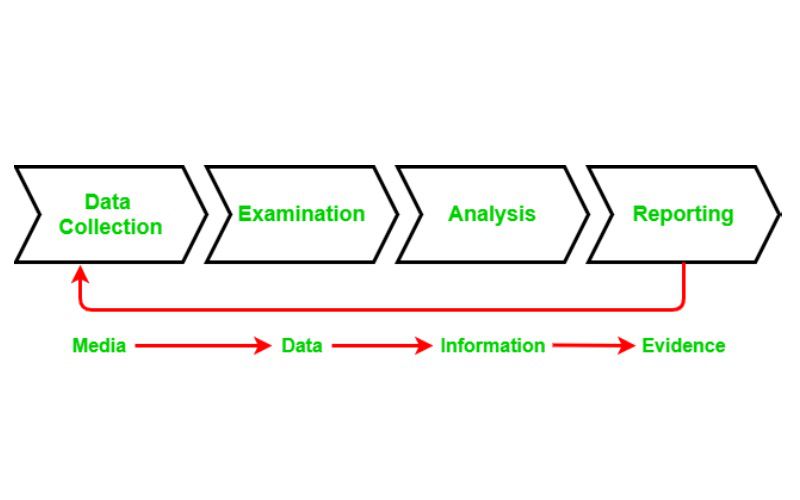
Digital forensics is the process of collecting, analyzing, and reporting on digital data and evidence in a manner suitable for presentation in a court of law. Digital evidence encompasses any data stored or transmitted using a digital device that contains information with potential evidentiary value. This can include computers, mobile devices, network traffic, databases, and more.
The goal of digital forensics is to perform a structured investigation while maintaining a documented chain of custody for the data. This allows digital evidence to be legally admissible in court and helps establish facts about cybersecurity incidents. Digital forensics provides insight into who, what, when, where, and how unlawful access or activity occurred on digital devices.
Planning and Preparation
The planning and preparation phase focuses on assembling the necessary tools and documentation required for a thorough forensic investigation. According to Victor Chidi in his Digital Forensics and Incidence Response video course here, key steps in planning and preparation include:
– Assembling the forensic toolkit – This involves gathering the right hardware and software tools for acquiring, imaging, and analyzing digital evidence. Standard tools include write blockers, forensic imagers, password crackers, and analytics software.
– Getting search warrants – Search warrants ensure the investigation abides by laws and protects the privacy rights of individuals. Warrants give legal authority to search and seize evidence from specific locations or devices.
– Coordinating with forensic specialists – Complex investigations often require expertise like computer forensics, mobile device forensics, cloud forensics, and network forensics. Specialists have the right skills and tools.
Securing the Scene
One of the most critical steps when collecting digital evidence is securing the crime scene. This involves isolating any devices that may contain evidence and establishing a solid chain of custody to ensure its admissibility in court. According to Sam Datt, “Identify, enumerate and isolate sources of Digital evidence. Document the unique serial numbers, stick labels onto each piece of evidence…” (https://www.linkedin.com/pulse/5-steps-securing-digital-crime-scene-sam-datt).
It’s important to photograph and video record the scene as found, including all devices and connections. Carefully label each piece of evidence, noting identifying details like serial numbers. Seal evidence like hard drives in anti-static packaging to protect them. Strict chain of custody procedures should be followed to track each piece of evidence from collection to analysis to storage or return. Maintaining integrity of the evidence is key for it being permissible in legal proceedings.
Acquiring Data
The next step in the digital forensics process is acquiring the digital evidence. This involves making a forensic copy or image of digital devices like computers, mobile phones, tablets, and storage media. It is critical to follow proper protocols to ensure the integrity of the original data is preserved.
When acquiring digital evidence, forensic examiners use specialized tools and hardware called write blockers to prevent any data from being modified or deleted from the device. Write blockers allow read-only access to prevent accidental changes to the original data (Source).
Forensic imagers create an exact bit-for-bit copy of the digital media which serves as the working evidence file. Cryptographic hash values like MD5, SHA-1 are calculated for both the original data and forensic image to verify the integrity and authenticity of the copy (Source).
Proper acquisition of digital evidence while preserving the chain of custody documentation is foundational to the entire forensic investigation and analysis process.
Analyzing Data
Once the data has been acquired through proper forensic imaging, the next step is to analyze the data. This involves extracting and reviewing files to identify relevant evidence. Investigators will use forensic tools to parse through the data and recover deleted files that may contain useful information. Encrypted data also needs to be decrypted so that its contents can be examined.
When analyzing a storage device or system image, it is important to create a working copy so that the original is untouched. The working copy can then be scoured for the specific data needed to reconstruct events or activities. File metadata like creation/access dates and system logs provide helpful timeline evidence. Known data patterns and algorithms can identify concealed or obfuscated data as well. The analysis may also uncover application artifacts, registry entries, internet history, and other digital footprints left behind by the user.
Thorough analysis requires specialized tools to carve out unallocated disk space, reconstruct internet activity, crack encryption, convert encoded or compressed data, and visualize complex relationships. The goal is to extract all possible relevant data from the working copy without altering the original image.
According to The Basics of Digital Forensics, analysis involves “unlocking, decoding, decompressing, or converting data into a usable format.” Investigators must possess the right skills to effectively analyze different types of digital evidence and uncover probative information.
Reconstructing Activities
Reconstructing the sequence of events and activities is a crucial step in the digital forensic process. The investigator will review system artifacts, event logs, file metadata, registry entries, memory snapshots, network traffic captures, and other sources to build a timeline of relevant events.
The goal is to correlate evidence found across multiple sources to determine when key actions occurred, in what sequence, involving which accounts, files, devices, or applications. This enables the investigator to reconstruct what happened and how in order to determine root causes and evaluate if any unauthorized or malicious activity occurred.
Building an accurate timeline requires piecing together evidence from multiple, and sometimes inconsistent, sources. The investigator may need to reconcile time zone differences, account for missing or incorrect timestamps, and resolve other discrepancies. Validation is key – the timeline should be cross-checked against all available forensic artifacts.
Powerful timeline analysis tools help automate correlation and visualization. But human expertise is still essential to interpret the story the timeline tells and draw sound conclusions based on reason, experience, and judgment. The end result is a detailed recreation of events that can serve as evidence in legal proceedings.
As noted in “Technology Corner: Virtual Crime Scene Reconstruction” (https://commons.erau.edu/jdfsl/vol6/iss4/6/), virtual reconstruction of a digital crime scene enables investigators to evaluate different hypotheses and scenarios of what may have occurred.
Reporting Findings
The reporting phase is crucial for documenting the methodology, maintaining chain of custody, and explaining the findings of the investigation. The final report should provide a clear timeline of the investigation and outline the processes used to acquire, analyze, and validate the digital evidence. According to Writing DFIR Reports: A Primer, the report should focus on explaining what the evidence indicates within the context of the investigation, regardless of whether it is incriminating or exonerating.
It is important that the report provides details on how the data was acquired, including hardware and software used. Any gaps in acquiring potential evidence should also be acknowledged. Thorough documentation establishes a demonstrable methodology and chain of custody. According to Write a Forensic Report Step by Step, the findings section should objectively present the facts revealed by examination of the evidence without speculation or subjective conclusions. The significance of the findings is then interpreted in relation to the original allegations or questions. Vetting the findings with peer review can further validate the evidence and identify any errors or omissions.
By systematically detailing the investigation from start to finish, digital forensic examiners can produce reports that withstand scrutiny and clearly convey pertinent findings to legal teams, corporate management, or other stakeholders.
Presenting Evidence
When presenting digital evidence in court, it is important to properly prepare exhibits, testify effectively as an expert witness, and maintain professionalism throughout the legal proceedings. Exhibits containing digital evidence should be clearly labeled, organized logically, and formatted appropriately for display to a jury or judge. According to tips from Magnet Forensics, exhibits should avoid unnecessarily technical jargon and clearly convey information to laypeople. The expert witness should thoroughly explain the nature, collection, and analysis of digital evidence while using aids like slides, videos, and animations to illustrate concepts and procedures.
The witness must remain calm and professional when undergoing examination or cross-examination on the stand. They should answer questions directly and avoid speculation, only conveying opinions within their area of expertise per the Magnet Forensics article. Maintaining composure and systematically presenting evidence and conclusions will instill confidence and trustworthiness.
Digital forensics experts such as Mic Merritt note that strong presentation skills are essential when conveying complex technical information to legal professionals. The expert witness should strive to educate the court effectively on digital evidence analysis while avoiding confusion or ambiguity. Proper preparation, exhibits, testimony, and professional behavior are key to successfully presenting digital evidence in legal proceedings.
Returning Evidence
Once a case is closed or adjudicated, the original digital evidence collected during the investigation must be returned to the rightful owner while maintaining proper chain of custody. According to the EMI Standards and Best Practices, “Evidence items should be retained in the custody of the evidence management for the entire duration of the item’s required duration of custody until receipt of authorized instructions regarding disposal.”
It is crucial for investigators to follow policies on retaining copies of digital evidence, maintaining comprehensive documentation, and preserving chain of custody when returning original evidence. Digital evidence should only be returned once it is authorized and confirmed no longer needed for appeals or future proceedings. The chain of custody must be upheld through the final transfer back to the owner.
Proper evidence management procedures, including using evidence disposition forms and documenting all transactions, can help ensure the process is completed accurately and securely.
Conclusion
In summary, the main steps for properly collecting digital evidence are planning and preparation, securing the scene, acquiring data, analyzing data, reconstructing activities, reporting findings, presenting evidence, and returning evidence. It is crucial to follow these systematic procedures in order to ensure the integrity and admissibility of digital evidence. Proper handling of digital evidence requires specialized skills and tools as well as adherence to legal and ethical guidelines.
Following best practices for the ethical collection of digital evidence is essential. Investigators must balance privacy rights, confidentiality, and other ethical concerns when acquiring and examining digital data. They should use the least intrusive methods possible and minimize unnecessary exposure of sensitive personal information. The methods used should be well-documented and justified. It is critical that those involved in digital forensics maintain impartiality, integrity, and transparency throughout the process.
Overall, the structured digital forensics process aims to extract reliable digital evidence while protecting civil liberties. When properly executed according to industry standards and ethics, digital forensic investigations can uncover the truth and serve the cause of justice in a fair and ethical manner.