Endpoint security has become increasingly important as businesses adopt flexible and remote work policies. Protecting devices like laptops, smartphones, and tablets is critical to securing corporate infrastructure and data. Read on to learn more about why endpoint security matters and how it can be implemented effectively.
What are endpoints?
An endpoint is any device that can connect to a network. This includes computers, phones, tablets, printers, security cameras, medical devices, and more. Endpoints represent potential entry points into corporate systems for cybercriminals. As such, securing endpoints is a key component of any cybersecurity strategy.
Some common types of endpoints include:
- Laptops
- Desktop computers
- Smartphones
- Tablets
- IoT devices
- Servers
- Cloud storage
- POS terminals
Endpoints can be company-owned or BYOD (bring your own device). Employees may use personal devices like phones and tablets for work purposes. These endpoints also need protection when accessing company apps and data.
Why is endpoint security important?
There are several key reasons why endpoint security has become so crucial:
- Remote work: With more employees working remotely, corporate networks extend beyond office firewalls. Sensitive data is often stored and accessed on remote endpoints.
- BYOD policies: Allowing personal devices enables flexibility but also introduces new risks if those devices are not secured.
- Mobility: The ability to work anywhere means more devices traveling outside the office, increasing the risk of loss or theft.
- Target surface: There are simply more devices than ever for hackers to target, especially with the growth of IoT.
- Direct access: Compromising an endpoint could allow direct access to company servers and internal networks.
- Malware: Phishing, viruses, and other malware often first infect endpoint devices.
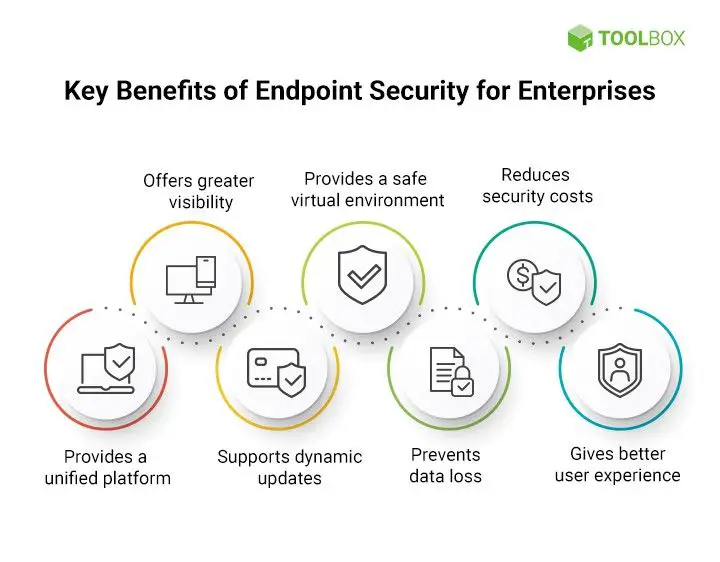
Ultimately, endpoints are attractive targets for cybercriminals and a leading source of data breaches. Securing these access points is critical for any organization.
What are the consequences of poor endpoint security?
Neglecting endpoint security can leave businesses vulnerable in multiple ways:
- Data breaches resulting from hacked endpoints can lead to loss of sensitive information like customer data or intellectual property.
- Unsecured endpoints are more likely to be infected with malware, ransomware, and viruses that can spread across the network.
- Loss or theft of an endpoint could result in unauthorized access to internal systems.
- Out-of-date, misconfigured, or unpatched software on endpoints heightens vulnerability.
- Lack of visibility into all connected endpoints limits the ability to assess risks.
- Insufficient access controls and passwords on endpoints increase the risk of unauthorized access.
- Regulatory non-compliance and legal liabilities can arise from insufficient endpoint security.
- Overall costs – financial, legal, PR – increase following an endpoint-related breach.
For these reasons, all organizations need to make endpoint protection a high priority.
What are the key elements of effective endpoint security?
A comprehensive endpoint security strategy should include these core elements:
- Device management: Maintain an inventory of endpoints and ensure needed software/settings are applied through centralized management.
- Monitoring and visibility: Continuously monitor endpoints for threats and anomalous activity.
- Anti-malware/antivirus: Install antivirus software on all endpoints to detect and remove malware.
- Access controls: Enforce authentication and restrict endpoint access to authorized users and trusted networks.
- Encryption: Encrypt endpoint hard drives and data to prevent unauthorized access.
- Firewalls and network security: Limit inbound/outbound connections to prevent untrusted network traffic.
- Patch management: Regularly install critical software updates and patches on endpoints.
- Data protection: Use data loss prevention and rights management to protect sensitive data.
Additional elements like mobile device management (MDM), virtualization, and advanced threat detection also strengthen endpoint defenses.
Endpoint security best practices
Organizations should follow these endpoint security best practices:
- Have a comprehensive endpoint protection policy covering acceptable use, access, data storage, etc.
- Only allow trusted, authorized devices to connect to corporate networks.
- Install antivirus/anti-malware on every endpoint and update definitions regularly.
- Encrypt endpoint hard drives using BitLocker (Windows) or FileVault (Mac).
- Use two-factor authentication for any endpoint accessing sensitive data.
- Regularly patch and update operating systems and software.
- Disable USB drives and limit external connections to prevent unauthorized data transfer.
- Automatically disable inactive endpoints after a set period of time.
- Install mobile device management (MDM) profiles on BYOD devices to enforce security policies.
- Back up endpoints regularly to enable rapid recovery if infected.
Following these steps will greatly reduce endpoint vulnerabilities and improve overall security posture.
Choosing an endpoint security solution
The right endpoint security solution depends on a company’s specific needs and infrastructure. Key criteria to consider include:
- Platform support – Ensure the product works across all endpoint operating systems in use, including mobile devices.
- Management – Centralized management and monitoring capabilities for streamlined administration.
- Threat prevention – Real-time anti-malware, firewalls, and IDS/IPS capabilities.
- Data controls – Data loss prevention, encryption, access controls, and rights management features.
- Zero trust access – Prevents lateral movement across network with microsegmentation and least privilege access.
- Visibility and analytics – Dashboards and detailed reporting into endpoint activity and violations.
- Automation – Capabilities like automated policy enforcement, software deployment, vulnerability scanning, and patches.
- Cost – Total cost of ownership including license fees, maintenance, installation, training, etc.
Leading options include solutions like CrowdStrike Falcon, Microsoft Defender for Endpoint, and Cisco Secure Endpoint. The cloud is increasingly used for streamlined management and intelligence sharing across endpoints.
Implementing effective endpoint security
Properly implementing endpoint protection involves these key phases:
Discovery and inventory
Discover all endpoints across the corporate infrastructure and compile them into a central inventory. This provides visibility into security coverage gaps.
Risk analysis
Analyze the risks associated with different endpoint types and usage scenarios. This enables policies and controls to be tailored to varying risk levels.
Policy definition
Define comprehensive policies for access, acceptable use, patching, encryption, data transfers, and other areas. Policies provide enforceable standards for endpoint security.
Deployment
Deploy chosen endpoint security software, management servers, and agents across endpoints enterprise-wide. Onboard all endpoints into centralized management system.
Configuration
Configure policies, profiles, and settings tailored to different endpoint types. Enable key protections like antivirus, firewalls, and encryption based on defined policies.
Training and awareness
Educate employees on endpoint security best practices for maintaining data security and complying with policies.
Monitoring and maintenance
Continuously monitor endpoints using management dashboards and alerts. Tune policies and maintain software deployments to ensure optimal effectiveness over time.
This lifecycle approach helps bake endpoint security into business processes for maximum impact.
Endpoint security challenges
While critical, endpoint security does involve some key challenges:
- User productivity – Security controls and software can negatively impact performance and user experience.
- Compatibility issues – Complex endpoint environments make it hard to standardize security tools and policies.
- Alert fatigue – Too many low-level alerts from different systems lead to key threats being missed.
- False positives – Imprecise endpoint security can flag harmless actions as potential threats.
- Overhead costs – Significant staff time and resources required for hardware, deployment, maintenance, etc.
- Lack of skills – Many organizations lack specialized expertise and best practices for endpoint security.
The most effective solutions focus on automation, integration, and user experience while providing multilayered threat protection.
The future of endpoint security
Endpoint security will continue advancing in several key areas:
- AI and machine learning – Identify new attack patterns and make accurate detections autonomously.
- Cloud-based management – Managed services from the cloud for greater centralization and lower overhead.
- Holistic platforms – Integrated suites providing broader protection beyond just endpoints.
- Greater automation – Automating processes like policy configuration, software deployment, threat response, and more.
- User behavior analytics- Monitor normal behavior patterns to better flag anomalies that may represent insider threats or account compromise.
- IoT and OT security – Expanded capabilities tailored to securing non-traditional devices and environments.
As the number and variety of endpoints continues growing, these innovations will be critical for scalable protection.
Conclusion
Endpoint security is foundational to enterprise cybersecurity. Remote work, BYOD policies, and cloud adoption have extended corporate networks beyond the firewall. This makes securing employee devices imperative to reducing attack surface and safeguarding data. By implementing layered defenses – across antivirus, encryption, access controls, and more – organizations can monitor, control, and harden their myriad endpoints against compromise.
With a surging array of threats and devices, proactive endpoint management provides a high ROI. Careful planning, policy definition, and multilayered technical controls are key to effective implementation. Integrating automation, advanced analytics, and threat intelligence will enable endpoint security to scale across expanding attack surfaces. By securing each endpoint, enterprise security teams can gain visibility and control to proactively combat evolving cyber risks.