Ransomware is a type of malicious software that encrypts files on a device and demands payment in order to decrypt them. The 3-2-1 rule is a data backup strategy that can help recover from a ransomware attack.
What is ransomware?
Ransomware is a form of malware that locks access to a computer system or data until a ransom is paid. It works by encrypting files so they cannot be accessed without a decryption key. Once infected, a ransom note is displayed demanding payment within a short timeframe. If the ransom is not paid, the files remain encrypted indefinitely. Ransom demands are often made in cryptocurrency, such as Bitcoin, making payments difficult to trace.
Ransomware attacks have been rapidly increasing, targeting businesses, hospitals, government agencies and individuals. Even with payment, recovering data is not guaranteed. Ransomware exploits human and technological weaknesses to deny access to critical data and systems until ransom demands are met.
How does ransomware infect a system?
Ransomware typically spreads through phishing emails containing malicious attachments or links. Clicking on a link or downloading an attachment allows the ransomware executable file to infect the system. It may also spread through:
- Drive-by downloads from compromised websites
- Remote Desktop Protocol vulnerabilities
- Weak or stolen passwords
- Software or operating system vulnerabilities
Once on a system, ransomware uses encryption algorithms to lock files, making them inaccessible. It may target specific file types such as documents, images, databases and archives. The entire hard drive may be encrypted as well. Then the ransom demand is displayed, often with a deadline before the decryption key is destroyed.
What are common examples of ransomware?
Some well-known ransomware variants include:
- CryptoLocker – One of the earliest ransomware threats, first appearing in 2013. Spread via infected email attachments.
- TeslaCrypt – Targeted gaming files and demanded ransom payment in Bitcoin. Was active from 2015-2016.
- WannaCry – A widespread 2017 attack that exploited Windows vulnerabilities to infect systems. Crippled many organizations globally.
- Ryuk – Targets large enterprises and demands high ransom payments in Bitcoin. Still active in 2022.
- Maze – Exfiltrates data before encrypting files and threatens to publish data if ransom unpaid. Prolific in 2020.
What is the impact of a ransomware attack?
Ransomware can have severe consequences for businesses and organizations, including:
- Loss of access to critical data and systems
- Revenue and productivity losses during downtime
- Costs associated with data and systems recovery
- Reputational damage and loss of customer trust
- Legal and compliance problems
- Payment of large ransom demands
In 2020, the average ransomware payment was over $200,000. Total ransom amounts paid exceeded $350 million that year. Healthcare, education and government entities are frequent targets due to weaker security controls and the critical nature of their systems and data.
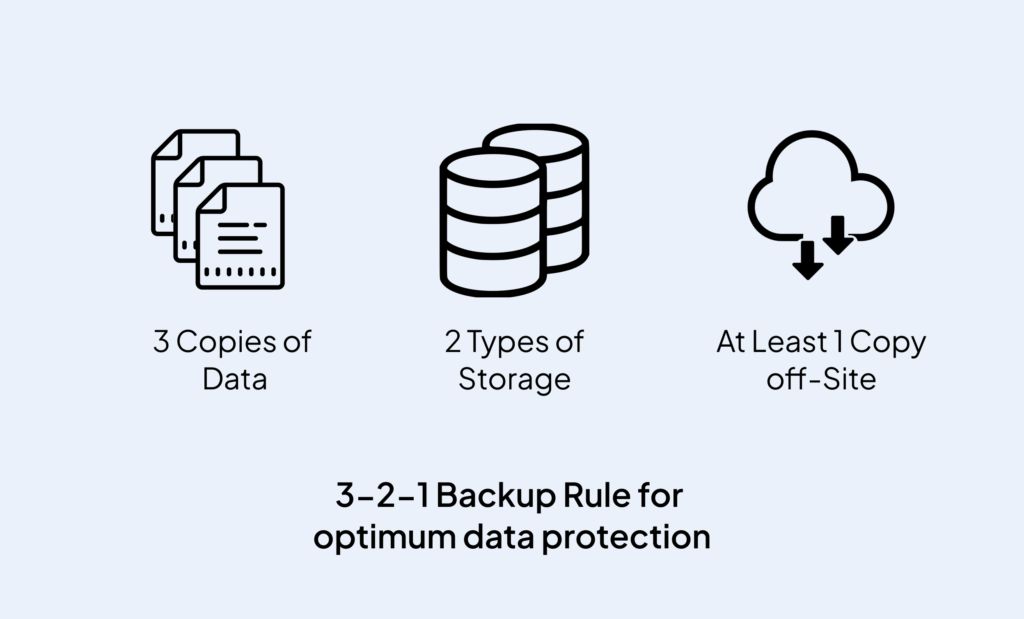
What is the 3-2-1 rule for ransomware protection?
The 3-2-1 rule is a best practice for backing up and protecting data against ransomware and other threats:
- 3 copies of all essential data
- Stored on 2 different media types
- With 1 copy stored offline/off-site
This layered backup strategy prevents data loss and facilitates recovery after an attack. If implemented properly, the 3-2-1 rule means an organization retains access to clean, unencrypted copies of data despite ransomware impacting production systems and live data.
3 copies of data
Maintaining at least three total copies of important files and data provides redundancy. If one or two copies become compromised or fail, another intact copy remains. This protects against accidental deletion, corruption, hardware failure, system crashes and cyber attacks.
2 types of storage media
Storing copies across different media guards against media failure. If a hard drive crashes, for example, data remains accessible from a cloud or tape backup. Recommended storage media options include:
- Cloud storage
- External hard drives
- High-capacity USB drives
- Tape drives
- Network attached storage (NAS) devices
1 offline/off-site copy
One copy of data should be isolated from network and internet access. This offline backup protects against malware reaching and infecting all copies. Offline options include external hard drives and tape systems that are physically isolated or stored offsite. Cloud storage counts as an online copy, not an offline one.
Benefits of the 3-2-1 rule
Adopting the 3-2-1 backup methodology provides powerful ransomware protection along with various other benefits:
- Prevents data encryption – Offline copies remain unaffected by ransomware that encrypts connected systems
- Allows data restoration – Clean backups facilitate complete recovery of files, applications and systems
- Minimizes downtime – Quick access to alternate data copies reduces business disruption
- Avoids paying ransom – Unencrypted backups eliminate the need to pay decryption ransom
- Supports recovery – Multiple copies give flexibility in how systems can be restored
- Protects from other data loss – Safeguards against deletion, corruption, hardware failure, disasters, etc.
Challenges of the 3-2-1 rule
While an effective strategy, the 3-2-1 rule for ransomware resilience also poses some challenges:
- Cost – Requires investment in backup systems, media and cloud repositories
- Complexity – Coordinating processes across multiple media and locations is difficult
- Maintenance – Backup integrity and media health must be verified continuously
- Secure configuration – Offline copies must be fully air-gapped from networks
- Restores – Recovering vast amounts of data is slow and labor intensive
- Versioning – Backups may not have latest data if replication falls behind
How to implement the 3-2-1 rule
Realizing the benefits of the 3-2-1 rule requires meticulous backup hygiene. Vital steps include:
1. Identify critical data
Document the most important data and systems that support critical business operations. These become top priority for backup.
2. Select storage media
Choose a mix of physical and cloud media to serve as backup targets. Options like external drives, tape and cloud repositories each bring advantages.
3. Install and configure backup software
Deploy reliable backup software capable of automating copies to multiple destinations simultaneously. Maintain a routine backup schedule.
4. Isolate offline copy
Completely disconnect one backup copy from networks, either locally using removable media or offsite with cloud storage. This copy cannot be reached by ransomware.
5. Test restores
Periodically restore from backups to ensure the process works properly. This verifies backup integrity and the ability to recover when needed.
6. Monitor backup status
Stay on top of backup health, schedule issues, capacity and media longevity through monitoring and reporting. Proactively resolve any problems.
How the 3-2-1 rule prevents paying ransom
The offline, immutable copy in the 3-2-1 configuration acts as the silver bullet against having to consider paying ransom. When ransomware infiltrates production systems and encrypts live data, this isolated backup copy remains totally unaffected. Restoring data becomes as simple as:
- Wipe and redeploy infected systems from scratch
- Restore data by retrieving the offline backup
- Resume operations from a clean, unencrypted state
Since accessible backups render encrypted production copies useless, the organization regains control without having to consider paying a ransom. Offline copies make data recovery independent of the attacker.
Recovering from ransomware without the 3-2-1 rule
Without a comprehensive 3-2-1 backup scheme, options for recovering from ransomware are limited:
- Pay the ransom – Funds the criminals without guarantee of decryption. Sets dangerous precedent.
- Restore from inadequate backups – Missing critical data results in business disruption.
- Attempt decryption – Only works for unsophisticated ransomware strains with flaws.
- Do nothing – Permanently lose access to encrypted data. Business failure likely.
Each of these carries major drawbacks. The 3-2-1 framework is a proven way to avoid being stuck choosing the least worst option after an attack.
Examples of the 3-2-1 rule stopping ransomware damage
Adhering to the 3-2-1 rule has helped real organizations negate ransomware impact and quickly recover critical data following attacks. For example:
TracksUSA
A precision machining company was hit by a ransomware attack affecting over 100 workstations. However, the 3-2-1 backup rule meant an isolated, unencrypted backup copy existed. This allowed swift recovery of files in just 48 hours instead of paying ransom. Operations were minimally disrupted.
Hancock Health
In 2018, this Indiana hospital system was infected with ransomware that encrypted patient records. Their 3-2-1 backup regimen allowed EHR data restoration without paying ransom. However, they did spend nearly $55,000 on recovery efforts.
City of Lynn
This Massachusetts municipality was struck by ransomware impacting a variety of city systems. Offline backups prevented major disruption or ransom payment. However, restoration and forensic efforts cost over $90,000.
Each example highlights the effectiveness of the 3-2-1 rule in combating ransomware. While not a panacea, it does provide a proven framework for substantially reducing risk and recovery cost.
Table summarizing the 3-2-1 rule components
| Component | Description |
|---|---|
| 3 copies of data | Maintain at least 3 total copies of critical data as redundancy against loss |
| 2 types of storage media | Store copies on different media for availability if one fails |
| 1 offline/off-site copy | Isolate 1 copy from networks to remain inaccessible to ransomware |
Conclusion
Ransomware can inflict tremendous damage to organizations by denying access to systems and data unless ransom is paid. The 3-2-1 rule provides a reliable framework for combating ransomware through layered data backups, including an offline copy out of reach of malicious encryption.
While not infallible, this strategy makes organizations ransomware-resilient by ensuring irreplaceable data remains recoverable without paying ransoms. This minimizes business impact and reduces costs of recovery. Prioritizing robust, redundant and isolated backups is crucial insurance against ransomware and other data loss threats.