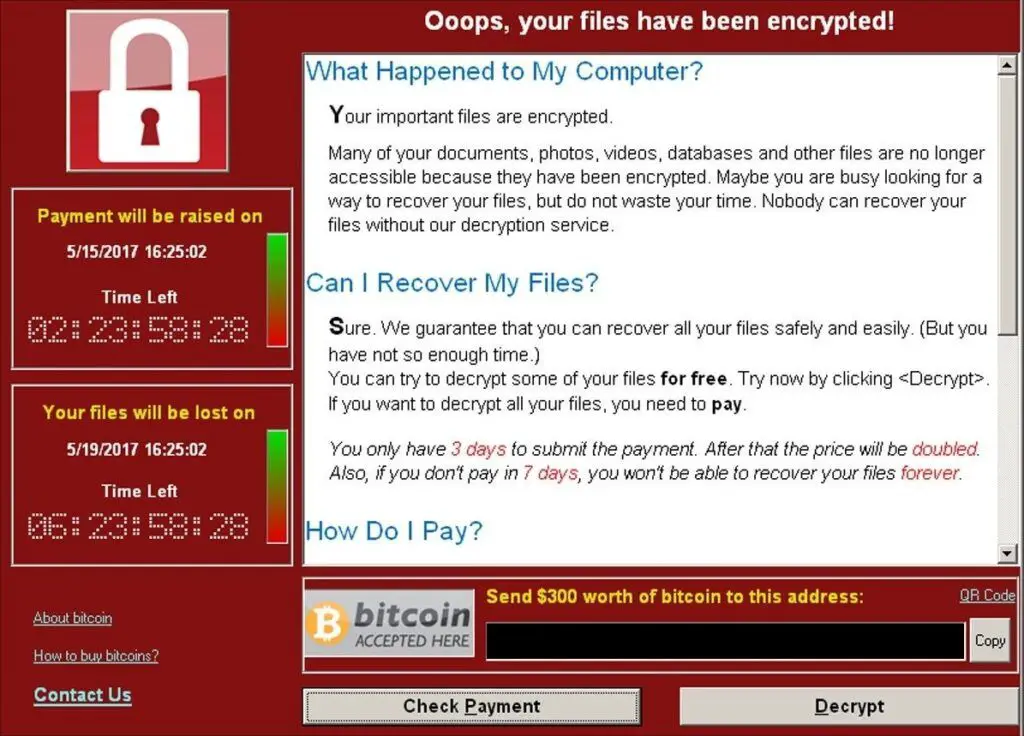
Ransomware is a type of malicious software that encrypts a victim’s files and blocks access to the computer or data. The perpetrators demand a ransom payment in exchange for restoring access.
Ransomware typically spreads through phishing emails or by exploiting vulnerabilities in systems. Once installed, it encrypts files and displays a ransom note demanding payment, often in cryptocurrency. If the ransom is not paid, the data remains encrypted and inaccessible. Ransomware attacks are a growing cybersecurity threat, with increasing financial and business impacts.
Financial Motivation
Ransomware is often used by cybercriminals to extort money from victims. The financial motivation behind ransomware attacks is clear – they provide an easy and lucrative revenue stream for attackers.
According to Cybersecurity Ventures, global ransomware damages are predicted to cost victims $265 billion annually by 2031, up from $20 billion in 2021 [1]. The increasing prevalence of ransomware attacks targeting businesses and critical infrastructure shows that there is big money to be made.
Ransomware can generate large sums of cash quickly and relatively easily. Payments are typically demanded in cryptocurrency, which helps attackers avoid detection. Cybercriminals are drawn to ransomware because it offers high rewards for little risk [2].
The financial incentives have led to ransomware becoming one of the most common cyber threats faced by organizations today.
Easy Money
Ransomware provides criminals with an easy and lucrative way to make money compared to other cybercrime methods. Unlike stealing credit card numbers or selling stolen data which require more effort to monetize, ransomware provides instant payouts. The criminal simply needs to infect a victim with ransomware and demand a ransom payment to decrypt their files. According to Ransomware: How cyber attackers turn hacking into profit – Blog, ransomware allows attackers to utilize “lock and extort” tactics to turn hacking into fast profits. Ransomware also scales easily – criminals can infect thousands of victims automatically and rapidly using malware kits. The Checkpoint article notes that ransomware provides criminals “guaranteed returns” compared to other methods that have less certain payouts. Overall, the instant payouts, scalability, and guaranteed profits make ransomware an easy way for criminals to generate lucrative returns.
Hard to Trace
Cryptocurrencies like Bitcoin allow ransomware hackers to receive payments that are very difficult to trace. Bitcoin transactions are recorded on a public ledger called the blockchain, but Bitcoin wallets are not linked to real world identities. This provides a layer of anonymity for ransomware hackers (Paquet-Clouston, 2019, https://academic.oup.com/cybersecurity/article/5/1/tyz003/5488907).
While it is possible to analyze the blockchain to track ransomware payments, doing so requires significant time and resources. The pseudonymous nature of Bitcoin makes it challenging for law enforcement to identify individuals receiving ransom payments (NPR, 2021, https://www.npr.org/2021/06/10/1004874311/how-bitcoin-has-fueled-ransomware-attacks).
Overall, cryptocurrency allows ransomware hackers to get paid while remaining anonymous. The difficulty of tracing ransomware payments in Bitcoin and other cryptocurrencies contributes to the appeal for criminals carrying out these attacks.
Low Risk
The anonymous nature of ransomware significantly reduces the risks for attackers, making it an attractive option to pursue financially motivated cybercrimes. Ransomware gangs are able to hide behind layers of anonymity, using cryptocurrencies like Bitcoin to receive ransom payments which are difficult to trace (source). The remote deployment of ransomware also allows attackers to avoid directly engaging with targets. With advanced encryption methods, ransomware is designed to lock organizations out of their systems securely until the ransom is paid. The transactional nature of ransomware limits the interaction between victims and perpetrators. This anonymity emboldens threat actors to conduct repeated campaigns with limited fear of being identified or facing consequences.
Vulnerable Systems
One of the key factors that enables ransomware attacks is vulnerable and unpatched systems. This primarily refers to outdated software or operating systems that have known vulnerabilities which have not been patched or updated by organizations (Unpatched Vulnerabilities are the Most Common Attack Vector Exploited by Ransomware Actors). Ransomware threat actors aggressively search for and target these vulnerable systems as an easy pathway into networks.
Unpatched vulnerabilities provide an open door that allows ransomware to bypass security measures and infect systems. Once inside the network, ransomware can then spread laterally and encrypt files across shared drives and backups. Well-known exploits like EternalBlue and Log4j have been used repeatedly over the years in high-profile ransomware attacks.
Maintaining comprehensive patching and update management is critical for organizations to close off these security holes. However, many struggle to regularly patch systems, update software versions, and replace end-of-life operating systems. This problem is amplified by the rapid proliferation of ransomware kits available through Ransomware-as-a-Service, allowing even unskilled actors to take advantage of known vulnerabilities.
User Behavior
One of the main factors that enables ransomware attacks is risky user behavior. When users click on malicious links or attachments in phishing emails, download software from unverified sites, or use weak passwords, they make an organization vulnerable. Ransomware often initially enters a system because a user was tricked into installing it or granting access.
For example, a common ransomware attack begins with a convincing phishing email. The email might claim the user needs to verify some information or review an invoice. If the user clicks on the attachment or link, malware like ransomware could be installed on their device. From there, it can spread throughout the network.
According to an IBM report, [1] 94% of malware is delivered through email phishing attempts. Users might also visit compromised sites and inadvertently download ransomware hidden in software installers or other files. Weak passwords further enable attackers to spread malware across systems.
While technological solutions are important, educating users and promoting safe cyber practices is essential to stopping ransomware. Users should learn how to identify phishing attempts, avoid suspicious links and sites, and use strong unique passwords. With training and awareness, user behavior can become a strong defense rather than a vulnerability.
Weak Security
Poor cybersecurity practices significantly increase an organization’s chances of being victimized by ransomware attacks (https://www.enzoic.com/blog/ransomware-attacks/). Weak passwords on user accounts provide an easy point of entry for attackers. Services like RDP, SMB, Telnet, and NetBIOS are frequently targeted due to having vulnerable code that is often unpatched (https://www.cisa.gov/news-events/cybersecurity-advisories/aa22-137a). Allowing phishing attempts to breach defenses gives attackers initial access to probe networks and find weaknesses. Failure to promptly detect intrusions allows adversaries time to escalate privileges, move laterally, and deploy ransomware across systems.
Organizations must implement defense-in-depth security measures like multi-factor authentication, network segmentation, endpoint detection and response solutions, and cybersecurity awareness training. Keeping software updated with the latest patches is also critical. Good cyber hygiene and vigilance helps mitigate the risk of ransomware.
Ransomware-as-a-Service
Ransomware attackers have begun offering ransomware kits and services to enable broader attacks with less technical expertise required. This business model is known as Ransomware-as-a-Service (RaaS). According to Trend Micro, “Ransomware as a service (RaaS) is a business model that involves selling or renting ransomware to buyers, called affiliates.”
With RaaS, ransomware developers provide easy-to-use dashboards and infrastructure so anyone can launch ransomware campaigns with no need to code. RaaS developers take a cut of any ransom payments made. Major RaaS operations include REvil, Lockbit, and others. This turnkey approach has fueled the growth of ransomware by removing technical barriers.
According to CrowdStrike, “RaaS lowered the barrier to entry significantly by providing affiliates with prebuilt malware kits on dark web marketplaces. Today, an aspiring ransomware operator does not need to know how to develop malware. The RaaS model provides everything they need to get started.”
Sources:
https://www.crowdstrike.com/cybersecurity-101/ransomware/ransomware-as-a-service-raas/
https://www.trendmicro.com/vinfo/us/security/definition/ransomware-as-a-service-raas
Conclusion
In summary, the primary factors enabling ransomware attacks include the financial incentives, vulnerable systems and user behavior, the rise of Ransomware-as-a-Service, and the low risk and high reward for cybercriminals. Ransomware can generate large profits that are hard to trace, especially with the use of cryptocurrency for ransom payments. Many organizations also have weak security protections, outdated software, and employees who fall victim to social engineering tactics. The development of Ransomware-as-a-Service has also made it easier for criminals with limited technical skills to launch attacks. While no single solution can stop all ransomware, a combination of security awareness training, keeping software patched and updated, robust backup procedures, and implementing advanced endpoint and network security can significantly reduce risk.