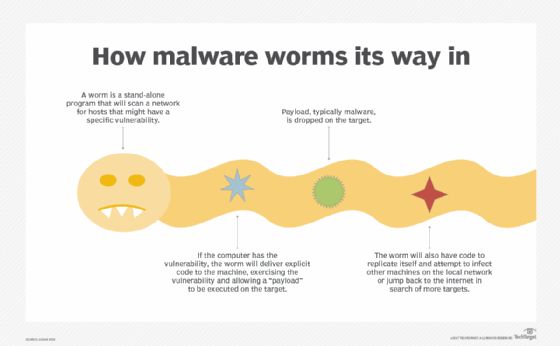
A computer worm is a type of malicious software program that spreads copies of itself from computer to computer without the need for human interaction. Worms are self-replicating programs that take advantage of file-transport or information-transport features on computer networks. They differ from viruses in that viruses require the spreading of an infected host file, whereas worms are stand-alone software and do not require a host program or human help to propagate.
How Do Computer Worms Spread?
Computer worms spread by exploiting vulnerabilities in operating systems or application programs. They take advantage of file-transport or information-transport features enabled on networked computers to spread copies of themselves to other systems. This allows them to replicate without any human interaction or assistance.
Some of the common methods computer worms use to spread include:
- Scanning for vulnerable systems: Worms scan networks for systems with vulnerabilities they can exploit to break in and infect.
- Using open network shares and drives: Worms access open network shares and drives to copy themselves to new systems.
- Email attachments: Worms can send copies of themselves via email as attachments which recipients then open, allowing the worm to execute and spread.
- Instant messaging: Worms can use IM clients and contacts lists to send copies of themselves to new systems.
- Social engineering: Worms can trick users into opening attachments or clicking on links to execute their code.
- Exploiting software vulnerabilities: Worms exploit security holes in software like buffer overflows to break in and infect systems.
By using these methods to self-propagate over networks, worms can spread quickly, infecting large numbers of computer systems without needing assistance after the initial infection. This allows them to replicate automatically.
Famous Computer Worm Outbreaks
Some infamous computer worms that were able to propagate widely without user interaction include:
Morris Worm – 1988
The Morris worm was one of the very first Internet worms, created by Cornell graduate student Robert Morris in 1988. It exploited weaknesses in Unix sendmail, finger daemon and rsh/rexec applications to spread. At the time, it managed to infect around 10% of all computers connected to the early Internet within just a day. This massive and disruptive spread highlighted the emerging threat worms could pose to the growing interconnectedness enabled by the Internet.
Code Red – 2001
The Code Red worm exploited a vulnerability in Microsoft’s IIS web servers to automatically spread itself. It was designed to launch a denial of service attack on the White House website, but also ended up infecting over 359,000 other hosts globally in less than 14 hours. It caused an estimated $2.6 billion in damages.
Conficker – 2008
First detected in 2008, the Conficker worm infected millions of Microsoft Windows PCs globally by exploiting a network file sharing vulnerability. It could also spread via USB drives and by brute forcing password-protected network shares. Conficker formed botnets by communicating with its infected hosts, but its actual intended purpose was never fully confirmed.
Stuxnet – 2010
The Stuxnet worm was a highly targeted cyberweapon, designed to spread via infected USB drives and local networks. It targeted Siemens industrial control systems and was used to damage uranium enrichment centrifuges in Iran’s nuclear program. Stuxnet showed how worm capabilities could enable sophisticated cyberattacks on critical infrastructure.
Why Are Worms Dangerous?
Worms can be extremely disruptive and dangerous due to their ability to self-replicate rapidly across networks without user interaction. Some major concerns posed by worms include:
- Rapid spreading – Worms can spread to large numbers of systems very quickly by automatically propagating, allowing them to infect entire networks or even the Internet globally within hours or days.
- Consumption of bandwidth – As worms replicate and communicate between infected hosts, their network communications can consume large amounts of bandwidth, slowing or crashing infected networks.
- System slowdowns/crashes – Worm activities like scanning and replication can overload systems with processor usage and traffic, causing slowdowns or crashes.
- Loss of data – Some worms can delete, encrypt or damage data on infected systems as part of their payload.
- Botnets – Worms can install backdoors to form botnets, allowing remote takeover of infected machines for criminal uses.
These impacts make worms a favored tool for cybercriminals and hackers. Worm outbreaks can cripple businesses, governments and critical infrastructure through traffic overloads, systems failures, and loss of sensitive data. Notable worm attacks like Conficker and Stuxnet have demonstrated their highly disruptive potential.
Defending Against Computer Worms
Defending against computer worms requires layers of security measures, given their ability to spread unaided once they gain an initial foothold. Key protections include:
- Patching and updating software to eliminate vulnerabilities worms can exploit to spread.
- Using firewalls and IPS systems to block malicious traffic and detect worm activity.
- Be careful with attachments and links in emails to avoid infection.
- Disable unnecessary services and ports that worms can take advantage of.
- Use security solutions like antivirus to detect, block and remove worm infections.
- Educate users on risks and best practices around worms.
- Segment and monitor networks to limit the spread of worms.
- Test and simulate worm scenarios to assess readiness.
With strong technical defenses combined with user awareness training, organizations can reduce their risk of disruptive worm outbreaks. However, the ongoing evolution of new worms like Nimda, Sasser and Zotob demonstrates the persistence of this threat. Sustained vigilance is key to limiting potential worm infestations before they result in data breaches or network crashes.
The Rise of “Good” Worms
Interestingly, while most worms are developed with malicious intent, some security researchers have explored concepts around “good” worms. These would be designed with beneficial aims like:
- Patching vulnerabilities in systems to prevent exploitation by malicious worms.
- Removing infections by harmful worms or viruses.
- Inoculating systems against code injection attacks.
However, such “white hat” worms would face significant legal and ethical challenges around replicating on systems without consent. They could also potentially spread out of control themselves. But the possibility of fighting fire with fire by using worm-like methods for defense remains an intriguing idea for some security experts.
Conclusion
In summary, computer worms are dangerous not because they need to be activated by a user, but precisely because they do not – they can spread unaided once released. This gives them enormous disruptive potential through rapid self-replication across networks. While technical controls and user education are key to limiting their spread, worm threats will likely persist as long as systems are networked and have vulnerabilities that can be exploited for self-propagation. However, their inherently autonomous nature also presents certain opportunities if similar capabilities can be harnessed beneficially. Understanding the worm model of self-sufficient propagation remains vital for security in today’s interconnected world.