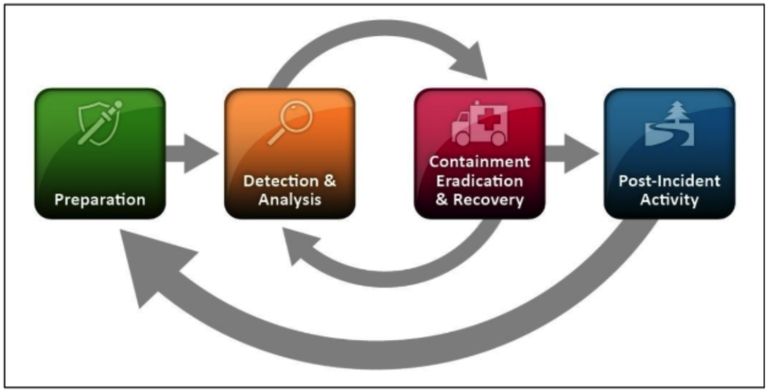
The incident response analysis phase is a critical step in the incident response process. It involves reviewing, assessing and analyzing the details surrounding a security incident to determine its scope, impact and root cause. The key goals of the analysis phase are to understand what happened, how it happened, who or what was responsible, and what vulnerabilities need to be addressed to prevent similar incidents in the future.
When does the analysis phase occur?
The analysis phase typically occurs after the containment phase, when the initial threat has been isolated and neutralized. At this point, the pressure of the attack itself has subsided, allowing the incident response team to take a step back and thoroughly investigate the incident.
The analysis phase involves a detailed examination of forensic evidence, log data, system configurations, and any indicators of compromise discovered during the detection and containment phases. The insights gathered will guide the remediation and recovery efforts that follow.
Why is the analysis phase important?
A thorough analysis phase is critical for several reasons:
- It helps fully understand the scope, impact and root causes of an incident
- It identifies vulnerabilities, gaps and weaknesses that need to be addressed
- It prevents similar incidents from occurring in the future
- It informs improvements to security policies, technologies and processes
- It provides data to calculate the cost of an incident
- It satisfies legal and compliance requirements for reporting and disclosure
Without an in-depth investigation, organizations risk leaving themselves open to repeat attacks, regulatory non-compliance and lawsuits down the line.
What activities take place during analysis?
Key activities commonly performed during the incident response analysis phase include:
Threat intelligence gathering
Researching details about threat actors, tools and techniques to understand their motives, methods and trends. Sources include threat feeds, security bulletins and intelligence shared through trusted communities.
Log analysis
Examining log data from security tools like firewalls, intrusion detection systems and endpoint detection and response platforms to recreate timelines and see what happened when.
Forensic investigation
In-depth probing of compromised systems and accounts using forensic tools to uncover key indicators, extract stolen data, and confirm how the attack unfolded.
Malware analysis
Reverse engineering of any malware samples discovered to understand their capabilities, behaviors and communication patterns.
Vulnerability scanning
Assessment of systems and software for any vulnerabilities or misconfigurations exploited as part of the incident.
Network traffic analysis
Inspection of network traffic logs and full packet captures to uncover command and control activities or data exfiltration.
Containment validation
Re-checking containment measures to confirm that access points, user accounts and compromised systems have been completely isolated and secured.
Impact and damage assessment
Estimation of effects to data, systems, operations and finances, including indirect costs from downtime, recovery and reputational harm.
Root cause determination
Identification of vulnerabilities, gaps or process breakdowns that enabled the incident and recommendations for how to address them.
What data sources are used?
The analysis phase examines data from a number of internal and external sources, including:
- Application and system logs
- Network traffic captures
- Intrusion detection alerts
- Firewall and proxy logs
- File system metadata
- System and configuration data
- Access and authentication logs
- Database audit logs
- Malware samples and signatures
- Recovered forensic artifacts and files
- Open source intelligence
- Threat intelligence feeds
- Information shared by trusted security coordinators and partners
Correlating details from these sources allows analysts to recreate timelines, uncover key indicators, and pinpoint exactly how an attack unfolded.
What tools are used?
Specialized tools used for analysis may include:
- Forensic analysis tools like EnCase and FTK to uncover artifacts on compromised systems
- Packet analysis tools like Wireshark for network traffic analysis
- Log analysis tools like Splunk to correlate details across data sources
- Threat intelligence platforms like MISP for collecting and analyzing IOCs
- Malware analysis tools like Cuckoo Sandbox to observe malware behaviors
- Memory forensics tools like Volatility for analyzing memory images
- Disassemblers and debuggers for reverse engineering malware samples
- Password crackers for analyzing stolen password hashes
- Mobile device forensic tools for inspecting compromised devices
- Database forensics tools for auditing database logs and transactions
Skilled threat hunters and analysts know how to leverage these tools to gain a comprehensive understanding of security incidents.
What outcomes result from the analysis?
The key outcomes of an effective incident response analysis include:
- Complete understanding of the incident’s scope, timeline, impacts and root causes
- List of vulnerabilities and deficiencies requiring remediation
- Identification of at-risk data, accounts, systems and endpoints
- Detailed IOCs, adversary TTPs and other threat intelligence
- Estimated costs and damages from incident
- Prioritized recommendations for enhancing defenses and policies
- Lessons learned, follow-up actions and procedural improvements
- Updated reporting for leadership, customers, partners and authorities
Documenting these outcomes is critical, as the analysis phase feeds into the processes of remediation, recovery planning and future risk reduction.
How long should the analysis phase last?
The duration of the analysis phase can vary significantly depending on the nature and complexity of the incident. Smaller incidents may only require a few hours or days of analysis, while major breaches can take several weeks or longer to fully investigate.
As a general guideline, analysis should continue until all key questions have been answered, the scope is confirmed, root causes are determined, and actionable recommendations have been provided. Prematurely ending analysis risks overlooking vulnerabilities or threat intelligence that could fuel future incidents.
That said, analysis should not drag on indefinitely. Providing leadership and stakeholders with regular updates and concise written reports helps keep the process aligned to business needs.
Who is involved in analysis?
While IT and security teams lead the analysis, multiple groups provide input to help paint a comprehensive picture. Stakeholders in the analysis phase may include:
- Incident response team – Security analysts, threat hunters, forensic investigators
- IT operations – Systems and network administrators
- Security operations center – Monitoring, log analysis
- Application and software development teams
- Threat intelligence analysts
- Legal counsel and compliance officers
- Public relations and communications – For reputational impact
- Human resources – When insiders are involved
- Executive leadership
Each group contributes expertise and perspective that improves the depth of analysis.
How is analysis documented and reported?
Thorough documentation is essential for tracking the analysis phase. Key reporting documents may include:
- Timeline of incident events – A detailed chronological log of when key events occurred before, during and after the incident.
- Incident summary report – A high-level overview of the incident for leadership and external stakeholders.
- Technical analysis report – In-depth look at technical details for IT and security teams.
- Forensic analysis report – Findings from any forensic investigations performed.
- IOC and threat intelligence briefing – Summary of threat actor tactics and relevant IOCs.
- Vulnerability analysis – Review of gaps and weaknesses enabling the incident.
- Recommendations report – Prioritized next steps for enhancing security and response.
Reports help transfer knowledge, guide next steps, and satisfy compliance requirements for evidence preservation and disclosure. They also provide data to calculate costs, damages and risk profiles associated with incidents.
What mistakes happen during analysis?
Common missteps that undermine the incident response analysis phase include:
- Poor preservation of evidence, compromising forensic investigations
- Limited visibility into systems, networks and endpoints
- Focusing only on containing the attack, not investigating root causes
- Failure to leverage threat intelligence and IOCs
- Stopping analysis prematurely before determining scope and impacts
- Neglecting to identify and remediate vulnerabilities enabling the incident
- Failing to document analysis activities, findings and recommendations
- Not involving stakeholders to get all relevant perspectives
- Lack of skilled analysts and proper tools to support investigations
Organizations should invest in processes, resources and training to avoid these pitfalls and maximize the effectiveness of incident response analysis efforts.
How can organizations improve their analysis phase?
Key steps organizations can take to improve incident response analysis capabilities include:
- Developing formal incident analysis processes and playbooks
- Assembling a skilled team of security analysts, threat hunters and forensics specialists
- Providing analysts with specialized investigation tools and training
- Collecting and retaining comprehensive log and data sources
- Establishing partnerships to leverage threat intelligence
- Designating staff to coordinate analysis efforts across departments
- Creating incident analysis reporting templates
- Conducting tabletop exercises to practice analysis and unearth gaps
- Enforcing evidence handling procedures that support forensics
- Allocating adequate time for thorough analysis, even for smaller incidents
- Continuously improving based on lessons learned from past response efforts
With robust threat analysis capabilities, organizations can respond more effectively to incidents and make data-driven decisions about enhancing their defenses against future attacks.
Conclusion
Performing comprehensive threat analysis is a core component of effective incident response. By thoroughly investigating what happened, how it happened and why, organizations gain actionable insights to guide remediation efforts and bolster overall security posture. A detailed analysis phase examines forensic artifacts, system data, network activity logs, threat intelligence and more to determine the full scope and root causes of an incident. While challenging, investing in skilled personnel, proven processes and the right technologies pays dividends by driving more informed, measured responses to security incidents.