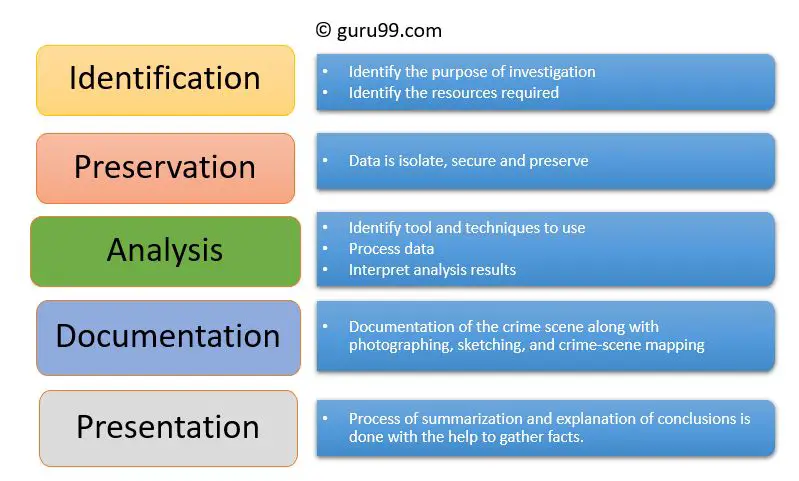
Digital forensics is the process of collecting, analyzing, and reporting on digital evidence in a manner suitable for presentation in a court of law. The purpose of digital forensic reports is to document the investigation process and present findings in a clear, concise, and comprehensive format. Reports serve as a record of the steps taken by the examiner during an investigation and provide a narrative of the relevant facts and findings. Well-documented reports allow the results and conclusions to be reviewed, verified, and replicated if necessary. Reports may be used internally or may be submitted as evidence in legal proceedings.
There are several key types of forensic reports that serve important but distinct purposes in digital investigations. This article provides an overview of the most common digital forensic report formats.
Investigative Reports
Investigative reports document the procedures and findings from a digital forensics investigation. These reports provide a chronological narrative of the analysis, including what actions the examiner took and what evidence was uncovered at each step. The goal is to provide a clear record of the investigation process. Investigative reports often cover the initial response, evidence acquisition, forensic imaging, data extraction and analysis, and investigative findings.
According to the article on Writing a Forensic Report, the key sections in an investigative report include the background, list of evidence, methodology, observations, and summary of findings. Background sets the context, evidence provides an inventory, methodology outlines the tools and techniques used, observations detail the findings, and the summary recaps the most relevant points.
As explained in Writing DFIR Reports: A Primer, investigative reports should focus on technical details and objective findings from the examination. The language used should be clear and accessible to non-technical readers. Charts, diagrams and other visual aids can help illustrate complex technical information and processes.
Investigative reports are detailed, technical documents that tell the story of the investigation, providing an authoritative record of what was done and found. They arm the legal team with the information needed to draw conclusions about the case.
Examination Reports
Examination reports are detailed technical reports generated from the forensic examination process. They document the steps taken by the examiner during the analysis of digital evidence, including documenting the tools and methods used, processes followed, findings, and results.
According to Forensic Focus, “The examination report details the who, what, when, where, how, and why related to the examination.” https://www.forensicfocus.com/articles/writing-dfir-reports-a-primer/
These reports are highly technical and aimed at other forensic experts who can understand the terminology and methodology. Information documented in an examination report includes the forensic tools used, processes and workflows, itemized findings, extracted data, analysis, and results of the examination.
Examination reports cover the forensic activities in detail, such as disk imaging, data extraction, timeline analysis, keyword searches, data carving, and recovering deleted files. Screenshots and technical details are included to document the step-by-step examination process.
According to Salvation Data, key sections of an examination report include a case overview, evidence examined, methodology, detailed findings, artifacts found, final results/conclusions, and supporting images. https://www.salvationdata.com/work-tips/write-a-forensic-report/
Expert Witness Reports
An expert witness report is prepared by a digital forensics expert for use in legal proceedings. The role of the expert witness is to provide opinions and testimony to the court on technical matters related to digital evidence and cybercrime (source). The expert analyzes digital evidence and data related to the case and documents their findings in a formal report.
The expert witness report will contain details on the background and qualifications of the expert, the evidence examined, the methodology used, observations made during analysis, opinions reached, and conclusions. According to one source, “Expert testimony is the culmination of everything that goes into a digital forensic examination, from consultation, acquisition, analysis, reporting, and court presentation” (source).
The role of the expert witness is to educate the court and provide impartial analysis. Their testimony must be based on facts, methodology, and expertise. A credible expert report is essential for the admissibility and weight given to digital evidence in legal proceedings.
Intelligence Reports
Intelligence reports focus on analyzing data to derive actionable intelligence and insights. These reports synthesize and make sense of information from various sources to identify threats, vulnerabilities, and risks. The key aspects of intelligence reports include:
Threat Intelligence – Assessing the tactics, techniques, procedures, and motivations of threat actors to understand their capabilities and predict future activities (Source).
Risk Analysis – Evaluating vulnerabilities and ranking risks to determine priority areas for defense and security efforts.
Intelligence Assessments – Developing informed conclusions about cyber threats, actors, campaigns or incidents based on available data.
Early Warnings – Identifying indicators, precursors or patterns that may foreshadow emerging or imminent threats.
Trend Analysis – Tracking and analyzing changes over time to identify shifts that may impact an organization’s security posture.
Intelligence reports synthesize raw data from various sources into actionable insights for strategic decision making and planning. The goal is to provide organizational leadership with the intelligence needed to get ahead of threats and make smart security investments.
Incident Response Reports
Incident response reports document the response to an occurred security incident. They capture critical details to evaluate the effectiveness of the incident response and recommend preventative measures for the future.
The key aspects of an incident response report include:
- Summary of the incident – When and how it was detected, systems and data impacted, timeline of events, root causes.
- Response actions taken – Containment strategies, forensic investigation processes, communications with stakeholders.
- Report findings and recommendations after incident – Steps to recover systems, findings from forensic investigation, recommendations to strengthen defenses and prevent similar incidents. (According to Venngage, recommendations should be specific, actionable, and aimed at addressing root causes).
- Supporting evidence like logs, screenshots, analysis results.
Well-documented incident response reports help organizations continually improve their security posture and incident response plans. Reports provide a factual account of what transpired and how well the response worked.
Executive Reports
Executive reports provide a high-level overview of the digital forensics investigation findings for management and leadership. They summarize the key details and outcomes in a condensed format without highly technical terminology or granular details of the examination Writing DFIR Reports: A Primer.
The goal of an executive report is to communicate only the most essential information that executives need to make strategic decisions. This includes the background and scope of the investigation, major findings, impact and risks identified, and recommended next steps Best practices for writing a digital forensics report.
Executive reports use clear, plain language and avoid forensics jargon. They focus on translating technical details into actionable business insights. Visual aids like charts, graphs, and infographics are often included to present data from the examination at a glance. The report is kept to 1-2 pages in most cases.
In summary, executive reports provide decision-makers with a high-level briefing of the key investigative findings, risks, and recommendations without overwhelming technical minutiae. Their purpose is to enable leadership to make informed strategic decisions for the organization.
Trend Reports
Trend reports focus on identifying patterns and changes in digital forensics over time. They analyze historical data to spot emerging trends and project future trajectories. As noted in the Digital Forensics Market Size report, analysts expect the global digital forensics market to grow at a 13.2% CAGR from 2019 to 2026, reaching $13.9 billion by 2026 (source). Key factors driving this growth include the proliferation of IoT devices, increased cybercrime, and new regulations requiring more rigorous digital forensic investigations.
Trend reports may examine adoption rates for certain tools and methodologies. For example, Trend Micro notes the increasing use of integrated digital forensic and incident response (DFIR) platforms like Trend Micro Vision One (source). These consolidated tools allow forensic investigators to gather evidence from endpoints, analyze data, and generate reports from a central interface.
Analysts also track trends in high-growth application areas. Per the Market Trends report, emerging technologies like blockchain, cloud forensics, mobile forensics, and social media forensics are key frontiers (source). As these technologies see greater adoption, demand for specialized investigative approaches will likely rise.
Audit Reports
Audit reports are used to assess compliance with policies, procedures, laws, and regulations. They are commonly used in digital forensics to analyze how effective an organization’s information security controls are at protecting data and thwarting cyber threats. Auditors will examine hardware, software, networks, data storage, and documentation to identify vulnerabilities or lapses in security.
Some key things an audit report may assess include access controls, security policies, data encryption, backup procedures, firewall configurations, employee practices, and more. The audit seeks to identify non-compliance, weaknesses, and potential improvement opportunities.
The resulting audit report will summarize the findings and provide an opinion on the effectiveness of controls. It may make recommendations to strengthen policies, close security gaps, or provide training. Reports are often presented to management or boards of directors so informed decisions can be made. Having regular audits is important for minimizing risk and demonstrating due diligence.
Conclusion
In summary, reports are crucial in digital forensics as they document the investigative process and findings in an unbiased manner. The different types of reports, such as investigative, examination, expert witness, intelligence, incident response, executive, trend, and audit reports, each serve a unique purpose. However, they share the common goal of accurately and comprehensively conveying digital evidence to various audiences like lawyers, judges, corporate management, and law enforcement. Well-written reports establish credibility and allow decision makers to fully understand the implications of the digital forensic results.
Some key best practices for report writing include being objective, structuring information logically, citing evidence thoroughly, following industry templates and standards, being mindful of the intended audience, and proofreading extensively. The final report provides the record of due diligence and professional methodology undertaken during an investigation. Given how pivotal reports are for legal proceedings, strategic planning, and incident investigations, mastery of report writing is an essential skill for any digital forensic practitioner.