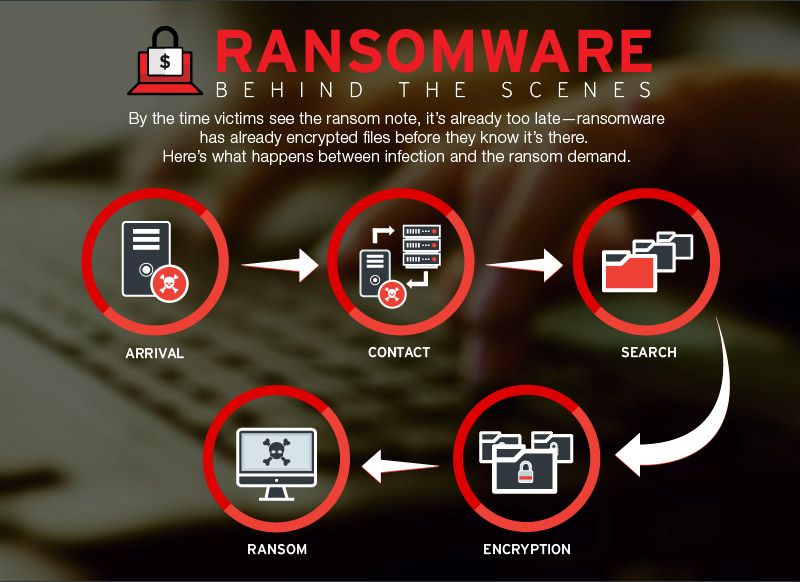
Ransomware is a form of malicious software that encrypts files on a device and demands payment in order to decrypt them. If your device becomes infected with ransomware, there are a few key things that will likely occur.
Your Files Will Be Encrypted
The primary purpose of ransomware is to encrypt files on your device so that you can no longer access them. Encryption converts files into an unreadable format using a complex algorithm. Ransomware encrypts files slowly and discretely in the background once it infects a device. You may not even realize your files have been encrypted until you try to open them one day and find that you can’t. Ransomware can encrypt a wide variety of file types including documents, photos, videos, and more.
You’ll Get a Ransom Demand
Once your files are encrypted, the ransomware will display a message informing you of what happened and demanding payment to get your files back. This message will contain instructions on how to pay the ransom, usually requesting payment in cryptocurrency such as Bitcoin. The ransom amount can vary dramatically, from several hundreds to thousands of dollars. The message will often warn that if you don’t pay the ransom within a certain timeframe, the decryption key will be deleted and your files will be lost forever.
Some Functions May Be Disabled
In addition to encrypting your files, some ransomware strains will also try to prevent you from using certain functions on your device intended to help remove infections. For example, ransomware may disable System Restore functionality, Safe Mode, Windows Update, firewalls, security software, Command Prompt access, etc. This makes it much more difficult to stop and remove the ransomware from your device.
Your Personal Files Will Be Targeted
Ransomware aims to encrypt files that are most valuable to you personally. So it will target document files, photos, videos, databases, and other file types specific to your usage of your device. Generic system files that are easily replaceable are usually not encrypted. This targeting of your irreplaceable personal files is intended to compel you to pay the ransom to get them back.
Professional Recovery May Be an Option
If you are unwilling to pay the ransom, it is sometimes possible to recover encrypted files by using professional decryption tools. Security companies like Kaspersky and McAfee maintain databases of ransomware strains and have tools that can decrypt some of them by cracking their algorithms. However, this decryption capability depends entirely on the particular type of ransomware involved, and only works for some strains, so there are no guarantees. You often need to identify which ransomware strain infected your device to determine if decryption is viable.
New Infections May Occur
Paying the ransom does not guarantee the ransomware will be removed from your device. The ransomware may install additional malicious components during the infection process. So even if you pay up and get your files decrypted, these other undetected infections could still be present. New strains of ransomware could then infect your device again in the future. Thorough scanning and cleaning of the device by security software is necessary.
Complete System Reinstallation May Be Necessary
If the ransomware is sophisticated and you cannot decrypt your files or completely remove the infection, reinstalling your operating system may be the only sure way to disinfect your device. Back up any remaining personal files you need, then wipe the infected system drive and reinstall the OS from scratch. This scorched earth approach is sometimes the only way to ensure complete removal of the ransomware remnants.
Data May Still Be Recoverable
Even though the encrypted files on your system are inaccessible, the raw underlying data may still be intact. Using advanced data recovery tools, it is sometimes possible to reconstruct portions of encrypted files by scanning the system drive and extracting data fragments. The recovered data remains scrambled, but specialists can sometimes partially reconstruct files using this technique. However, this requires an extremely high level of technical expertise.
Backups Are Your Best Protection
The most effective way to protect yourself from permanent data loss due to ransomware is to maintain recent backups of your files on disconnected external media. If your device gets infected, you can simply restore your data from backup rather than paying the ransom. Backup platforms like cloud storage, external hard drives, NAS devices, and offline backups provide protection against file encryption. Just ensure backups are disconnected from your system to prevent encryption.
How Ransomware Initially Infects Your System
Now that you know what generally happens after a ransomware attack, how does the initial infection occur in the first place? Here are some of the most common infection vectors through which ransomware sneakily establishes itself on a system:
- Phishing emails with infected attachments or links to malicious sites
- Infected application downloads from unofficial sources
- Drive-by downloads from compromised websites in browsers
- Remote Desktop Protocol (RDP) brute force attacks on exposed systems
- Software vulnerabilities that enable remote code execution
- Infected external devices like USB drives connected to the system
Once on a system, ransomware uses various techniques to hide its presence and evade detection as it encrypts files in the background. Advanced strains exploit privileges and security holes to spread across networks.
How To Prevent Ransomware Infections
Practicing good security hygiene is key to preventing ransomware attacks. Here are some important tips:
- Keep all software up-to-date with the latest patches
- Avoid enabling RDP unless absolutely needed
- Install reputable antivirus and anti-malware tools
- Be extremely cautious of unsolicited emails and attachments
- Only download programs from official trusted sources
- Immediately back up any suspicious files before scanning
- Disable macros in Microsoft Office documents
- Don’t browse websites carelessly or click suspicious ads/popups
- Use ad blockers and anti-exploit tools in your browser
Following best practices for security and being vigilant about suspicious system activity goes a long way in preventing ransomware from ever having a chance to infiltrate your device and encrypt your important files.
What To Do If Infected With Ransomware
If you discover your device has been infected with ransomware, here are the steps you should take:
- Disconnect from networks/internet immediately
- Backup any files that are still accessible
- Identify the ransomware strain if possible
- Use security tools to contain and remove the infection
- Determine if decryption tools are available
- Wipe system fully and restore from clean backups
- Learn from the experience and improve security
Staying calm but acting quickly can help minimize the damage from a ransomware attack. The most important things are preventing its spread across networks, containing the infection, removing it completely, and restoring your data from clean backups.
Should You Pay the Ransom?
This is always a difficult decision for victims of ransomware. There are several factors to consider when deciding if paying the ransom is appropriate:
| Paying Ransom | Not Paying Ransom |
|---|---|
| May allow you to quickly recover encrypted files if decryption key works | Does not guarantee you will get files back even if you pay |
| Only option if backups are not available and files are invaluable | Rewards and incentivizes criminals to continue attacks |
| May be only realistic option depending on type of ransomware | May result in repeat infections if ransomware is not fully removed |
| Can be done if you can afford the ransom amount | Loss of files may not critically impact operations or be manageable |
There are merits to both options. In general, paying the ransom should be an absolute last resort after all other options have been exhausted. The FBI recommends not paying ransoms.
Conclusion
Ransomware attacks can have devastating effects by encrypting irreplaceable files and holding them hostage for payment. If your device is infected, your files will be encrypted, some functions may be disabled, and you’ll get a ransom demand for decryption. Professional recovery and complete system wipes are two options if you don’t pay. Ultimately, the best protection against ransomware is comprehensive backups, security best practices, and cyber vigilance.