Threat intelligence providers are companies that collect, analyze, and provide data on cyber threats to help organizations defend against attacks. Threat intelligence can come from a variety of sources and be tailored to specific industries, geographic regions, or types of threats.
What is threat intelligence?
Threat intelligence refers to analyzed information about potential or current attacks that can impact an organization. This includes data on threat actors, their tactics, techniques, and procedures (TTPs), compromised credentials, malicious IP addresses, phishing emails, malware, and other indicators of compromise (IOCs).
Threat intelligence helps security teams:
- Identify attacks earlier in the cyber kill chain
- Prioritize responses based on context around the threats
- Block known threats before damage is done
- Determine if an attack is targeted or part of a broader campaign
High-quality threat intelligence is relevant, timely, and actionable, enabling faster detection and an improved security posture.
What do threat intelligence providers offer?
Threat intelligence providers collect threat data from a wide range of sources, analyze it, and deliver customized intelligence to clients. Core services offered include:
- Threat feeds – Regular updates on new threats, including IP addresses, domains, malware hashes, phishing emails, and other IOCs.
- Threat reports – Detailed reports on threat groups, new TTPs, or emerging campaigns.
- Adversary profiles – Deep analysis of specific threat actor groups and how they operate.
- Strategic intelligence – Insights into threat trends by industry, region, and attack type.
- Threat monitoring – Ongoing monitoring of threats relevant to the client’s industry and interests.
- Threat portals – Dashboards and platforms to access and analyze intelligence.
This intelligence powers defensive tools like firewalls, SIEMs, endpoint detection and response (EDR), and intrusion detection systems (IDS). It also informs threat hunting, incident response, awareness training, and security strategies.
What are the key benefits of threat intelligence?
Using threat intelligence provides multiple advantages, including:
- Faster detection – Threat intel provides IOCs and TTPs that help security teams identify threats early.
- Improved prioritization – Context around threats helps teams focus on the most urgent and relevant attacks.
- Proactive blocking – Intelligence is used to block known bad IP addresses, URLs, malware files, phishing emails.
- Stronger defenses – Intel informs which defenses to use, their configuration, and rules.
- Targeted hunting – Teams can hunt for specific threats in their environment based on threat intelligence.
- Better collaboration – Sharing intel helps security teams coordinate defenses across organizational boundaries.
Ultimately, this reduces risk, contains threats faster, and helps conserve security resources.
What are the sources of threat intelligence?
Threat intelligence providers leverage both external and internal sources to build their offerings. Common external sources include:
- Open source intelligence (OSINT) – Public sources like blogs, forums, code repositories, social media, and news articles provide threat insights.
- Dark web – Providers monitor dark web sites and forums for threat actor communications and stolen data sales.
- Telemetry from security tools – Anonymized global telemetry provides data on real attacks seen in the wild.
- Partnerships with industry – Collaborating with IT vendors, service providers, CERTs, and industry groups.
- Collaboration with law enforcement – Some work with agencies like FBI, NSA, and Interpol to incorporate threat information.
- Underground contacts – Certain providers cultivate anonymous contacts in the cybercriminal underground.
Internal sources can include:
- Global sensor networks – Sensors set up by providers detect and analyze malware, phishing sites, C2 traffic, and other threats.
- Honeypots – Controlled systems are used to attract attackers and study TTPs.
- Botnet monitoring – Infiltrating and tracking botnet activity provides intelligence on attacks.
- Malware analysis – Reverse engineering malware samples reveals capabilities and coding similarities.
- Threat research teams – Expert researchers review data and threats to create intelligence reports.
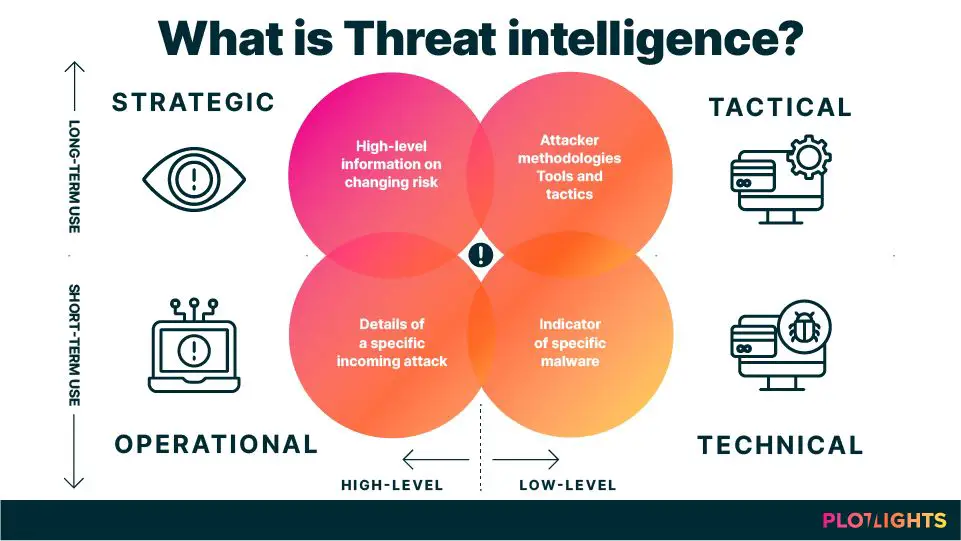
What are the different types of threat intelligence?
Threat intelligence is often categorized into three levels:
- Strategic – High-level intelligence focused on threat trends, key actors, geopolitics, and emerging technologies that may impact security.
- Operational – Intelligence on threat actor TTPs, ongoing campaigns, malware analysis, phishing, vulnerabilities, and compromised credentials that can support security operations.
- Tactical – Very specific technical indicators like file hashes, IP addresses, domains, and email subjects that can be used to detect threats and block attacks.
Providers may focus on one or more levels depending on their sources and capabilities. Many also tailor intelligence around industries like finance, retail, healthcare, and more.
How do threat intelligence platforms work?
Threat intelligence platforms aggregate, analyze, and contextualize threat data into actionable intelligence. Core components include:
- Collection – Gathering threat data from multiple internal and external sources via APIs, feeds, scraping, partnerships.
- Processing – Filtering, normalizing, deduplicating, and enriching raw data into standardized indicators.
- Analysis – Linking related indicators, establishing patterns, attributing campaigns to threat groups, identifying targets.
- Production – Compiling intelligence into machine-readable formats like STIX/TAXII as well as reports, briefings, dashboards.
- Dissemination – Distributing intelligence to defenses, teams, and stakeholders based on their requirements.
- Integration – APIs and tools to enable intelligence consumption across security infrastructure like SIEMs, firewalls, proxies.
- Automation – Workflows to automatically update defenses with new IOCs and trigger responses.
By connecting to a provider’s intelligence platform, organizations can operationalize relevant threat data across their security stack.
What are some top threat intelligence providers?
Some of the leading commercial threat intelligence providers include:
| Provider | Description |
|---|---|
| Recorded Future | Wide-ranging strategic and tactical threat intelligence fueled by natural language processing and machine learning. |
| ThreatQuotient | Threat intelligence platform with extensive enrichment and analytics capabilities. |
| Anomali | Integrates threat intel feeds, SIEM data, and ISAC reports into customized products. |
| LookingGlass Cyber | Extensive intelligence on cyber threats, state actors, compromised assets, and supply chain risks. |
| Flashpoint | Specialized provider leveraging unique data sources like forums, dark web, and underground contacts. |
| Digital Shadows | Focuses on externally facing digital assets, brand threats, data leaks. |
| AlienVault | Combines open source intelligence with OT and IoT-specific threat detection. |
| CISCO Talos | Provides threat intelligence based on telemetry data from CISCO security products. |
| Splunk | Leverages SIEM data to generate analytics-driven threat intelligence. |
There are also industry-specific providers focused on sectors like finance, energy, and healthcare. Some large enterprises build internal threat intelligence teams and capabilities as well.
What are the benefits of commercial threat intelligence?
Compared to freely available threat intel, commercial providers offer:
- Breadth and depth of intelligence – Access to vast threat data from diverse authoritative sources, along with expertise to enrich and analyze it.
- Speed – Rapid discovery and analysis of emerging threats and campaigns.
- Relevance – Intelligence can be tailored to specific regions, industries, technologies, and internal risks.
- Accuracy – Specialized tools and human analysis for high fidelity intelligence with low false positives.
- Coverage – Intelligence on a wide spectrum of threats including cybercrime, hacktivism, state-sponsored attacks, and insider threats.
- Strategy – Insights into the threat landscape to inform security roadmaps and leadership decisions.
- Workload reduction – No need to build internal capabilities for global threat monitoring and analysis.
For resource-constrained security teams, commercial threat intelligence can provide an essential force multiplier effect.
What questions should you ask threat intelligence providers?
When evaluating threat intelligence providers, key questions to ask include:
- What specific data sources do you use? How are they validated and updated?
- How much of the analysis is automated vs manual review? What are your analysis methods?
- Do you tailor intelligence to specific verticals and geographies?
- What partners or sub-contractors are part of your source network?
- What intelligence formats (STIX, CSV, PDF reports) do you support?
- How frequently are indicators updated? What is the SLA for new threats?
- How do you reduce false positives and inaccurate data?
- What platforms and tools are available to consume your intelligence?
- Do you integrate with other security products we use?
- Can your intelligence automatically update our defenses like firewalls?
- What level of support do you provide?
- What is your experience in our industry?
Understanding their capabilities, specialities, and limitations is key to choosing the right provider.
How should you integrate and consume threat intelligence?
To maximize value from threat intelligence, organizations should:
- Establish dedicated TIP teams – A threat intelligence program with staff to manage providers, integrate intelligence, measure efficacy.
- Feed key security systems – Route indicators to security tools like SIEMs, EDR, firewalls, email/web gateways.
- Automate dissemination – Use APIs and workflows to automatically update defenses rather than manual processes.
- Train staff – Educate security teams on leveraging threat intelligence in their workflows for detection, response.
- Provide strategic context – Use reports/briefings to inform executives, board members on threats relevant to business.
- Enable sharing – Share intelligence internally and externally with trusted partners for greater collective security.
- Measure impact – Quantify improvements in metrics like detection time, containment time, blocked threats.
Threat intelligence must become an integral part of security operations and tools to realize its full potential.
What are common challenges with threat intelligence?
Some frequent challenges faced by organizations include:
- Data overload – Too many IOCs and excessive threat alerts can overwhelm security teams.
- Limited sharing – Silos between network/endpoint/application teams prevents maximizing intel.
- Lack of context – IOCs without context on campaigns lead to false positives and blind spots.
- Measuring ROI – Difficulty determining effectiveness and justifying threat intel investments.
- Feed inconsistencies – Varying data formats, qualification, and update frequencies across feeds.
- Integration issues – Technical challenges connecting new data sources and tools.
- Skill gaps – Lack of analysts to assess intelligence and act on findings.
- Dependence on manual processes – Tedious manual work to disseminate intelligence across defenses.
A thoughtful approach is required to maximize the advantages while navigating the pitfalls.
Conclusion
Threat intelligence provides invaluable insights that can significantly improve security defenses and monitoring. By informing decisions and systems with relevant, timely intelligence on the evolving threat landscape, organizations can detect and disrupt attacks sooner.
However, realizing the full potential requires evaluating providers carefully based on your needs, integrating intelligence into workflows through automation, developing skills to leverage it, and tracking impact on metrics. With the right implementation, threat intelligence can take security programs to the next level.