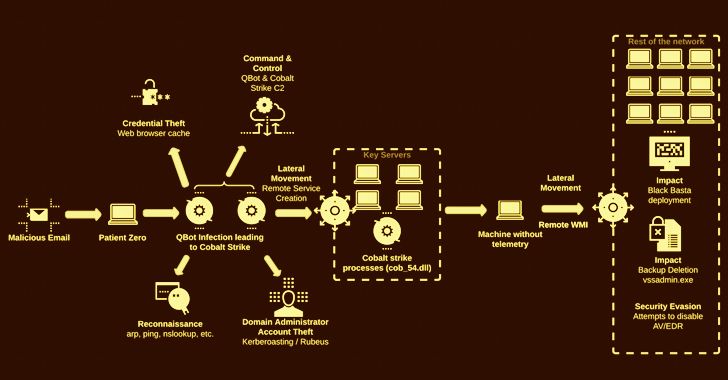
Black basta is a type of malware that can infect Android devices and take control of them. As with any type of malware, black basta has certain vulnerabilities that can be exploited to detect or stop an infection. In this article, we will explore the key vulnerabilities of black basta and how security experts and Android users can leverage them for protection.
How Black Basta Infects Devices
Black basta is spread through infected apps, which a user downloads and installs on their Android device. These infected apps appear legitimate but contain hidden malicious code that gets triggered once the app is launched on the device. Here are some key ways black basta infects devices:
- Get uploaded to third-party app stores that have poor security screening. Users download these infected apps thinking they are legitimate.
- Mask as popular Android apps and get distributed through phishing links or text messages. Users click on links or attachments that seem legitimate but actually download the malware.
- Come pre-installed on certain Android devices, embedded deep in the firmware. This happens through unethical manufacturer practices.
Once installed on a device, black basta begins communicating with a remote command and control server operated by the attackers. It can now execute a wide range of malicious activities through commands sent by the C&C server.
Key Vulnerabilities of Black Basta
Like all malware families, black basta has certain weaknesses in its code and infection methodology that can be leveraged to detect its presence or disrupt its working. Here are some of its key vulnerabilities:
Requires Continuous Internet Connectivity
Black basta needs to maintain constant communication with its C&C server to function properly. It cannot operate autonomously on the infected device beyond initial installation. Without internet connectivity, the C&C server cannot send new commands to the infected device.
This reliance on internet connectivity can be disrupted through the following measures:
- Switching to airplane mode temporarily isolates the device from external communication.
- Disabling Wi-Fi and mobile data has the same effect as airplane mode.
- Usage of firewalls can block black basta’s outbound connections.
- Changing internet service providers disrupts the hardwired IP addresses used by black basta.
Prone to Outages of C&C Infrastructure
Black basta fully depends on its C&C server infrastructure to control infected devices. Any outages or takedowns of these servers immediately paralyze the malware. C&C servers often switch IP addresses and domains to avoid detection. But they can still be identified through patterns of communication and taken down.
Has Predictable Network Traffic Patterns
The network traffic generated by black basta displays certain repetitive and predictable patterns that can be used to detect its presence. These include:
- Frequent outgoing connections on ports 80, 443, or 53 to a similar set of IP addresses.
- Heavy domain name resolution traffic for domains associated with black basta C&C servers.
- Repetitive connections at fixed intervals to download configuration data or exfiltrate stolen user data.
Network security tools can be configured to alert administrators about such traffic anomalies indicative of a black basta infection on the network.
Leaves Forensic Footprints
Black basta does make changes to an infected Android device that can be forensically spotted later on for investigation purposes. These footprints would include:
- Installation of non-standard SSL certificates allowing man-in-the-middle decryption of secure traffic.
- Changes to browser settings and permissions to allow interception of web sessions.
- Alterations to the OS Hosts file, proxies, DNS settings to divert traffic through black basta routes.
- Any unknown apps installed on the device that may be associated with black basta.
Through forensic analysis, these indicators can conclusively establish past or current black basta infection on a device.
Contains Identifiable Code Artifacts
The core code of black basta does contain certain identifiable artifacts such as:
- IP addresses of its C&C servers hardwired into configuration files.
- Distinct packet signatures of network traffic it generates.
- Unique encryption keys it uses to obfuscate C&C communications.
- Code strings, modules, libraries that are reused across variants.
- Similar obfuscation techniques across different samples.
By analyzing these coding artifacts, security researchers can build detection signatures for black basta. Some variants may have minor code modifications but retain enough common artifacts to be detectable through signature-based scanners.
Behavioral Analysis Techniques
Analyzing the behavior of black basta during execution also reveals common infection patterns that can be used for detection. Some examples of behavioral analysis approaches include:
Sandbox Emulation
Black basta samples can be run in a contained virtualized environment to observe their execution flow. The malware is tricked into activating while security tools record its every action. This reveals details like network connections attempted, files created, system changes made, processes activated, etc. These IOCs can then be converted into detection rules.
Debugging
Debuggers like IDA Pro allow stepping through black basta’s code one instruction at a time during execution. Its runtime decryption routines, data exfiltration, and other behaviors can be monitored in real-time. Code analysis can reveal inner workings of different malware variants.
Network Traffic Analysis
As mentioned earlier, black basta generates distinct network traffic patterns as it communicates with C&C servers. Analyzing this traffic using tools like Wireshark helps identify patterns for detection rules. Things like IP addresses, domain names, frequency, packet sizes, etc. offer useful insights.
Some other examples of dynamic analysis techniques used by researchers include binary instrumentation, code injection, and memory forensics. When performed skillfully, they can reveal many useful insights into black basta’s workings.
Vulnerabilities of Encrypted Communications
Black basta uses a range of encryption techniques to obfuscate its C&C communications and internal binary code/data. However, vulnerabilities exist in the implementation of these encryption schemes that can still enable detection.
Weak Encryption Algorithms
Some black basta variants use symmetric encryption algorithms with a small key size or outdated modes of operation. These can be cracked through brute force much more easily. Weak RSA encryption is also prone to mathematical attacks for decryption.
Reused Encryption Keys
At times black basta reuses the same encryption keys across multiple infections. By obtaining the key from one infected device, security researchers can decrypt samples found on other victims too. This provides a wealth of intel into the malware’s inner workings.
Hardcoded Encryption Keys
Rather than generating random keys, some black basta variants hardcode the encryption keys inside their binary. Through reverse engineering, these keys can be extracted and then reused for decryption.
Metadata & Traces
Even when communication is encrypted, metadata about the traffic remains unencrypted. Things like timestamps, packet sizes, destination info, traffic volumes etc. Still, provide useful clues about C&C communications. Residual traces in system memory can also reveal encryption keys.
Injection Techniques
Security researchers often use special techniques to inject their own code into black basta malware. This allows better monitoring of its actions or even disruption of its execution. Some examples include:
DLL Injection
A custom DLL with logging, analytics, or blocking logic can be injected into black basta’s execution context. This DLL gets loaded by the malware just like its internal DLLs and can monitor or interfere with its workings.
Code Injection
Small code snippets can be forcibly injected into the memory space of the black basta process to add hooks for analysis or to disable specific functions.
Memory Editing
The values of specific memory addresses critical to black basta’s functioning can be changed to manipulate execution flow or decryption keys.
API Hooking
APIs used by black basta to perform tasks like encryption, network transfer, file activities etc. can be hooked to monitor or block those operations.
When performed expertly, these injection techniques provide deep insight into the malware while also disabling its malicious capabilities as needed.
Machine Learning Detection
Given the vast volumes of new android malware samples emerging these days, traditional signature-based detection proves inadequate. Modern AI/ML techniques are better suited for detecting variants of black basta based on its underlying traits.
Large datasets of black basta samples are used to train machine learning models to recognize its patterns. Some approaches include:
Static Analysis
Features like opcodes, metadata, permissions, API calls etc. are extracted from black basta samples to train ML classifiers like logistic regression, random forests, neural networks, etc. They learn associations between these static features and black basta code.
Dynamic Analysis
Models are trained on features extracted from dynamic execution of samples in sandboxes. This includes behavior like file/registry operations, network activity, memory access, system calls etc. RNNs, CNNs perform well in classifying malware based on dynamic traces.
Hybrid Analysis
For best results, features from both static and dynamic analysis are combined to train deep neural networks capable of reliably detecting black basta variants. This provides resilience against code obfuscation techniques.
Deep learning has emerged as a robust way to detect evolving strains of android malware like black basta. However, adversarial ML remains an arms race, as black basta developers may try crafting samples that can evade ML classifiers.
User-Level Detection
For Android users, it is essential to watch for early warning signs of a black basta infection on their device. Some user-level symptoms to watch out for include:
- Unknown apps installed on your device that you didn’t download.
- Apps crashing unexpectedly or freezing.
- Unusual battery drain.
- Sluggish device performance.
- High data usage when internet activity seems low.
- Unknown outgoing connections in firewall or data usage logs.
- Unusual pop-up ads.
If multiple such symptoms appear, it likely indicates black basta presence. Some steps users can take include:
- Scan device with a reputed anti-virus app to detect malware.
- Factory reset the device if the infection seems deep.
- Avoid sideloading random apps from unverified sources.
- Monitor which apps use data/battery intensively.
- Examine app permissions carefully during installs.
Staying alert and being cautious about app installs is the best way Android users can avoid black basta infections.
Conclusion
In summary, here are some of the key vulnerabilities of the black basta malware that can be leveraged to detect and disrupt infections:
- Dependence on C&C infrastructure.
- Predictable network activity patterns.
- Code artifacts and patterns.
- Behavioral analysis through sandboxes and debuggers.
- Weaknesses in encryption implementation.
- Susceptibility to code injection techniques.
- Detectability through ML techniques.
- User-visible symptoms of infection.
By combining these strategies, security analysts can build multi-layered defenses against black basta. However, android malware continues to evolve rapidly. Users and organizations must remain vigilant and constantly adapt detection approaches to identify new black basta variants. The cybersecurity arms race against malicious threat actors is a continuous process requiring ongoing innovation.