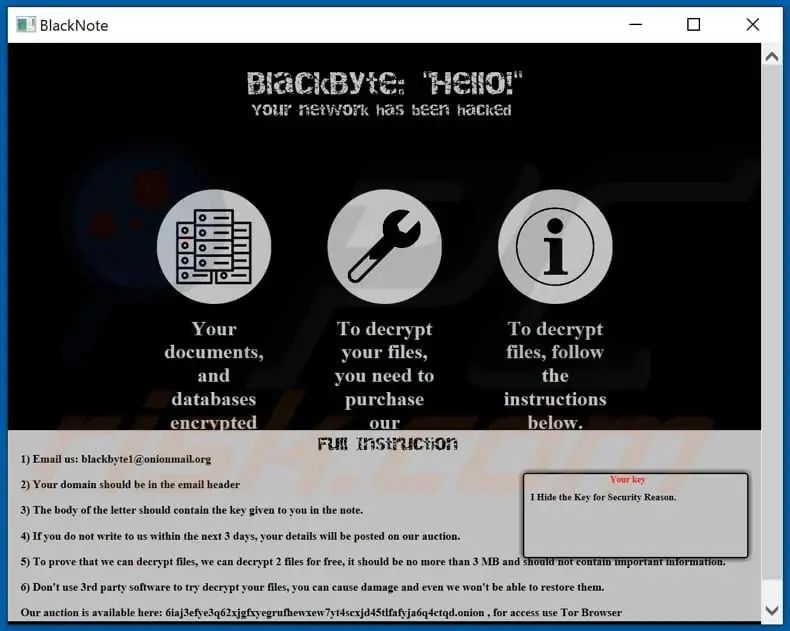
BlackByte ransomware is a type of malicious software that encrypts files on a victim’s computer and demands a ransom payment in order to decrypt the files. It has been actively targeting organizations worldwide since at least July 2021.
What does BlackByte ransomware do?
Like other ransomware, BlackByte gains access to a victim’s system and encrypts files so they can no longer be accessed by the user. Encrypted files are essentially locked until the victim pays the ransom demand. BlackByte targets a wide range of file types for encryption, including:
- Documents
- Images
- Audio and video files
- Email databases
- Source code and databases
In addition to encrypting files, BlackByte may also:
- Disable or tamper with security software to prevent recovery
- Delete volume shadow copies to prevent restoring from backup
- Modify file extensions to .blackbyte making it impossible to open files
- Drop ransom notes demanding payment for decryption
This activity essentially grinds business and operations to a halt for the victim. BlackByte ransomware notes have demanded ransoms ranging from $40,000-$200,000 paid in Bitcoin to receive a decryptor tool.
How does BlackByte infect systems?
BlackByte relies on a few common infection vectors to compromise corporate networks:
- Exploiting vulnerabilities – BlackByte may exploit weaknesses in unpatched software, such as Remote Desktop Protocol, to gain access and then use tools like Mimikatz to steal credentials.
- Phishing emails – Mass emails containing malicious attachments or links can trick users into downloading malware, enabling remote access.
- Compromised credentials – If usernames and passwords are leaked or stolen, BlackByte can log into systems remotely.
- Brute force attacks – Trying common password combinations to guess credentials and access accounts.
Once inside the network, BlackByte abuses administrator privileges to disable defenses, deploy ransomware to devices, and exfiltrate data before encrypting files across the organization.
What are the effects of a BlackByte attack?
BlackByte attacks can severely impact businesses in multiple ways:
- Service outages and disruptions – Encrypted files lead to delays in critical operations, manufacturing, transactions, and customer service.
- Revenue and productivity losses – Outages directly translate to lost business and wages for the duration of the incident.
- Recovery costs – IT spends significant time and resources recovering encrypted systems, even if backups are available.
- Ransom payments – Large Bitcoin payments may be required to obtain a decryption key from the attackers.
- Reputational damage – High-profile attacks can harm an organization’s brand and public image.
- Notification costs – If personal data was compromised, notification and monitoring for impacted individuals may be necessary.
One recent BlackByte victim reportedly faced over $85 million in losses from business and service disruptions after refusing to pay the $12 million ransom.
Who is behind BlackByte ransomware?
BlackByte is believed to be operated by a ransomware group that researchers call “BlackMatter.” BlackMatter first appeared in July 2021 after the shutdown of the infamous DarkSide ransomware service:
- DarkSide shut down operations in May 2021 after the high-profile ransomware attack on Colonial Pipeline disrupted fuel supplies along the U.S. East Coast.
- Security analysts believe BlackMatter includes former affiliates of DarkSide who rebranded to continue deploying ransomware.
- BlackMatter partners provide initial access to corporate networks, while the ransomware developers handle encryption and extortion.
Like other ransomware groups, BlackMatter operates an affiliate model and leverages partnerships with initial access brokers, hacking groups, and money launderers to run a ransomware-as-a-service scheme:
| Partners | Role |
| Affiliates / Brokers | Gain initial access through phishing, exploits, leaked credentials. |
| Devs / Operators | Develop the ransomware payload and manage extortion operations. |
| Money launderers | Cash out ransom payments through cryptocurrency tumblers and exchanges. |
This distributed infrastructure makes disruption difficult. Even if BlackByte itself dissolved, affiliates could likely continue deploying the ransomware or rebrand again.
Notable BlackByte ransomware attacks
Since emerging in mid-2021, BlackByte ransomware has compromised several high-profile organizations globally:
- July 2021 – BlackByte appears in the wild, with researchers connecting it to the BlackMatter ransomware group.
- September 2021 – Australian transportation company Toll Group is hit by a BlackByte attack impacting operations across multiple Asia Pacific countries.
- November 2021 – BlackByte disrupts technical services at Sinclair Broadcast Group, forcing TV stations offline.
- December 2021 – Belgian it services firm EASI impacted by BlackByte, shutting down networks right before the holiday season.
- January 2022 – Ransomware attack attributed to BlackByte hackers disables online networks for The Impossible Missionaries Church of God.
These incidents highlight BlackByte’s willingness to target large multinational corporations in crucial sectors like transportation, media, IT services, and even non-profits. The ransomware continues to pose an active threat.
How can organizations defend against BlackByte?
Preventing BlackByte infections requires layered defenses at multiple levels:
- Keep all software updated – Patching vulnerabilities blocks common intrusion vectors.
- Use strong passwords – Make passwords complex and enable multi-factor authentication.
- Secure endpoints – Deploy antivirus, endpoint detection and response (EDR) tools.
- Train personnel – Educate staff to identify social engineering and phishing attempts.
- Segment networks – Isolate and firewall critical systems to limit lateral movement.
- Air-gap backups – Maintain offline, immutable backups to enable restore after an attack.
Organizations should also have an incident response plan in place to quickly isolate and contain infections before they lead to widespread damage.
Conclusion
BlackByte exemplifies the serious threat posed by ransomware to modern organizations. Its operators cripple businesses by encrypting critical data and only provide decryption keys after large ransom payments. BlackByte relies on affiliates and partnerships to gain access to corporate targets before deploying its ransomware payload across networks. Notable victims include transportation, media, and IT companies suffering massive business disruption. Defending against BlackByte requires security across human, process, and technical levels – training personnel, hardening infrastructure, segmenting access, patching diligently, and maintaining air-gapped backups.