An insider threat refers to a security risk posed by someone who has authorized access to an organization’s assets and systems. Insider threats can include current or former employees, contractors, business partners, or anyone else with inside knowledge or access. Some key aspects of insider threats include:
What makes someone an insider threat?
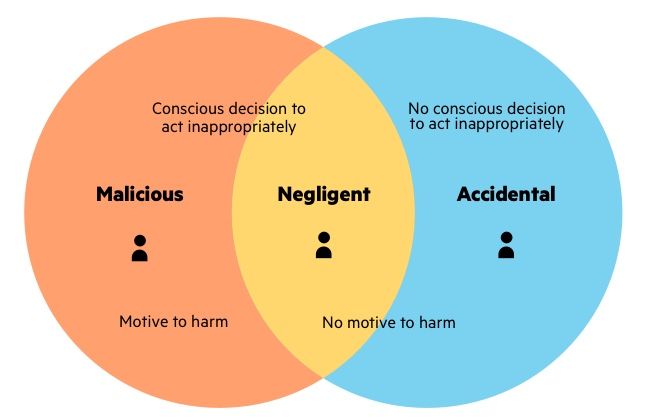
There are a few factors that can turn an otherwise trusted insider into a potential threat:
- Malicious intent – This includes employees or contractors who use their access intentionally to steal data, sabotage systems, or cause other damage.
- Negligence – When insiders misuse systems, improperly handle data, or unintentionally expose sensitive information through poor security practices.
- Compromised credentials – Insiders can become a threat if their login credentials are stolen by an external attacker to gain unauthorized access.
- Disgruntlement – Dissatisfied or former employees who seek to “get back” at the organization by destroying data, leaking information, etc.
While malicious actions get the most attention, negligence and compromised credentials are often overlooked aspects of insider threats. Organizations need policies and technical controls to limit insider access to only what is needed to do their jobs.
What types of actions make insiders a threat?
Some examples of threatening insider actions include:
- Stealing or leaking confidential data – This can include intellectual property, customer information, or other sensitive data.
- Fraud – Using internal systems and access privileges for personal gain.
- Sabotage – Intentionally disrupting operations, deleting critical files, infecting systems with malware.
- Unauthorized snooping – Abusing access rights to spy on other users or view confidential records.
- Policy violations – Breaking security rules such as sharing passwords or using unapproved devices.
- Harassment – Using access to internal systems to stalk or harass other users.
Essentially, any use of privileged access for nefarious, disruptive, unethical or illegal purposes constitutes an insider threat. The damage done can range from reputational harm to disruption of operations to loss of revenue or competitive advantage.
What types of assets are most at risk from insider threats?
Some of the key assets within an organization that insider threats may target include:
- Intellectual property – Product designs, source code, patents, and other IP or trade secrets.
- Customer/employee data – Names, addresses, social security numbers, health records, or other PII.
- Financial information – Accounting data, payroll records, financial reports.
- Strategic plans – Merger/acquisition plans, marketing plans, research data.
- System access – Login credentials, security tools, master passwords.
Insiders often have broad access that lets them take advantage of weak controls around these assets. Strong data encryption, access controls, monitoring, and data loss prevention policies can help mitigate this risk.
What are best practices for preventing insider threats?
A multi-layered strategy is required to counter insider threats. Key elements include:
- Least privilege access – Grant insiders access to only the data and resources needed for their role. Use role-based access controls and segregation of duties.
- Background checks – Thoroughly vet employees and contractors before granting access.
- Training – Educate insiders on security policies and how to protect assets.
- Monitoring – Log, audit, and monitor insider activities to detect unauthorized access attempts.
- Data protection – Encrypt data at rest and in motion, and control use of external storage devices.
- Access controls – Authenticate and authorize all access to assets, factoring in trust levels.
- Incident response – Have a plan in place to quickly detect and respond to potential insider attacks.
Taking a layered approach across people, process, and technology makes it much harder for any individual insider to do harm.
How do organizations assess their risk and exposure to insider threats?
Some ways organizations can assess insider threat risks include:
- User behavior analytics – Look for unusual user activity that varies from norms.
- Data loss prevention – Tools to detect potential unauthorized data exfiltration.
- Honeytokens – Embed fake data that will alert you if accessed.
- Vulnerability assessments – Test your controls by safely attempting unauthorized access.
- Threat modeling – Analyze which assets are most vulnerable and attractive to insiders.
- Culture surveys – Gauge employee morale and identify disgruntlement.
- Access certifications – Require managers to periodically certify employee access needs.
Ongoing risk assessments should be performed to quantify potential insider threat risks based on data sensitivity, number of insiders, controls in place, and detected activity. This enables organizations to focus limited resources on the most likely and impactful risks.
What are some notable examples of insider threats?
Some high-profile insider threat cases include:
| Company | Insider(s) | Incident |
|---|---|---|
| Uber | Former employee | Stole data on 57 million customers and drivers in 2016 and demanded money to delete data. |
| Morgan Stanley | Financial advisor | Stole account data on 350,000 clients and offered to sell it. |
| Equifax | Software developers | Stole sensitive personal data on 148 million consumers in 2017. |
| Employees | Accessed accounts of critics and government officials for spying purposes. |
These examples highlight how even employees of the largest companies can potentially become malicious insiders. The damage done forced new assessments of controls and major reforms at each company.
What laws relate to insider threats?
Key laws dealing with insider threats include:
- Computer Fraud and Abuse Act – Makes it a crime to access a computer without authorization or exceed authorized access to obtain data, defraud, or cause damage.
- Economic Espionage Act – Criminalizes theft of trade secrets to benefit a foreign state or entity.
- Sarbanes-Oxley Act – Requires protections against data destruction or manipulation.
- Privacy laws – Such as HIPAA and GDPR create data privacy and security requirements.
- Intellectual property laws – Make unauthorized use and disclosure of trade secrets illegal.
These laws make organizations legally liable for breaches involving insider threats. They also impose fines and criminal penalties on insiders who steal data or IP.
How do you spot suspicious insider activity?
Some ways to spot suspicious insider activity include:
- Someone accessing data unrelated to their job.
- Unapproved emailing or downloading of sensitive documents.
- Attempts to gain higher data access permissions.
- Signs of unauthorized data being copied off-site.
- A worker suddenly coming in early, staying late, or working odd hours.
- Use of external storage devices against policy.
- Unreported lost hardware like laptops, flash drives, smartphones.
Any significant deviations from normal activity baselines or violations of security policies warrant closer investigation. The goal is early detection before major damage can occur.
What are common insider threat actor profiles?
Some typical profiles of insider threats include:
- The Disgruntled Employee – Feels mistreated and seeks revenge by destroying data or disrupting operations.
- The Manipulated Insider – Tricked by social engineering or compromised by blackmail.
- TheOverburdenedEmployee-Usesunapprovedtoolstofinishworkfaster,leadingtobreaches.
- The Financial Fraudster-Abusesaccesstoprofitthroughsellingdataortradingsecrets.
- TheSpy-StealsIPoraccessesunauthorizeddatatoaidforeignnation.
- The Idealist-Leakssecretstorevealperceivedorganizationalwrongdoing.
Understanding these common profiles helps focus insider threat detection and mitigation strategies.
How can you encourage employees to report suspicious activity?
Some ways to promote internal monitoring and reporting of risks include:
- Create an anonymous insider threat reporting channel.
- Train employees to recognize and respond to suspicious or unauthorized activities.
- Foster an ethical culture where employees are not punished for honest mistakes.
- Provide incentives for uncovering significant risks or incidents.
- Protect whistleblowers from retaliation.
- Increase awareness of the impacts of insider threats.
- Encourage peer monitoring to detect colleagues behaving in an unusual manner.
Insiders often observe suspicious activity before major damage occurs. Providing safe, anonymous reporting channels increases this vital early detection and response capability.
What policies help prevent insider threats?
Some important policies that can mitigate insider threats include:
- Least privilege access – Only provide access to assets required for a user’s duties.
- Background checks – Fully vet employees and contractors before granting access.
- Password policies – Require strong, unique passwords that are regularly changed.
- Multi-factor authentication – Strengthen access controls for sensitive systems.
- Data classification – Identify sensitive data to guide access controls and encryption.
- Encryption – Protect data at rest and in motion from unauthorized access.
- Remote access – Limit connectivity to internal systems and monitor activity.
- Access reviews – Periodic certification of user access by managers.
These policies reduce opportunities for insiders to leverage access privileges for malicious purposes. Strict enforcement is necessary for effectiveness.
How can you limit damage from rogue insiders?
Steps to limit damage from rogue insiders include:
- Use data loss prevention tools to block unauthorized sensitive data exfiltration.
- Segment the network to restrict lateral movement.
- Implement rapid system lockout when suspicious activity is detected.
- Conduct frequent backups and redundant data storage to enable recovery.
- Log, monitor, and audit user activity to create an access trail.
- Require heightened validation for access to the most sensitive assets.
- Have an incident response plan ready to contain a breach by isolating systems and data.
The goal is to significantly raise the difficulty for an insider to access and abuse the most critical assets and systems. This will limit the potential scale and duration of an attack.
What are the unique challenges in detecting insider threats?
Some key challenges with spotting insider threats include:
- Trusted insiders don’t trigger perimeter defenses and have appearance of legitimacy.
- Broad access rights of many users prevent effective separation of duties.
- Difficult to discern intent – many insiders don’t realize or acknowledge their own threats.
- Encryption and remote work make data exfiltration harder to detect.
- Long tenures build deep knowledge of vulnerabilities.
- User activity monitoring faces privacy concerns.
- Threats from negligence often have no attacking behaviors to trigger alerts.
These factors often allow insider threats to hide in plain sight. Custom, context-aware behavioral analytics are needed versus more binary perimeter controls.
How can you balance insider threat monitoring with user privacy?
Strategies to address privacy concerns include:
- Establish data handling policies that limit collection and govern use cases.
- Anonymize collected activity data to remove personally identifiable information.
- Provide clear notice to users about monitoring activities.
- Only collect activity data needed to detect threats and minimize storage periods.
- Allow users to review and contest any information collected about them.
- Train personnel managing monitoring programs to handle information ethically and confidentially.
- Get legal guidance to ensure programs comply with privacy regulations.
Privacy and insider threat monitoring objectives both aim to protect the organization and its users. Open communication, limited data collection, and ethical controls help maintain trust.
Conclusion
Insider threats present a complex, persistent security challenge due to the inherent trust placed in employees, partners, and other insiders. Mitigating these risks requires a multifaceted program including access controls, monitoring, training, and policies that balances security, privacy, and productivity. By understanding different insider threat profiles, tactics, and early warning signs, organizations can develop intelligence-driven solutions tailored to their specific risks. Ongoing vigilance and collaboration between security, HR, legal, and executives is key to protect critical assets from abuse of privileged access while enabling users to do their jobs. Insider threats will continue to evolve alongside technology, but with proper planning and precautions, organizations can minimize both the likelihood and the impacts of attacks.