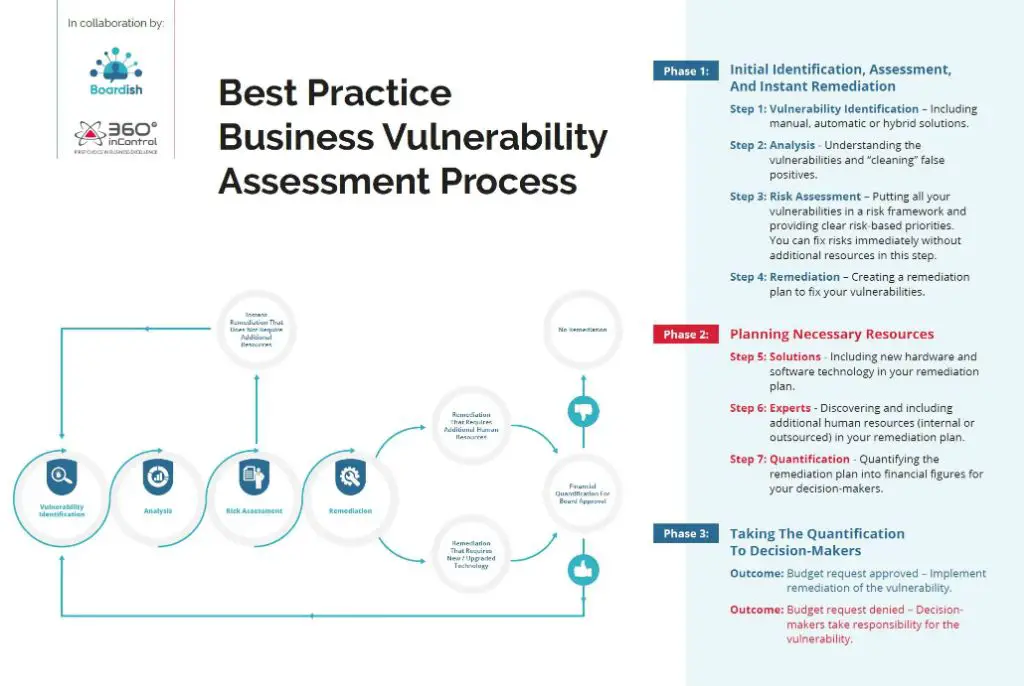
The first step in identifying vulnerabilities is to understand what vulnerabilities are and why they matter. Vulnerabilities are weaknesses or gaps in a system’s security that could be exploited by an attacker. Identifying vulnerabilities is a critical part of cybersecurity and risk management because it allows organizations to find and address security flaws before they lead to breaches or other incidents.
Why is vulnerability identification important?
There are several key reasons why identifying vulnerabilities is a crucial first step:
- It enables proactive security – Finding vulnerabilities before attackers do allows organizations to fix the problems on their own terms.
- It reduces risk – Discovering and remediating vulnerabilities lowers the chances of a successful cyber attack and its potential impacts.
- It informs defense strategies – Understanding weakness points guides efforts to strengthen security controls and response plans.
- It supports compliance – Many regulations and standards require vulnerability management programs to maintain compliance.
In short, effective vulnerability identification provides the foundation for managing security risks and protecting against emerging threats. Organizations that regularly search for and remediate vulnerabilities can detect issues early, prevent incidents, and demonstrate proper security due diligence.
What are the key vulnerability categories?
Vulnerabilities can be organized into a few major categories based on the asset or area they impact:
- Network vulnerabilities – Flaws in network design and configuration, such as open ports or default passwords, that expose networks to attacks.
- Endpoint vulnerabilities – Weaknesses in end user devices like lack of patching or misconfigurations that open endpoints to compromise.
- Application vulnerabilities – Bugs or logic flaws in software code that cause failures in data validation, memory management, etc.
- Human vulnerabilities – Gaps in staff cyber awareness, social engineering susceptibility, and security policy compliance.
- Physical vulnerabilities – Inadequate controls around facility access, asset storage, or other on-site security issues.
Understanding these categories helps teams scope vulnerability management activities and focus on high risk areas.
What are common sources of vulnerability data?
There are many sources organizations can leverage to uncover vulnerability data:
- Asset inventories – Detailed lists of hardware, software, applications, and services in the environment.
- Automated scans – Network, endpoint, application, and cloud scanning tools and technologies.
- Penetration testing – Simulated attacks by ethical hackers to probe for weaknesses.
- Open source research – Public vulnerability databases, vendor notifications, and threat feeds.
- Risk assessments – Reviews of security controls, processes, architectures, and staff behaviors.
- Audits – Examinations of policies, procedures, and systems configurations.
Combining automated scanning with human-driven assessments provides the most thorough vulnerability identification. Prioritizing based on criticality also helps focus on assets that need the greatest attention.
What are the steps of the vulnerability identification process?
An effective vulnerability identification process generally involves the following key steps:
- Define scope – Determine which assets, systems, locations, and stakeholders are in scope for assessments.
- Discover assets – Build as comprehensive an inventory as possible of technology, applications, tools, and other assets.
- Run automated scans – Configure network, endpoint, web application, and other scans to run on a scheduled basis against in-scope assets.
- Perform human-driven testing – Conduct penetration tests, red team exercises, social engineering tests, and physical security reviews.
- Gather intelligence – Monitor threat feeds, vendor notifications, and patch releases to stay on top of disclosed vulnerabilities.
- Review configurations and controls – Examine system settings, account permissions, data flows, and security tools for weaknesses.
- Analyze and prioritize findings – Score vulnerabilities based on severity and asset criticality to focus remediation.
- Report and track issues – Document vulnerabilities in detail with risk ratings and mitigation steps in a tracking system.
- Remediate problems – Isolate, patch, upgrade, replace, remove access, or take other actions to fix or reduce vulnerabilities.
- Verify resolution – Rescan, retest, or recheck areas after remediation to ensure vulnerabilities are properly addressed.
This process needs to be continuous and repeat on a regular schedule to maintain visibility and control over the vulnerability landscape.
What are the key elements of a vulnerability management program?
A comprehensive vulnerability management program requires the following fundamental components:
- Asset inventory – A verified listing of systems, software, devices, and applications in the environment.
- Discovery and identification – Tools and processes to continuously unearth new vulnerabilities.
- Risk analysis – Standards for evaluating and rating vulnerability severity and asset criticality.
- Reporting and metrics – Means of documenting findings, tracking status, and measuring program results.
- Remediation – Resources and workflows for fixing or reducing vulnerability risks.
- Verification – Validation testing to confirm vulnerabilities are addressed.
- Governance – Assignment of roles, responsibilities, and accountabilities across teams.
- Education – Ongoing training on technologies, tools, processes, and vulnerabilities.
With these elements in place, organizations can systematically find, evaluate, and resolve security weaknesses before they lead to incidents. Vulnerability management programs require time and expertise to build but are one of the most impactful cybersecurity investments an organization can make.
What are some common challenges in vulnerability management?
While critical, vulnerability management faces a few typical challenges:
- Shadow IT – Unknown assets and tools that fall outside the centralized program.
- Detection gaps – Scanners miss vulnerabilities that require manual testing to find.
- Prioritization difficulties – Challenges accurately defining asset criticality and vulnerability severity.
- Poor data context – Lack of business impact details for found vulnerabilities.
- Reporting/metrics ambiguity – Unclear benchmarks for program reporting and success measurement.
- Patching roadblocks – Hurdles in testing and deploying patches, especially for legacy systems.
- Verification obstacles – Ensuring all instances of vulnerabilities are fully addressed across environments.
Organizations need to invest in the right tools, talent, and processes while centrally governing vulnerability management to overcome these common issues.
What tools and technologies support vulnerability management?
Some of the key categories of tools that enable effective vulnerability management include:
- Asset inventory tools – Software and hardware asset management, configuration management databases (CMDB).
- Vulnerability scanning tools – Network, endpoint, application, and cloud scanners.
- Penetration testing tools – Tools for ethical hacking, social engineering, physical testing.
- Threat intelligence platforms – Centralized data on disclosed vulnerabilities, emerging threats.
- Risk analysis tools – Vulnerability scoring, asset criticality ranking, and risk calculation.
- Ticketing/tracking systems – Issue documentation, assignment, and lifecycle monitoring.
- Reporting tools – Automated report generation with custom queries and dashboards.
- Patch management tools – Automated deployment and verification of patches across assets.
Orchestrating these tools under a central vulnerability management platform helps streamline identification, analysis, and remediation workflows.
What security standards include vulnerability management requirements?
Many cybersecurity standards and regulations include specific directives around vulnerability management, such as:
- ISO 27001
- NIST CSF
- CIS Critical Security Controls
- PCI DSS
- HIPAA
- SOX
- GLBA
For example, the Payment Card Industry Data Security Standard (PCI DSS) requires the following vulnerability management activities:
- Maintain an inventory of systems and software.
- Perform quarterly internal and annual external vulnerability scans.
- Address vulnerabilities that exceed scan risk thresholds.
- Retest and validate remediated vulnerabilities.
Adhering to applicable standards demonstrates due care and reduces compliance audit findings.
How can machine learning and AI help?
Advances in machine learning and artificial intelligence are providing new ways to enhance vulnerability management programs, such as:
- Discovering assets and cataloging inventories faster.
- Accelerating vulnerability scanning and expanding coverage.
- Automatically classifying and scoring vulnerabilities by severity.
- Using algorithms to define asset criticality based on behavior and dependencies.
- Predicting vulnerabilities that are likely to arise in systems.
- Recommending and prioritizing fixes based on risk and business impact.
- Continuously monitoring threat feeds and advisories about new flaws.
As the use of AI and ML grows, vulnerability management programs can leverage intelligent technologies to scale analysis and automation.
What are some key vulnerability management best practices?
Organizations should follow these recommended practices to mature their vulnerability management programs:
- Discover your full asset inventory and keep it continuously updated.
- Use multiple scan engines and technologies to maximize vulnerability detection.
- Validate your controls inventory and third-party risk levels annually.
- Include vulnerability identification in change management and project lifecycles.
- Integrate scanning and testing tools into central dashboards and workflows.
- Define, document, and standardize rational, repeatable processes.
- Provide regular vulnerability management training and communications to staff.
- Protect scan findings and schedule scans to minimize business disruption.
- Align KPIs and metrics to key business risks, assets, and objectives.
By making these practices standard, organizations can drive continuous improvement in vulnerability management and risk reduction over time.
Key Takeaways
- Identifying vulnerabilities through scanning, testing, audits, and threat monitoring is the foundation of cyber risk management.
- Asset discovery and inventory are the critical first steps in establishing visibility over the attack surface.
- Vulnerabilities span networks, endpoints, applications, humans, and physical spaces.
- Both automated scanning and manual reviews by experts are required for comprehensive results.
- Detailed reporting, tracking, analysis, and verification of issues is necessary to drive effective remediation.
- Integrated processes, governance, metrics, and tools are key to successful vulnerability management at scale.
By taking a strategic, programmatic approach, organizations can find and remediate vulnerabilities before they turn into breaches. Comprehensive vulnerability identification provides the visibility required to assess and control cyber risks.