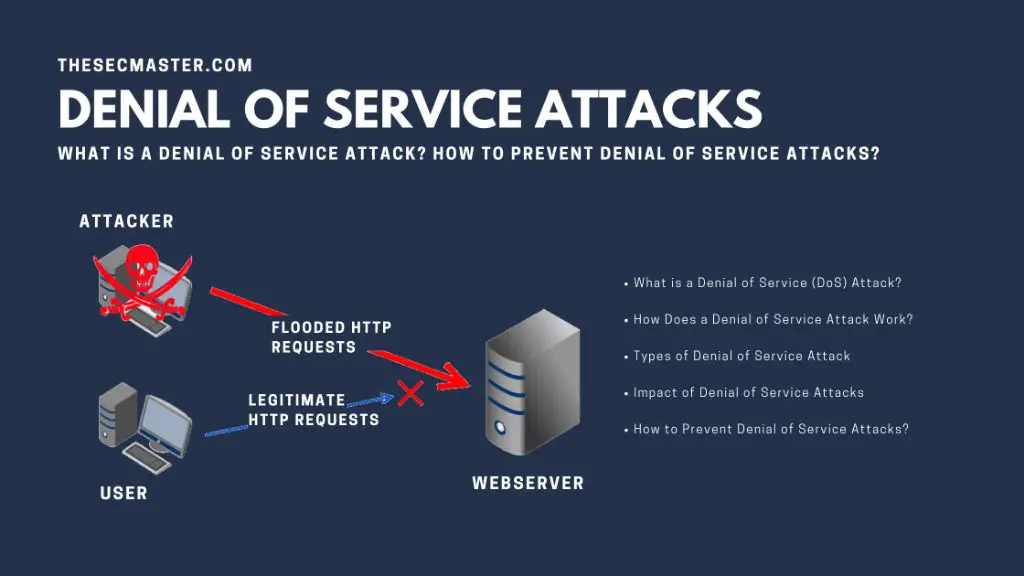
A denial of service (DoS) attack is a cyber attack that aims to make a computer system or network resource unavailable to its intended users. DoS attacks overwhelm the targeted machine or network with traffic from multiple sources in order to disrupt services and prevent legitimate requests from being fulfilled. There are several common causes and motivations behind DoS attacks, as well as various methods attackers use to carry them out.
What is a Denial of Service Attack?
A denial of service attack floods a targeted system with bogus requests, overwhelming it to the point that it can no longer process genuine requests. This effectively denies legitimate users access to the service. There are several variations of DoS attacks, including:
- Network-layer attack: This floods the target’s network bandwidth with traffic until it can no longer process genuine network packets. A network-layer attack involves sending the victim a stream of TCP, UDP, ICMP, or other protocol packets in an attempt to overwhelm the victim’s bandwidth. Such an attack can prevent access to an entire network, not just a single server.
- Application-layer attack: This inundates a web application with requests until it can no longer process genuine traffic. An application layer attack targets web server resources and bandwidth by intentionally flooding a targeted website with syn packets and holding open as many half-open TCP connections as possible. Application-layer attacks include low-bandwidth attacks, Slowloris, R.U.D.Y. attacks, and more.
- Repeated attacks: This involves barraging the target with a high volume of seemingly legitimate requests. When performed multiple times, it can bring down the victim completely.
- Permanent DoS attack: An attack intended to render the target completely unusable, rather than simply disrupting service.
- Distributed DoS (DDoS) attack: This uses multiple machines to target a single victim. The flood of incoming messages overwhelms the target system, causing it to crash and deny service to legitimate users.
The impact of DoS attacks can vary significantly – from minor disruption to complete denial of service. The goal is to compromise availability and uptime, obstruct access to and use of resources, or diminish service quality for users. DoS attacks often serve as a distraction while the real criminal act is being perpetrated.
Common Causes & Motivations Behind DoS Attacks
There are various reasons why an attacker might execute a DoS attack:
- Hacktivism: Hacktivists use DoS attacks to make political statements and promote political aims. Anonymous and other hacktivist groups have used DoS attacks against organizations they disagree with politically.
- Revenge: Disgruntled employees or angry ex-staff with inside knowledge of systems have been known to launch DoS attacks against their former employers as revenge.
- Competition: Unscrupulous business rivals sometimes use DoS attacks against competitors, especially ecommerce sites, hoping to diminish their performance and drive customers to their own sites instead.
- Extortion: Some criminals threaten a DoS attack against an organization unless they receive a ransom payment in cryptocurrency. DDoS extortionists often recruit and rent botnets to carry out the actual attack.
- Cyber warfare: DoS attacks have become an increasingly common tactic for cyber warfare between nation states. Attacks are often intended to damage digital infrastructure and disrupt vital online services.
- Testing & research: White hat hackers, cybersecurity researchers, and developers might execute DoS attacks against their own systems to test platforms and pinpoint vulnerabilities before attackers discover them.
- Accidental: Poorly configured servers and flawed network hardware can unintentionally cause DoS conditions.
- Malicious pranksters: Vandals have been known to launch DoS attacks simply to watch systems crash & burn.
Ultimately, there are a wide range of motivations driving denial of service attacks, both malicious and relatively innocuous. The end goal for attackers is interrupting services and victimizing users.
Common DoS Attack Vectors & Techniques
Attackers have many techniques available to overwhelm systems and networks with bogus traffic. Some of the most common DoS attack vectors include:
Volume-Based Attacks
Volume-based attacks aim to consume available bandwidth, overwhelm network infrastructure, and flood resources. Tactics include:
- UDP floods
- ICMP floods
- SYN floods
- TCP floods
- HTTP floods
- HTTPS floods
- DNS amplification attacks
These work by exhausting bandwidth and inundating targets with more traffic than they can accommodate. Volume-based attacks can be executed by a single system flooding the target or through distributed means, like botnets.
Protocol Attacks
Rather than just aiming to exhaust bandwidth, protocol attacks target inherent weaknesses in network protocols themselves. Examples include:
- SYN flood attacks
- Ping of Death attacks
- Smurf attacks
- Permanent DoS attacks
- DNS amplification attacks
- Teardrop attacks
Attackers exploit vulnerabilities in implementations of network and transport layer protocols. By sending malformed packets, they can tie up resources and crash systems.
Application Layer Attacks
Application layer attacks target web server resources and flood sites with requests in an attempt to overwhelm. Common examples:
- HTTP POST floods
- HTTP GET floods
- Slowloris
- RUDY attacks
These attacks consume web server resources or open multiple connections until capacity is reached, making services lag or timeout for legitimate users.
Reflection & Amplification Attacks
Reflection and amplification attacks use third-party systems to flood victims with traffic. These tactics include:
- Smurf attacks
- Fraggle attacks
- DNS amplification
- NTP amplification
- SSDP amplification
- Chargen amplification
Attackers spoof the victim’s IP address and send small requests to publicly accessible services that reply with much larger responses. This amplifies and reflects attack traffic toward the victim.
Permanent DoS Attacks
Permanent DoS attacks render systems or hardware completely unusable, rather than just temporarily disrupting service. Methods include:
- Phlashing (flashing malicious firmware to network devices)
- OS exhaustion (overloading an operating system’s resources)
- Brute force hardware damage
- Fried hardware (literally cooking hardware components)
These are advanced, hardware-focused attacks launched by highly skilled adversaries. Victims require hardware replacements or reinstalls to recover.
Distributed Reflection DoS
Distributed reflection denial of service (DRDoS) attacks combine multiple reflection vectors and botnets to maximize the scale and impact of attacks. Large, distributed botnets perform spoofing and reflection to bombard victims with enormous volumes of traffic from multiple directions.
Other DoS Vectors
Other potential DoS vectors include:
- Resource depletion – consumebandwidth, RAM, CPU, disk/data storage space, database connections, etc.
- Moving target defense – Never allowing systems to fully recover from an attack before launching another.
- App-level attacks – Targeting application logic, bugs, or vulnerabilities.
- Encrypting ransomware – Encrypting data and demanding ransom to unlock it.
- Brute force resource exhaustion – Bombarbing logins, database searches, etc. with invalid inputs.
Attackers are constantly evolving and innovating new ways to disrupt services and deny usage of resources. DoS methods are diverse and ever-changing.
Common DoS Attack Tools
Skilled hackers can code their own tools to carry out DoS attacks, but for novice attackers there are many easy-to-use programs and botnets for hire:
- Low Orbit Ion Cannon (LOIC): FOSS stress testing tool often used for DoS attacks.
- HULK: Python-based DoS testing tool.
- R.U.D.Y. – R-U-Dead-Yet: HTTP POST DoS tool.
- Tor’s Hammer: Perl-based application DoS tool.
- Pyloris: Slowloris implementation in Python.
- T50 Network Stress Tester: Powerful packet injector for Layer 4-7 DoS testing.
- UFONet: Abuses OSI Layer 7 HTTP to create DoS attacks.
- GoldenEye: DDoS penetration testing tool.
- Botnets: Armies of infected computers rented outfor reflection/amplification DDoS attacks.
Attackers have access to a thriving underground market for DoS and DDoS-for-hire services. Unscrupulous vendors rent out botnets, traffic spoofing services, malware, etc. to even unskilled attackers at low prices.
Key Indicators of a DoS Attack
Detecting an active DoS attack requires analyzing various symptoms and traffic anomalies. Signs include:
- Unusually slow network performance and response times.
- Spikes in bandwidth utilization and bottlenecks.
- Increased rates of packet loss.
- High volume of TCP, UDP, or ICMP packets incoming to the network.
- Legitimate requests receiving delayed or non-existent responses.
- Inability to access websites and use internet services.
- Reduced availability of server resources and services.
- Dramatic surges in DNS queries from random source IP addresses.
- Suspicious concentration of traffic from a single source or autonomous system.
- Crashes, lockups, and failures of infrastructure components.
Ongoing monitoring and analytics focused on bandwidth, connections, traffic flows, loads, and resource consumption is critical to detect DoS conditions arising. The traffic patterns of an attack will stand out from normal usage.
DoS Mitigation & Prevention
There are various strategies and best practices organizations should follow to mitigate the risk of denial of service attacks:
- Network infrastructure monitoring: Actively monitor bandwidth utilization, packet loss, latency, and other metrics across network infrastructure to quickly detect attacks.
- Traffic rate limiting: Implement rate limiting on routers and other network hardware to restrict flows to acceptable levels.
- IPS threat detection: Enable intrusion prevention systems to identify DoS activity and malformed traffic.
- Access control lists: Use ACLs on routers to restrict and filter traffic from problematic hosts and networks.
- Connection limits: Enforce connection limits based on source IPs to prevent single hosts overwhelming resources.
- Load balancers: Distribute traffic over multiple servers to avoid overloading single points of failure.
- Overprovisioning: Provision bandwidth, servers and other infrastructure to handle traffic volumes above normal loads.
- CDN caching: Use content delivery networks to cache and distribute traffic to ease loads.
- DDoS mitigation services: Route traffic through managed scrubbing centers to filter attack traffic.
- Blackhole filtering: “Blackhole” routes and filter suspicious traffic flows to relieve overloaded systems.
- OS hardening: Harden operating systems and infrastructure through patches, disabling unused features/protocols, etc.
- Application security: Perform rigorous application security measures – sanitize inputs, enforce authentication, limit requests, etc.
- Incident response plan: Develop and rehearse a detailed response plan for DoS scenarios.
Proactive preparedness and defense-in-depth security reduce the attack surface available for denial of service activities.
Conclusion
Denial of service attacks aim to compromise availability and prevent legitimate use of resources by overwhelming systems with bogus requests. Motivations range from hacktivism and extortion to revenge or competition. Volume-based floods, protocol attacks, reflection techniques, and application assaults are common DoS vectors. To mitigate risk, organizations should actively monitor networks, enforce limits, balance loads, scrub traffic, and employ layered security controls. With vigilance and concerted effort, the impact of DoS attacks can be minimized.