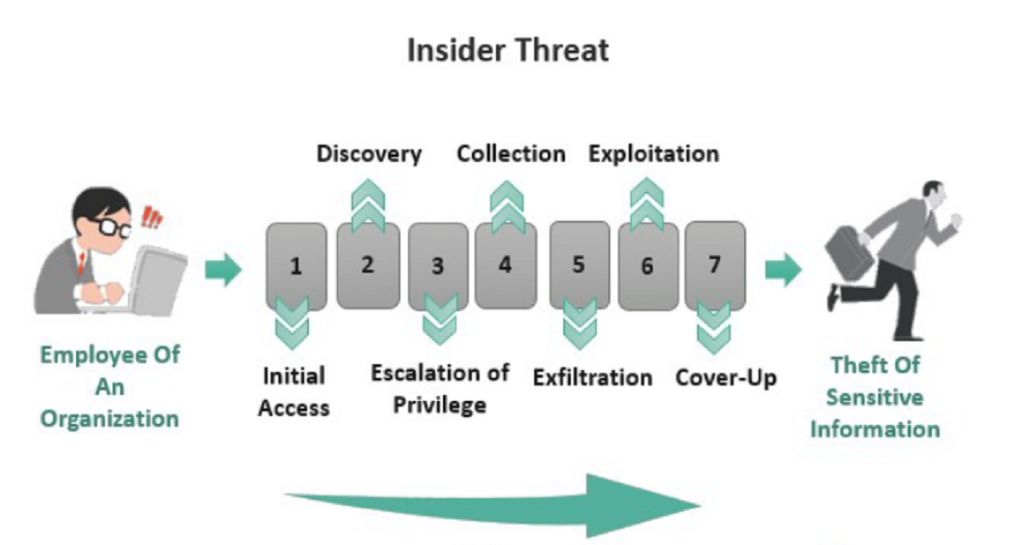
Insider threats refer to security breaches that originate from within an organization, typically by employees or contractors who have authorized access to sensitive data and systems. There are two main types of insider threats that organizations need to be aware of and protect against: malicious insiders and accidental insiders.
Malicious Insiders
Malicious insiders intentionally steal, modify, delete, or expose an organization’s confidential or proprietary information. They may be motivated by financial gain, revenge against the company, or ideology. Some examples of malicious insider threats include:
- Employees who sell trade secrets or customer data to competitors
- Disgruntled employees who delete or corrupt data and systems before leaving a company
- Insiders who exfiltrate confidential documents and emails toexpose perceived corporate wrongdoing
- Moles or double agents who are recruited by rival companies or foreign governments to collect sensitive information from the inside
Malicious insiders have intimate knowledge of a company’s systems, policies, and vulnerabilities. They often have access privileges that allow them to easily circumvent security controls. As a result, malicious insider attacks can cause severe financial, operational, and reputational damage.
Motivations for Malicious Insider Attacks
There are several common motivations behind malicious insider cyber attacks:
- Financial Gain: Selling proprietary data and trade secrets can be extremely lucrative for insiders. Even small pieces of information can fetch high prices from competitors, especially in industries like finance and technology.
- Ideology: Some insiders launch attacks to embarrass or disrupt an organization whose ethics or business practices they disagree with. Examples include leakers who expose corporate wrongdoing.
- Revenge: Disgruntled employees may seek vengeance for perceived mistreatment such as termination, lack of promotion, or workplace conflicts. Sabotaging systems and destroying data can help them get even before leaving.
- Espionage: Insiders may secretly collect proprietary information to advance the interests of another company or foreign government. Millions are spent recruiting corporate moles and double agents.
- Thrill Seeking: Certain malicious insiders attack systems for the challenge, excitement, or social recognition from the hacker community. It satisfies their curiosity and need for power.
Examples of Malicious Insider Cyber Attacks
Some notable examples of insider attacks include:
- Edward Snowden – The former NSA contractor leaked a massive trove of classified documents about government surveillance programs.
- Chelsea Manning – The Army soldier shared hundreds of thousands of military and diplomatic documents with WikiLeaks.
- Anthony Levandowski – The ex-Google engineer allegedly downloaded over 14,000 proprietary files before leaving to start a competing autonomous vehicle company.
- Dongfan “Greg” Chung – The former Boeing engineer was caught passing space shuttle secrets to China.
- Sherry Cohen – The IT contractor caused a 16-hour outage at Canadian telecom Telus after her contract was terminated.
Accidental Insiders
In contrast to malicious insiders, accidental insiders do not have malicious intent. They unintentionally expose confidential data or enable security breaches through careless behavior, lack of security training, or social engineering attacks. Examples of accidental insider threats include:
- Employees who fall for phishing scams and divulge passwords or other sensitive data
- Staff who improperly dispose of documents containing proprietary information
- IT personnel who misconfigure security settings or leave systems vulnerable
- Workers who access company data on untrusted WiFi networks
- Those who lose mobile devices containing unencrypted corporate data
Accidental insider threats often go unnoticed but can still cause serious security incidents. Even without malicious intent, insiders can still inflict extensive damage through negligence and violating security best practices.
Causes of Accidental Insider Threats
Why do accidental insider threats occur? Some of the most common causes include:
- Lack of security training – Employees may not understand policies, procedures, proper data handling, and how to identify risks.
- Complex systems – Sophisticated IT environments are prone to misconfigurations that create vulnerabilities.
- Dangerous applications – Staff who install unauthorized apps or disable security controls raise the risk.
- Unsafe practices – Bad habits like password reuse or accessing public WiFi open the door to compromise.
- Social engineering – Even experts fall victim to skillfully crafted phishing emails and persuasion tactics.
- Unsecured devices – Lost or stolen laptops and mobile phones frequently contain unencrypted data.
- Excess privileges – Overly broad access rights can allow mistakes or snooping to go undetected.
- Lax compliance – Failing to follow security policies leads to more incidents.
Impacts and Damages
Both malicious and accidental insider threats can severely impact organizations in multiple ways, including:
- Financial losses – Stolen data and IP, disruption of operations, and costs to recover can add up to millions of dollars.
- Loss of competitive advantage – Data exfiltration erodes trade secrets and hard-won business differentiators.
- Regulatory non-compliance – Data breaches may violate regulations like HIPAA, GDPR, and state privacy laws.
- Legal liability – Negligence suits and fines from regulators create additional expenses.
- Negative publicity – Public breach notifications damage brand reputation and customer trust.
- Operational disruption – Outages of business-critical systems lead to loss of productivity and revenue.
- Compromised intellectual property – Years of proprietary R&D and innovation can be stolen in minutes.
One survey found that 27% of companies had experienced an insider attack in the past year, with average costs exceeding $11 million per incident. The damage from both malicious and accidental insider threats should not be underestimated.
Preventing Insider Threats
Defending against insider threats relies on a multifaceted approach focused on prevention, detection, and response. Key measures include:
- Perform thorough background checks – Screen new hires, vendors, partners, and M&A targets for red flags.
- Implement least privilege access – Only grant the minimal access needed and enforce separation of duties.
- Deploy data loss prevention – Monitor, classify, and protect sensitive information against exfiltration.
- Encrypt data at rest and in motion – Use strong encryption to make data unusable if stolen.
- Enable strong access controls – Enforce complex passwords, multi-factor authentication, and privileged access management.
- Monitor user behavior – Analyze access patterns to detect abnormal activity and policy violations.
- Promote security awareness – Train staff on best practices through onboarding, emails, events, etc.
- Disable unneeded functions – Restrict admin rights, USB drives, logins, etc. not required for the role.
- Segment networks and limit lateral movement – Isolate the most sensitive data and systems.
- Log, monitor, and audit everything – Early threat detection requires robust activity logs.
Implementing these controls requires buy-in across the organization to foster a culture that takes insider threats seriously. Cybersecurity must involve everyone, not just IT.
Detecting Insider Threats
Stopping all insider attacks is impossible. Detecting them quickly when prevention fails is critical to limit damages. Tactics to expose insider threats include:
- User behavior analytics – Profile normal activities to flag anomalies like unauthorized access spikes.
- Honeypots – Place decoy data to detect snooping attempts.
- Email monitoring – Scan outgoing messages for sensitive data and suspicious content.
- Endpoint monitoring – Look for tampering, suspicious programs, and unauthorized hardware.
- Dark web monitoring – Search hacker forums and dark web sites for stolen company data.
- File integrity monitoring – Detect changes to critical files and system configurations.
- Network traffic analysis – Inspect patterns to catch exfiltration attempts.
- Asset management – Track databases, code repos, files, and devices to know what’s compromised.
Security teams should tap SIEM, UEBA, DLP, and EDR tools to surface early signs of insider threats. Machine learning algorithms can help detect anomalies missed by rules alone.
Responding to Insider Threats
When an insider attack is discovered, responding swiftly helps control damages. Response best practices include:
- Convene the incident response team – Ensure technical, legal, HR, PR, and executives are looped in.
- Determine scope and timeline – When did it start? Which systems and data were accessed?
- Preserve evidence – Make bit-by-bit copies of compromised endpoints for forensic analysis.
- Suspend access – Immediately revoke suspect’s credentials, accounts, and authorizations.
- Interview stakeholders – Talk to managers, coworkers, and the insider themselves if possible.
- Assess business impacts – Identify which operations, partners, and customers are affected.
- Initiate recovery procedures – Start restoring compromised systems from backup.
- Update security controls – Fix deficiencies that allowed the attack to close security gaps.
Lessons learned from insider threat response should feed back into prevention efforts. Any disciplinary measures for accidental insiders should focus on education and reducing negligence.
Insider Threat Programs
To confront insider threats systematically, many organizations develop formal insider threat programs. These programs coordinate policies, protections, detection, training, response, oversight, and reporting related to insider threats under one umbrella. Key elements often include:
- Executive oversight and sponsorship
- Cross-functional team with representatives from IT, HR, legal, business units, etc.
- Formal threat model, risk assessments, and mitigation plans
- Specialized insider threat detection tools and integration with existing security controls
- Customized employee training on security policies and responsibilities
- Thorough background vetting and monitoring of high-risk users
- Plans and processes for incident response and integrating lessons learned
- Analysis of trends, metrics, and benchmarking against peers
- Cooperation with business units, legal, and law enforcement as needed
Regular reviews help insider threat programs evolve and mature over time as new risks emerge. They represent the best practice for managing insider risk.
Using Behavioral Analytics to Detect Anomalies
One of the most powerful techniques for detecting insider threats involves building behavioral profiles of normal user activity patterns, then using analytics and machine learning algorithms to detect anomalies that deviate from those baselines. Some examples of how behavioral analytics can identify potential insider threats include:
- Logins from strange locations or times – If a user who always logs in from New York starts accessing accounts from Russia at 2 AM, that’s suspicious.
- Accessing unusual resources – An engineer repeatedly querying the HR database merits investigation.
- Abnormal download volume – If a user suddenly starts downloading gigabytes of data, it may indicate theft.
- Suspicious file transfers – Emailing documents late at night or to personal accounts warrants scrutiny.
- Unusual privileged commands – Root account usage should trigger alerts if that user is not an admin.
- Multiple failed login attempts – This may precede a hacker brute forcing credentials.
By automatically surfacing anomalies for human review, behavioral analytics acts as a force multiplier that makes monitoring for insider threats significantly more efficient.
Implementing Behavioral Analytics
Putting behavioral analytics into practice involves several key steps:
- Ingesting activity log data into a SIEM, analytics platform, or specialized UEBA solution.
- Establishing individual user baselines for metrics like login location, data access, commands run, etc.
- Applying statistical algorithms to detect significant deviations from normal patterns.
- Assigning risk scores to anomalous events to prioritize investigation.
- Providing actionable insights to security analysts reviewing flagged events.
- Tuning and optimizing algorithms over time to improve accuracy of alerts.
Machine learning techniques like clustering, neural networks, and support vector machines can uncover hidden patterns indicative of insider threats.
Challenges of Behavioral Analytics
However, some challenges can hinder the effectiveness of behavioral monitoring, such as:
- Not having enough baseline data for users who are new or have highly variable roles.
- Difficulty accounting for major changes like internal transfers or external events.
- Minimizing false positives that waste analyst time on benign anomalies.
- Ensuring algorithms keep adapting to evolving user behavior over time.
- Protection of user privacy – these tools should augment human judgement, not fully automate enforcement.
With careful implementation that provides actionable intelligence rather than raw alerts, behavioral analytics offers powerful protection against malicious and accidental insiders.
Conclusion
Insider threats present significant risks that bypass traditional perimeter defenses. Preventing, detecting, and responding to malicious and accidental insiders requires a multifaceted approach tailored to each organization’s culture and risk tolerance. Technical controls provide valuable safeguards, but truly securing the human element also requires promoting awareness, vigilance, and security as a shared responsibility among all employees. With comprehensive insider threat programs and behavioral analytics to enhance monitoring, companies can transform one of their biggest liabilities into a defensive strength.