Endpoint detection and response (EDR) and endpoint security are two important cybersecurity capabilities that help protect an organization’s endpoints and networks. While they have some overlap in functionality, there are important differences between the two that organizations need to understand.
In brief, endpoint security refers to traditional antivirus and anti-malware tools that protect endpoints from known threats. EDR provides additional detection and response capabilities to identify and react to advanced threats that may evade traditional endpoint security.
Understanding the key differences between these technologies allows organizations to develop a robust cyber defense strategy. In this comprehensive guide, we will compare and contrast endpoint security vs EDR across a range of factors to provide a clear understanding of their respective strengths and limitations.
What is Endpoint Security?
Endpoint security refers to a range of tools and techniques focused on protecting endpoint devices from cyber threats. Endpoints include devices like desktops, laptops, servers, mobile devices, and Internet of Things (IoT) devices.
Key elements of a solid endpoint security strategy include:
- Antivirus software detects and blocks known malware, viruses, and malicious scripts.
- Host-based firewalls control inbound and outbound connections to prevent unauthorized network access.
- Application control limits which applications can run on an endpoint to prevent potentially risky software.
- Device control regulates access to removable media like USB drives to prevent malware spread.
- Web filtering blocks access to risky or unauthorized websites.
- System hardening involves locking down endpoints by removing unneeded software/services.
Legacy endpoint security tools relied heavily on malware signatures and reputation databases to recognize threats. Modern tools incorporate additional techniques like machine learning and behavioral analysis for improved detection rates.
Overall, endpoint security aims to serve as the primary line of defense against cyberattacks. It focuses on stopping known, commodity threats before they can compromise endpoints. Effective endpoint security helps enforce basic cyber hygiene across an organization’s footprint of devices.
What is Endpoint Detection and Response?
Endpoint detection and response (EDR) is a subset ofendpoint security that emphasizes rapid detection, investigation, and remediation of advanced threats that evade traditional endpoint protection.
Key capabilities of EDR solutions include:
- Continuous monitoring analyzes endpoint activity in real-time to detect anomalies.
- Advanced threat detection uses machine learning and behavioral analysis to identify sophisticated and stealthy attacks.
- Centralized visibility and management provides security teams with comprehensive insight into the threat landscape across all endpoints.
- Alert triage and investigation workflow allows analysts to dig into alerts and potential incidents.
- Threat hunting enables proactive searches across endpoints to uncover lurking threats.
- Automated response and remediation capabilities can isolate infected endpoints, kill malicious processes, and remove malware.
EDR equips security teams with robust tools to hunt for in-progress cyberattacks, visualize their spread, and disrupt malicious activity across endpoints. It works hand in hand with preventive endpoint security to create a complete defense.
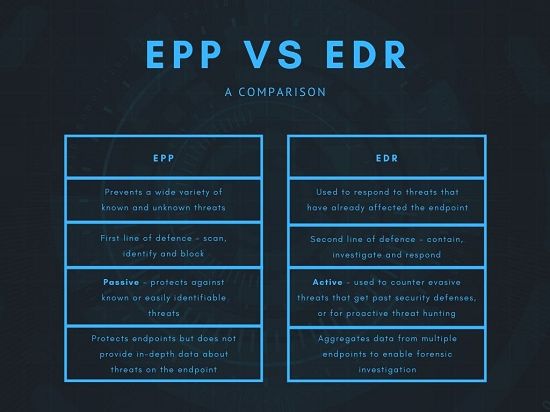
Key Differences between Endpoint Security and EDR
Now that we’ve defined the two technologies, let’s explore the key differences between endpoint security vs EDR in greater detail:
When Threats Are Detected
Endpoint security focuses on preventing threats pre-execution before they can run and cause damage. Signature-based detection and machine learning models aim to block malware and malicious connections.
In contrast, EDR assumes threats will inevitably slip past endpoint security. EDR monitors endpoint activity post-execution to detect threat behaviors that manifest after malicious code runs.
For example, endpoint security might block a phishing email attachment before it launches. But if it gets through, EDR could spot the subsequent suspicious process launches and network connections.
Breadth of Visibility
Endpoint security usually only detects threats at the individual endpoint level. If a device is compromised, security software may alert the local user but has little insight into wider impact.
EDR solutions provide centralized visibility and dashboards across all endpoints. Security teams can quickly determine if a threat is isolated to one endpoint or spreading more widely. This enterprise-wise visibility is critical for an effective response.
Detection Focus
Endpoint security dwells firmly in “known bad” territory. Signatures and reputation data aim to detect and block malware and attacks seen previously. But they struggle to stop never-before-seen threats with no known signature.
EDR uses behavioral analysis and anomaly detection to spotlight “unknown bad.” By analyzing patterns of events and processes, EDR can detect and flag activity that appears suspicious even if the threat is brand new. This allows EDR to stop advanced and novel attacks that evade traditional endpoint protections.
IT Operational Insight
Endpoint security provides limited visibility into overall IT operations. Its focus remains on threat detection rather than analyzing how endpoints function normally.
In addition to threat hunting, EDR gives full insight into routine endpoint activity. Security analysts can get familiar with normal behaviors across endpoints. This allows them to more quickly spot anomalies that could signify threats.
Flexibility of Response
Endpoint security offers fairly basic response options, like quarantining or deleting detected malware. Disruption is limited to the compromised endpoint itself.
EDR enables various flexible response actions that can be taken remotely from the centralized console. Options include isolating endpoints from the network, terminating suspicious processes across endpoints, disabling certain user accounts, and running custom scripts. EDR response also aims to prevent threat spread beyond the patient zero endpoint.
Cloud-Based Options
Endpoint security software has traditionally relied on on-premise architecture. Software agents are installed on each endpoint device. Data remains within the corporate network boundary.
EDR solutions can be deployed on-premise but also embrace cloud-based architectures. Cloud-delivered EDR centralizes data storage, management, and analytics in a hosted provider environment. This removes hardware deployment hassles for enterprises.
Staffing and Skill Requirements
Endpoint security usually involves little specialized expertise. IT generalists can typically handle basic installation, configuration, monitoring, and alert response.
Effective EDR usage requires more advanced skills like threat hunting, deep investigation capabilities, and rapid incident response expertise. Large security teams or managed security service providers are often required to run EDR successfully.
Cost Differences
Endpoint security capabilities are usually bundled into suites that also include firewall, VPN, sandboxing, and other security tools. This makes pricing highly variable but generally affordable for most organizations. Individual endpoint agents can cost less than $10 per device annually.
As a premium capability requiring advanced analytics and staffing, EDR solutions can be significantly more expensive. Some sources estimate average EDR costs at $25 to $50+ per device each year. For advanced use cases, budget even more for additional headcount and services.
When to Use Endpoint Security vs EDR
Now that we’ve thoroughly compared the two technologies, we can offer recommendations on when to deploy endpoint security versus EDR.
Endpoint Security
Every organization should implement baseline endpoint security to enforce cyber hygiene. Antivirus, firewalls, and device controls combine to provide “protection by default” against common threats. Endpoint security lays a universal foundation for cyber defense.
Prioritize endpoint security for:
- General purpose endpoints like employee laptops and desktops.
- Business-critical assets that require fundamental safeguards.
- Widely distributed endpoints like remote workers and IoT devices.
- Any endpoint handling sensitive data.
Endpoint security delivers the greatest value for general IT environments without specialized threat exposure.
Endpoint Detection and Response
EDR fills critical security gaps that remain after deploying endpoint security. It brings advanced threat detection, rapid response, and elite threat hunting.
Organizations that need EDR include:
- Heavily targeted sectors like finance, healthcare, and government.
- Mature security programs looking to improve SOC capabilities.
- Environments with tight regulation and audit requirements.
- Companies reliant on defending intellectual property and trade secrets.
- IT infrastructure exposed to frequent sophisticated threats.
For elevated risk scenarios facing advanced persistent threats, EDR is a must-have rather than “nice to have.”
Using Endpoint Security and EDR Together
Endpoint security and EDR should be used together to maximize protection. Here are best practices for deploying a unified endpoint security and EDR strategy:
- Implement preventive endpoint security widely to block common attacks.
- Deploy EDR on critical assets and likely attack targets to enhance monitoring.
- Integrate EDR with endpoint security data to boost threat visibility.
- Ensure EDR and endpoint security agents coordinate and don’t conflict.
- Feed EDR findings back into endpoint security to block newly detected threats.
- Align workflows across both for consistent incident response.
Follow a tiered model with broad endpoint security coverage and focused EDR enhancements on key assets. Integrate the two approaches to create a comprehensive endpoint defense.
Conclusion
Endpoint security and EDR each offer distinct strengths in protecting modern environments against sophisticated threats. Endpoint security blocks known malware attacks pre-execution. EDR monitors endpoints post-execution to detect stealthy and advanced threats.
While EDR has a higher cost and complexity, its specialized threat detection and rapid response capabilities warrant investment for higher-risk organizations. Optimal endpoint protection requires deploying and integrating both technologies based on an organization’s infrastructure, resources and risk profile.