Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks are two of the biggest threats facing websites and online services today. Both types of attacks aim to make a website or online service unavailable to legitimate users by flooding it with fake traffic. However, DoS and DDoS attacks work in slightly different ways. This article will explain the key differences between DoS and DDoS attacks, providing a useful study guide for anyone looking to learn more about these threats.
What is a DoS attack?
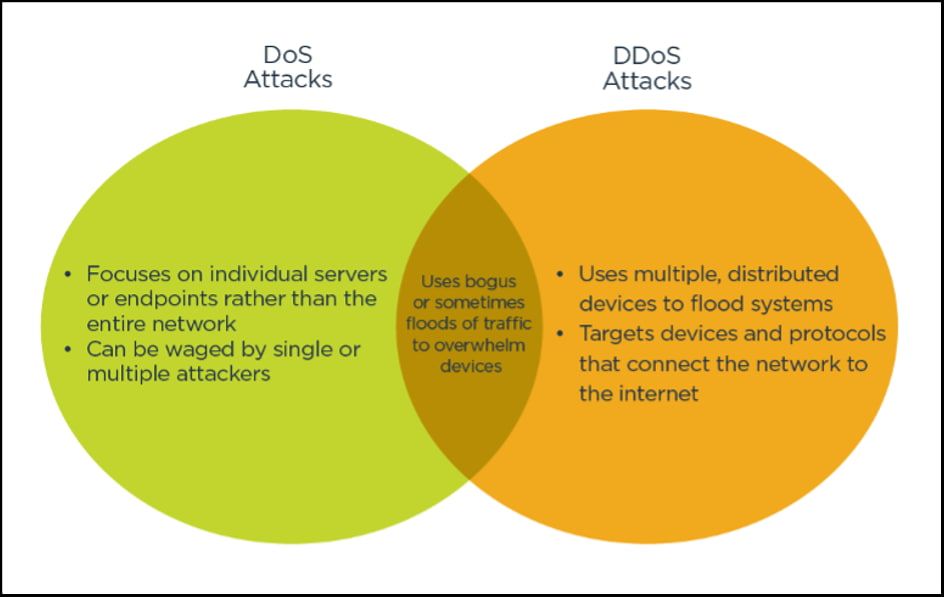
A denial-of-service (DoS) attack is when a single machine, often controlled by a hacker, floods a targeted website, server or network with fake traffic in an attempt to overload systems and make the site unavailable. DoS attacks typically work by exploiting vulnerabilities in the target’s system that allow the hacker to consume excessive amounts of limited resources on the server, such as CPU, RAM or bandwidth.
Some of the most common DoS attack types include:
- Buffer overflow attacks – where the hacker sends more data to the buffer than it can handle, causing it to overflow.
- Ping floods – a basic attack where the hacker overwhelms the target with ICMP echo requests (pings).
- SYN floods – the hacker sends continuous SYN requests to a server but does not complete the TCP handshake, exhausting connection resources.
The impact of a successful DoS attack can include:
- The target website or server crashing and becoming unavailable.
- Poor network performance and slow loading times for legitimate users.
- Reputational damage and loss of user trust in the website or service.
What is a DDoS attack?
A distributed denial-of-service (DDoS) attack occurs when multiple machines, often infected with malware and controlled by a hacker, work together to target and overwhelm a website or online service. DDoS attacks are much larger in scale than DoS attacks because the incoming traffic is distributed between many different sources.
To launch a DDoS attack, hackers will typically infect thousands of vulnerable internet-connected devices, such as PCs and IoT devices, with malware. This network of devices becomes known as a botnet. The hacker can then order the botnet to simultaneously send requests to the target website or server, mimicking legitimate user traffic. This vastly multiplies the scale of the attack traffic compared to a DoS attack from a single source.
Some common DDoS attack vectors include:
- Volume-based attacks – attempts to saturate the network bandwidth of the target with huge amounts of bogus traffic.
- Protocol attacks – focuses on exhausting connection resources by exploiting vulnerabilities in Layer 3 and Layer 4 network protocols.
- Application layer attacks – targets web server resources and APIs with bogus requests.
The impact of DDoS attacks can include:
- Complete denial of service, crashing the website/server due to resource exhaustion.
- Degraded performance – slow loading times and timeouts for legitimate users.
- Reputational damage, loss of revenue, and customer churn.
Key differences between DoS and DDoS
While DoS and DDoS attacks share the same goal of denying legitimate users access to online services, there are some key differences between the two attack types:
| DoS | DDoS |
|---|---|
| Originates from a single source (IP address). | Involves multiple attack sources distributed globally. |
| Relatively low volume of attack traffic. | Massively higher volume of aggregated traffic from multiple botnet nodes. |
| Exploits system vulnerabilities. | Typically overwhelms bandwidth and infrastructure. |
| In most cases, the attacker wants to target a specific organization. | The hacker’s motivations can vary from financial, ideological to just causing disruption. |
| Technically less complex to execute. | Setting up and controlling a large botnet requires greater expertise. |
In summary, while DoS and DDoS have the same negative effect, DDoS attacks pose a greater threat as they are much harder to mitigate due to the distribution of attack traffic. DoS attacks from a single IP can be easily blocked with firewall rules, whereas blocking all members of a large botnet is extremely difficult.
Common DDoS attack tools
DDoS hackers employ a range of malware tools and botnet platforms to launch attacks at scale. Some of the most common DDoS weapons observed in recent attacks include:
- Mirai – An infamous IoT botnet malware first seen in 2016. It spreads by scanning for insecure IoT devices like cameras and DVRs and brute-forcing access via default passwords.
- Darkai – An evolved version of Mirai which adds exploits for vulnerabilities in IoT devices. More advanced but limited distribution so far.
- Tsunami SYN flood tool – Delivers high-intensity attacks using SYN flood techniques which overwhelm server resources with TCP SYN requests.
- Fbot – An Android-based botnet malware which abuses misconfigured Memcached servers to amplify DDoS firepower.
- MRCRT – China-linked malware that exploits vulnerabilities in IoT devices and Linux servers.
These tools allow even unskilled attackers to launch destructive DDoS attacks by simply renting access to established botnets. DDoS-for-hire services provide users with point & click tools to target any chosen website or server.
Common DoS attack tools
While less complex than DDoS attacks, DoS attacks can still be launched fairly easily using a number of available tools, including:
- LOIC – Open-source DoS tool that floods targets with TCP, UDP and HTTP requests. Often misused by novice hackers.
- HOIC – A more powerful DoS tool based on LOIC, providing a simple web-GUI for users to input target details.
- XOIC – Enhanced version of HOIC featuring SSL support and configured list of attack types.
- SlowHTTPTest – Simple DoS tool that focuses on using slow HTTP requests to overwhelm web server resources.
- R-U-Dead-Yet – Specialized HTTP DoS tool designed to consume web server resources and take sites offline.
While these tools make launching basic DoS attacks relatively easy, sustaining attacks for longer periods often requires more technical expertise. DoS attacks from a single source IP are also fairly easy for providers to mitigate once detected.
Defending against DDoS vs DoS
Mitigating the threats posed by DDoS and DoS attacks requires layered defenses and constant vigilance. However, defending against distributed multi-vector DDoS assaults requires significantly more advanced techniques and solutions. Some key considerations for mitigating DDoS vs DoS include:
For DoS defense:
- IP blocking and connection rate-limiting of suspicious traffic sources.
- OS and application patching to remove vulnerabilities.
- Enforcing strong password policies on Internet-facing assets.
- Upgrading server capacity and bandwidth to improve resilience.
- Blacklist blocking of known DoS tool signatures.
For DDoS protection:
- Hybrid on-premise and cloud DDoS protection solutions.
- Service provider assistance – such as through BGP flowspec, to block attack traffic upstream.
- Always-on network monitoring to quickly detect attacks.
- Proactive website content caching via CDNs to absorb some attack impact.
- Adopting best practices from frameworks such as the DDoS Resilience Report.
While DoS can often be handled internally, complex DDoS scenarios usually require assistance from experts – such as an emergency response service. The distributed nature of DDoS means attacks can overwhelm internal network capacity quickly before protections are activated.
Legal implications
Both DoS and DDoS attacks are illegal. Acts that deny services to legitimate users violate cybercrime and computer abuse laws in jurisdictions globally. Some key legal considerations around DoS vs DDoS include:
- DoS attacks may constitute a breach of the Computer Fraud and Abuse Act (CFAA) in the US, carrying criminal penalties.
- Launching DDoS attacks involving botnets of compromised computers can result in charges of computer intrusion and wiretapping.
- Hiring DDoS-for-hire providers (“booters”) also carries criminal liability.
- DDoS perpetrators can face felony charges and prison time if caught and prosecuted.
- DOs/DDoS attacks against government agencies and public infrastructure may prompt heavier fines and sentencing.
While basic DoS using downloadable tools may be treated more leniently when involving naive users, law enforcement agencies are increasingly willing to pursue charges, especially for repeat offenses.
Those whose systems are hijacked into botnets are generally not criminally liable, but failing to take reasonable security precautions could lead to civil suits for negligence.
Preparing for certification exams
Understanding the key differences between denial-of-service vs distributed denial-of-service attacks is an important learning objective for information security certification exams, including:
- CISSP – DoS and DDoS are included in the Security Operations domain.
- CISM – Covers DoS/DDoS threats and mitigations as part of Information Security Incident Management.
- CEH – Extensive coverage of DoS/DDoS tools, techniques and how they work.
- CompTIA Security+ – Test candidates on DoS/DDoS concepts as part of Threats, Attacks & Vulnerabilities.
- CCNA CyberOps – DoS/DDoS covered under Threat Analysis and Computer Network Defense topics.
Key focus areas for exam prep around DoS vs DDoS include:
- Understanding DoS vs DDoS terminology, tools and methodologies.
- Typical impacts of successful attacks.
- How botnets work and are created.
- Approaches for detection, mitigation and prevention.
- Legal/compliance issues around DoS/DDoS attacks.
Candidates should aim to understand DoS/DDoS beyond just textbook definitions – such as real-world threat trends, tangible impacts, and practical steps to improving resilience. Hands-on exposure to attacks and defenses using labs and simulations can be very helpful for exam preparation.
Conclusion
In summary, while denial-of-service and distributed denial-of-service attacks share the same goal of disrupting online services, DDoS attacks pose a greater threat due to the use of botnets to generate traffic from multiple locations. DoS remains a concern, but modern web applications and servers can be resilient to attacks from single sources through techniques like rate limiting. Combating threats as complex as DDoS however requires specialized solutions and service providers capable of traffic scrubbing at scale.
For exam candidates and security practitioners, understanding the contrasts in origin, methodology and mitigations for DoS vs DDoS will ensure they have the knowledge needed to defend against both threats. Hands-on learning around realistic attacks scenarios is also invaluable. As web traffic continues to grow and new vectors like IoT botnets emerge, maintaining strong DDoS defenses will be a fundamental requirement for online business continuity.