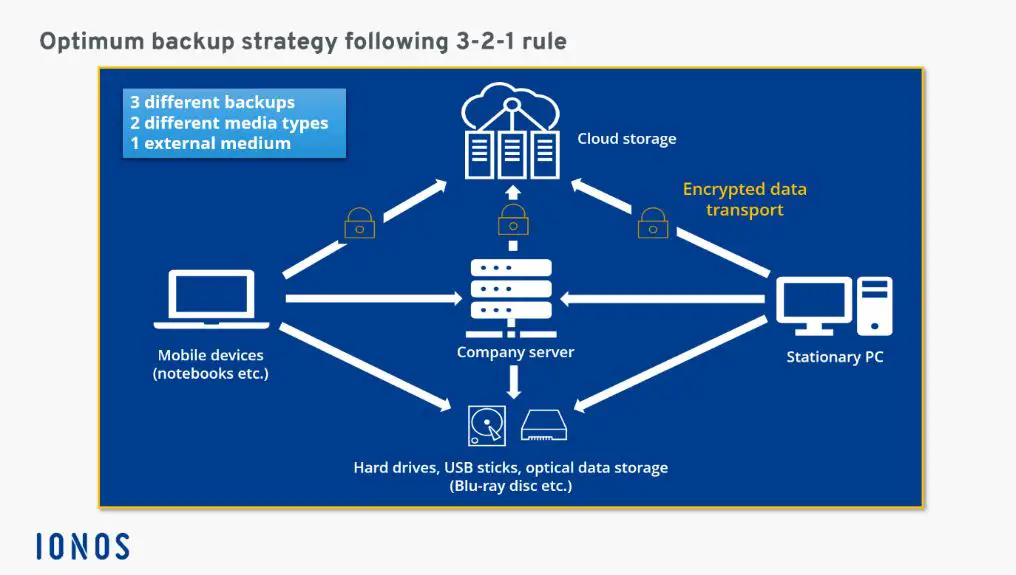
The 3-2-1 backup rule is a best practice for creating resilient and reliable backups. It recommends keeping at least 3 copies of your data, stored on 2 different media, with 1 copy stored offsite. This simple strategy can help protect against data loss from hardware failure, accidental deletion, file corruption, ransomware, natural disasters, and other threats.
Why is the 3-2-1 rule important?
The 3-2-1 rule helps mitigate the risk of data loss by introducing redundancy and media diversity. Here’s why each part of the rule matters:
- 3 copies – Having at least three total copies means you can lose one copy and still recover your data from the remaining two copies. More copies provide additional protection.
- 2 different media types – Storing copies on different media guards against media failure. For example, if your hard drive fails, you can restore from a backup on a separate external HDD or tape.
- 1 copy offsite – Keeping a copy at a remote location protects against localized threats like fire, theft, or natural disaster. The offsite copy ensures you can recover if you lose access to backups stored locally.
Together, these precautions ensure your data remains available in a wide range of failure scenarios. The 3-2-1 rule provides robust, balanced data protection suitable for individuals and businesses alike.
Examples of the 3-2-1 backup rule
The 3-2-1 rule is flexible – it can be adapted to fit any backup environment. Here are some examples of how the rule could be implemented:
Personal computer backups
- Copy 1: Live data on your computer’s internal hard drive
- Copy 2: External USB hard drive stored onsite
- Copy 3: Cloud backup service with offsite storage
Small business server backups
- Copy 1: Production data on the server hard disk
- Copy 2: Nightly backups to an onsite NAS device
- Copy 3: Weekly offsite backups to a cloud storage provider
Enterprise database backups
- Copy 1: Live database server
- Copy 2: Nightly backups to a disk library onsite
- Copy 3: Asynchronous replication to an offsite DR site
These examples illustrate the flexibility of the 3-2-1 rule for single devices, networked servers, and mission-critical systems. The specific media and locations can be adapted to your environment and recovery requirements.
Choosing media for 3-2-1 backups
An effective 3-2-1 backup strategy relies on selecting suitable media for storing your redundant copies. Here are some media types to consider:
External hard drives
External HDDs provide a simple local backup target through USB, eSATA, or FireWire. Look for durable drives with adequate capacity for multiple backups. HDDs offer high reliability for the price but are still vulnerable to physical damage and media failure.
NAS devices
Network-attached storage (NAS) provides disk-based backups accessible from anywhere on your network. NAS devices support automated backup jobs and storage pools that can be expanded over time. However, they are not immune to ransomware which could spread from networked devices to the NAS.
Tape drives
Tape drives can create portable, offline backups not continuously connected to the network. Tape cartridges provide reliable cold storage for infrequently accessed data. However, restoring from tape may be slow, so it should be combined with other media.
Cloud storage
Online cloud backup services offer easy offsite storage over the internet. Cloud storage handles backup automatically and scales to accommodate data growth. Cost, internet bandwidth limits, and latency are constraints to consider.
Removable media
USB flash drives, SD cards, and optical discs provide portable and diverse storage for additional copies. Their small size makes them convenient for offsite use. However, capacity limitations prevent their use as primary backups.
Where to store offsite backups
To complete the 3-2-1 backup rule, one copy of your data must be stored offsite. This protects against disasters like fires, floods, theft, or ransomware impacting your local backups. Typical offsite locations include:
- Cloud storage – Services like Dropbox, OneDrive, and Backblaze offer reliable and convenient offsite cloud backups.
- Remote office – Store a backup in another corporate office not sharing the same disaster risks.
- Trusted acquaintance – Keep a backup drive with a friend or family member outside your region.
- Safe deposit box – Rent a bank safe deposit box for offsite storage of removable media.
- Commercial vaults -Specialized data protection vendors like Iron Mountain provide secure, climate-controlled offsite vaults.
Consider ease of access, security, and geographical diversity when choosing an offsite location. The offsite copy provides your last line of defense if local backups are compromised.
How often to perform backups
Backup frequency should be determined by your recovery point objective (RPO) – the maximum acceptable data loss if a failure occurs. Some common backup intervals include:
- Continuous backups – Critical systems may warrant real-time continuous replication to create backups with an RPO of zero data loss.
- Daily backups – Daily backups provide an RPO of 24 hours and are typical for server environments.
- Weekly backups – Backing up once a week gives an RPO of up to 7 days and may suffice for personal computers.
- Monthly backups – While riskier, monthly backups can be used for rarely changing archival data where some data loss can be tolerated.
Your ideal frequency depends on data change rates, RPO objectives, and how much potential data loss is acceptable. Test restores periodically to confirm backups are working as intended.
Automatic vs manual backups
Backup processes can be performed manually or run automatically on a schedule:
- Manual backups – Require user initiation and intervention each time. Allow for physical media changes but are prone to human error.
- Automated backups – Scheduled by backup software for hands-free operation. Less flexible but ensure consistency without ongoing user effort.
For individual users, a combination of both methods is recommended. Automate routine backups combined with occasional manual whole-disk backups to portable drives for offsite storage.
Businesses should rely on automated backup policies to reduce management overhead and ensure protection is in place. Define backup schedules, retention rules, alerts, reports, and test procedures in your backup policy.
Versioning backups
Backup versioning maintains previous copies of files from different points in time. As data changes, the backup retains multiple iterations of each file. This protects against accidentally overwriting files and provides options to “roll back” to an earlier version if needed.
Versioning increases storage requirements but gives enhanced protection compared to simple overwriting backups. Set the number of versions depending on your storage capacity and retention policies.
Backup method comparison
| Backup type | Versioning | File recovery | Restores prior state |
|---|---|---|---|
| Full backup | No | All files | Yes |
| Incremental backup | No | Latest version only | No |
| Differential backup | No | Latest version only | Yes |
| Versioned backup | Yes | Any version | Yes |
Versioned backups provide the most comprehensive protection. However, multi-versioning capabilities may not be offered on all devices or backup targets.
Backup retention policies
Backup retention policies govern how long backup data is kept before being deleted or overwritten. Typical retention considerations include:
- Recovery window – The time duration you must be able to restore data from backup.
- Compliance – Retention laws related to your data, e.g. medical or financial data.
- Available storage – Storage capacity dictates maximum retention length.
- Backup media lifespan – Retain data within media shelf life, e.g. tape cartridge life expectancy.
Balance these factors to craft retention policies that keep data long enough to meet your recovery and compliance needs without exhausting your storage capacity.
Typical retention policy examples include:
- Daily backups retained for 1 month
- Monthly backups retained for 1 year
- Yearly backups retained for 10 years
Test that old backups can be restored to confirm your retention windows are sufficient for available history.
Options for recovering backups
Several options exist for restoring lost data from properly implemented 3-2-1 backups:
Bare metal restore
Restores the full contents of a system from scratch, including the operating system and applications. Requires a complete system image backup.
File restore
Recovers specific files and folders from a backup without altering the overall system. Useful for retrieving accidentally deleted or corrupted documents.
Application restore
Some applications like Microsoft Exchange provide specialized restore features to roll back the application state without rebuilding the entire server.
Snapshot restore
Reverts an entire system disk to a previous snapshot or backup image. Helpful for ransomware recovery or widespread data corruption.
The right restoration method depends on the scope of data loss and available backup types. Test backup recoverability periodically to verify your plan.
Best practices for backup testing
Testing your backups helps confirm they are working correctly and data can be successfully restored when needed. Here are some best practices for validation testing:
- Test recovery regularly – Monthly or quarterly testing is recommended.
- Test on clone systems – Restore backups on isolated test environments, not production systems.
- Verify backup integrity – Spot check integrity of backup contents before restore.
- Test all backup types – Validate different system, file, and application backups.
- Document results – Record test dates, procedures, results, and recovery rates.
Take corrective actions if any issues are uncovered during testing. Passing tests provide confidence your data is protected.
Potential drawbacks of the 3-2-1 approach
While highly recommended, the 3-2-1 backup rule is not a flawless solution. Some limitations include:
- More storage needed – Multiple copies take more disk space for backup storage.
- Increased costs – Additional hardware, software, cloud storage expenses.
- Complexity – More locations to manage and keep in sync.
- Longer restores – Recovering from offsite media may take more time.
However, most agree the added reliability is worth the effort and costs. Prioritize backups and determine an appropriate budget based on your recovery requirements.
Who should follow the 3-2-1 backup rule?
Due to its versatility and widespread effectiveness, the 3-2-1 backup rule is recommended for:
- Individuals – Protect irreplaceable personal data from loss.
- Businesses – Reduce downtime and ensure availability of critical systems.
- Organizations – Meet data protection obligations for stakeholders.
Any individual or group storing important data digitally can potentially benefit from the 3-2-1 rule. The impacts of data loss often outweigh the minor costs and efforts of proper backups.
Alternatives to the 3-2-1 backup rule
In some situations, other approaches may be warranted instead of traditional 3-2-1 backups:
- High availability (HA) – Clustered servers with failover provide continuous uptime if protected applications go down.
- Cloud-native resiliency – Services like AWS, Azure workloads that leverage distributed redundancy mechanisms.
- Immutable storage – WORM (write once, read many) storage prevents malicious or accidental changes to data.
- Geographic redundancy – Data replicated synchronously across multiple widespread data centers.
However, these can often complement rather than fully replace traditional backups. Evaluate your application architectures and recovery goals to determine suitable data protection schemes.
Conclusion
The 3-2-1 backup rule delivers a time-tested, proven backup strategy embraced by leading data protection experts. While simple in concept, the diligent application of the guidelines provides robust defense against data loss. Organizations can enhance resilience and limit downtime through comprehensive backup policies based on the 3-2-1 rule.
With the ever-growing importance of digital data, proper backups are no longer optional. Ransomware and hardware failure remain ubiquitous threats. Adopting the versatile 3-2-1 approach can cost-effectively backup your irreplaceable data, securing your memories, work, and business against catastrophe.