A vulnerability management framework is a critical component of any organization’s cybersecurity strategy. The purpose of a vulnerability management framework is to systematically identify, assess, and remediate vulnerabilities within an organization’s networks, systems, and applications. Having a strong vulnerability management framework in place allows organizations to proactively strengthen their security posture and reduce the risk of successful cyber attacks.
Why is Vulnerability Management Important?
Vulnerability management is important for several reasons:
- It helps organizations identify and prioritize vulnerabilities based on risk.
- It enables the patching of critical vulnerabilities before they can be exploited by attackers.
- It provides visibility into an organization’s attack surface and potential security gaps.
- It facilitates compliance with security policies, regulations, and industry standards.
- It reduces the time and costs associated with incident response by preventing successful attacks.
Without a solid vulnerability management program, organizations leave themselves open to security breaches, data loss, service disruptions, and regulatory non-compliance. Given the increasing sophistication of cyber threats, no organization can afford to neglect vulnerability management.
Elements of an Effective Vulnerability Management Framework
An effective vulnerability management framework typically consists of the following core elements:
Asset Inventory
The first step is to maintain a comprehensive inventory of assets that need to be assessed and monitored. This inventory should include:
- Servers
- Endpoints
- Network devices
- Cloud instances
- Mobile devices
- Software platforms and applications
- Supporting infrastructure
Having an accurate, up-to-date asset inventory is crucial for identifying all potential vulnerabilities across the IT environment.
Vulnerability Scanning
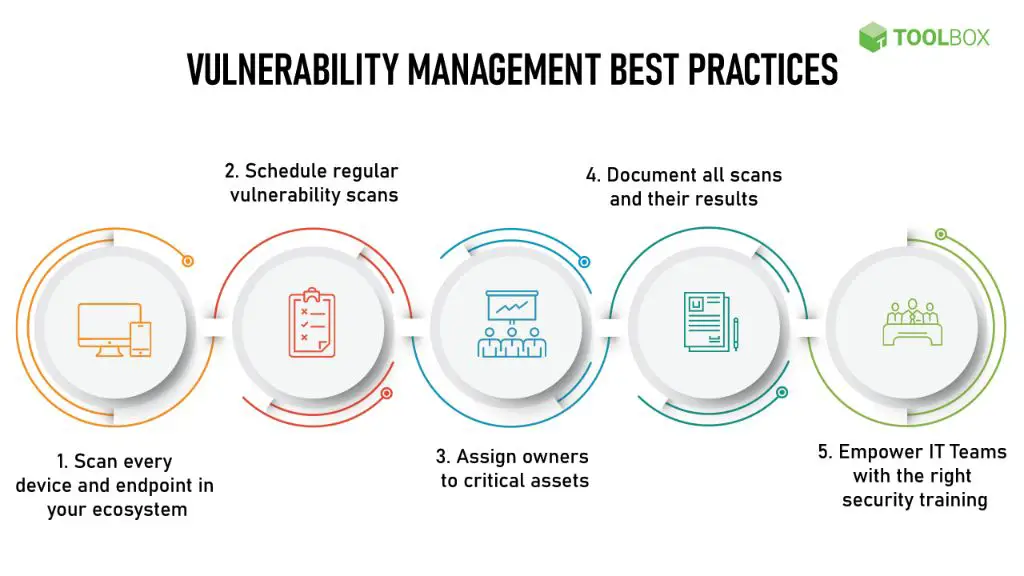
Both internal and external vulnerability scanning should be conducted on a regular basis across the entire IT infrastructure. Scanning helps detect misconfigurations, missing patches, exploitable bugs, and other security flaws present on assets. Leading vulnerability scanning tools can automate much of this process and provide detailed reports that outline discovered vulnerabilities and associated risks.
Risk Analysis
Not all vulnerabilities present the same level of risk. Once vulnerabilities have been identified through scanning, each one should be evaluated based on factors such as:
- Threat landscape – Is the vulnerability being actively exploited in the wild?
- Criticality – How critical is the impacted asset and data to organizational functions?
- Exploitability – How easily can this vulnerability be exploited?
- Impact – What is the potential business impact if the vulnerability is exploited?
This enables the prioritization of vulnerability remediation efforts based on actual risk levels.
Remediation
Vulnerabilities need to be addressed through remediation in a timely manner, with critical risks fixed immediately. Different remediation options exist depending on the vulnerability:
- Patching – Installing vendor-released patches that address specific vulnerabilities.
- Configuration changes – Tightening configurations that may be overly permissive.
- Software updates – Upgrading to newer software versions without vulnerable components.
- Workarounds – Implementing temporary risk reduction measures when patches or upgrades are unavailable.
- Mitigating controls – Adding controls such as WAFs, firewalls, and IPS to reduce exposure.
Organizations should have defined policies and procedures in place to handle vulnerability remediation efficiently.
Verification
It’s important to verify that remediation efforts were successful. Follow-up scans should be performed after applying fixes to confirm vulnerabilities have been eliminated or mitigated to an acceptable minimal risk level based on scoring criteria.
Reporting and Metrics
Ongoing metrics need to be tracked, with detailed vulnerability reports provided to security leaders and stakeholders. Useful metrics include:
- Total vulnerabilities detected
- Vulnerabilities remediated or mitigated
- Mean time to remediate vulnerabilities
- Vulnerabilities still outstanding
- Percentage of assets scanned
Reporting gives insight into remediation progress, allows monitoring of trends, and helps communicate risks to business owners.
Continuous Monitoring
Vulnerability management should not be a one-time project but rather an ongoing program. Environments require continuous monitoring given factors such as:
- New vulnerabilities constantly emerging
- Additional assets being added
- Patches causing configuration changes
- Network and system changes altering the attack surface
By continuously monitoring for new vulnerabilities, risks can be addressed before they are exploited.
Key Benefits of a Vulnerability Management Framework
Here are some of the top benefits organizations gain by implementing a comprehensive vulnerability management framework:
- Improved risk visibility – By maintaining an asset inventory and performing regular scans, organizations gain greater visibility into risks across their environment.
- Prioritized remediation – Vulnerability data enables smarter prioritization based on actual risk levels.
- Reduced exploitability – Proactively patching vulnerabilities leaves fewer opportunities for attackers to exploit flaws.
- Faster response times – With vulnerabilities mapped out, incident response teams can react quicker when an event does occur.
- Optimized resource allocation – Resources for enhancing cyber defenses can be allocated more effectively based on vulnerability insights.
- Stronger compliance – Documented vulnerability management programs help demonstrate due diligence to auditors.
- Lower costs – Reducing successful breaches saves on the enormous post-breach costs associated with investigation, remediation, fines, lawsuits, and reputational damage.
Challenges in Vulnerability Management
While vulnerability management delivers substantial benefits, organizations often face some key challenges when implementing their programs:
Visibility Gaps
Since vulnerability management relies on having an accurate asset inventory, gaps in visibility can lead to blind spots. Some organizations struggle to gain full visibility into assets like IoT devices, BYOD endpoints, and cloud-based resources spread across services.
Detection Difficulties
Certain types of vulnerabilities can be tricky to detect reliably through automated scanning. These include logical vulnerabilities that require an understanding of application logic or business processes to uncover.
Analysis and Prioritization
With scans potentially detecting thousands of vulnerabilities, separating the signal from the noise can be difficult. The triage process to determine actual risk levels and priority for remediation requires significant human analysis and subject matter expertise.
Resource Constraints
Security teams are often understaffed, and lack of qualified personnel makes scaling vulnerability management challenging. The cybersecurity skills gap also exacerbates resourcing issues.
Patching Disruptions
While patching is critical, upgrading production systems also introduces risk of operational disruptions. Change control processes must be followed to avoid outages from patching activities.
Legacy Systems
Older legacy systems and end-of-life software that are still embedded in the environment may not be patchable for identified vulnerabilities. Lack of upgrade capacity for certain systems can leave exposure.
Developing a Vulnerability Management Framework
Developing and implementing an effective vulnerability management framework includes the following key steps:
Establish Governance
Governance provides oversight and facilitation for the program. A cross-functional team representing IT, security, DevOps, and business units should be assembled to develop policies, procedures, reporting requirements, and processes for vulnerability management.
Create Asset Inventory
Assets in scope for the program must be documented in a centralized repository. This inventory needs to be comprehensive and continually kept current as the environment changes.
Define Vulnerability Scanning Scope
Determine the specific assets, infrastructure zones, and applications that will be scanned. Scanning everything may be unrealistic, so organizations should prioritize areas of highest risk.
Select Tooling
Evaluate and select automated scanning solutions that can efficiently detect vulnerabilities across the environment. A combination of agent-based and agentless scanners may be required for complete coverage.
Establish Processes
Document vulnerability management processes covering scans, threat intel integration, risk analysis, remediation, verification, exception handling, and reporting.
Define Metrics and KPIs
Determine metrics and KPIs to track program performance and measure risk levels. This provides criteria for assessing effectiveness and guiding resource allocation.
Integrate Other Security Controls
Correlate vulnerability data with other security solutions like SIEM, firewalls, and endpoint detection and response (EDR) to gain additional context for analysis.
Assign Responsibilities
Ensure specific roles and responsibilities are defined across security, IT ops, and development teams for vulnerability tasks.
Establish SLAs
SLAs provide defined timelines for critical vulnerability management lifecycle steps, such as performing scans and remediating high risks.
Implement Training
Team members should receive role-based training on maintaining and executing the vulnerability management program.
Test and Tune the Program
Once implemented, the program should be evaluated and refined through tabletop exercises and drill tests. Process gaps and issues can be identified and addressed.
Set a Review Schedule
A cadence for periodically reviewing and auditing the program should be established so that it continues meeting business needs and evolving alongside the threat landscape.
Key Capabilities for Vulnerability Management Tools
Choosing the right vulnerability management platform is critical. Effective tools typically include capabilities such as:
- Comprehensive vulnerability scanning across networks, endpoints, web applications, cloud environments, mobile devices, containers, OT, and IoT.
- Authenticated scanning that leverages credentials to more deeply probe vulnerabilities affecting operating systems, software, and applications.
- Intelligent prioritization of vulnerabilities based on threat context and business criticality of affected assets.
- Built-in workflows for tracking vulnerabilities through the remediation process.
- Detailed dashboards and customizable reporting for communicating risks and demonstrating compliance.
- Integration with IT ticketing systems for efficient hand-off of vulnerability data between security and IT ops teams.
- Compliance policy templates for standards such as CIS and PCI DSS to accelerate audit preparations.
- API integrations with other security solutions including SIEM, firewalls, and IT management platforms.
Conclusion
A vulnerability management framework provides enormous value for reducing organizational risk. By taking a strategic, metrics-driven approach, security leaders can make continuous progress on closing vulnerabilities before they turn into breaches. While mature vulnerability management takes time to build, organizations can follow the steps and best practices covered here to advance their programs and maximize effectiveness. When implemented well and with full stakeholder support, a solid vulnerability management framework acts as a force multiplier that strengthens defenses across the entire security ecosystem.