Encryption is the process of encoding information in such a way that only authorized parties can access it. When files on your computer are encrypted, it typically means that someone has encrypted them in order to restrict access. There are a few common scenarios where you may encounter encrypted files:
You enabled encryption yourself
If you turned on encryption for a specific folder or drive on your own computer, you did so to prevent unauthorized access. For example, you may have encrypted a folder containing financial documents or other sensitive information. In this case, you should have the encryption key required to decrypt the files.
Your company uses encryption
Many organizations use encryption to protect company data. For example, your files may be encrypted if you access them remotely via a VPN. The IT department manages the encryption in this scenario. If you can’t access encrypted work files, you’ll need to contact them.
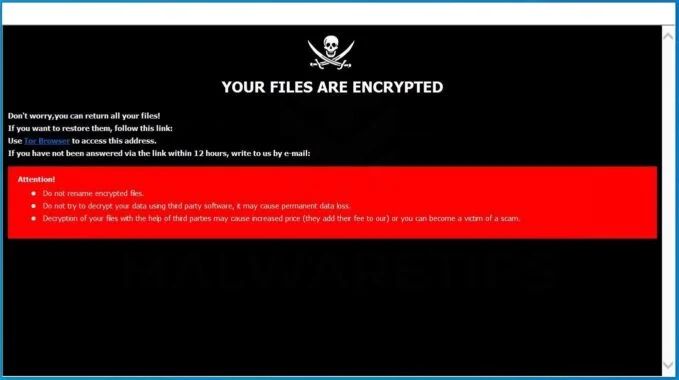
Ransomware attacked your computer
One of the most common ways files become unexpectedly encrypted is due to malware like ransomware. Ransomware encrypts files on infected devices and demands payment to decrypt them. Cybercriminals distribute ransomware through phishing emails, infected websites, and other methods. If you don’t have backups of your files, you may have to pay the ransom to get them back.
An encryption utility encrypted everything
Some encryption tools automatically encrypt all files on a device or drive. For example, BitLocker on Windows can implement full disk encryption. If you enabled this type of utility and forgot the password, you won’t be able to access any files.
How can you tell if your files are encrypted?
There are a few signs that indicate your files have been encrypted:
- You cannot open files and get an error message about encryption
- File names have been changed to random characters
- Folders containing encrypted files are marked with a lock icon
- A text file with ransom instructions has been added to your desktop or folders
If you see these indicators, your files have likely been encrypted. But how do you go about regaining access to them?
Get the encryption key or password
If you encrypted the files yourself or your company manages the encryption, you’ll need to retrieve the encryption key or password. Typically, a certificate or key file is required along with a password to decrypt files. Your IT department may need to provide you with this information if it’s a work device.
Restore from backups
If your files were encrypted by ransomware, restoring from backups is the best way to regain access. As long as you have unencrypted backups stored offline, you can restore your files after removing the ransomware. This eliminates the need to pay the ransom.
Use third-party decryption tools
For some ransomware strains, security researchers are able to crack the encryption. Third-party decryption tools are sometimes released that allow victims to decrypt their files for free. This depends on the quality of encryption used by the malware authors.
Format and reinstall
If you can’t decrypt your files, formatting the drive and reinstalling your operating system is a last resort. This completely erases all data on the disk, however. So only attempt this if you have exhausted all other options and have backups.
How does encryption work?
To understand what happens when your files are encrypted, it helps to know what encryption does. Encryption uses an algorithm and a key to transform plain text into cipher text. It scrambles data in a way that only decrypting it with the right key can restore it to a readable form.
Here are the technical steps involved in encrypting and decrypting data:
- An encryption algorithm is used to encrypt plaintext data with a secret key
- This produces ciphertext data that looks scrambled and unintelligible
- The ciphertext and secret key are needed to decrypt the data
- Decryption applies the algorithm and key to transform the data back into plaintext
Modern encryption uses complex mathematical transformations to thoroughly obscure data. Without the proper key, decrypting the ciphertext is extremely difficult.
Types of encryption
There are a few different types of encryption that may be used on your files:
Symmetric encryption
Symmetric algorithms use the same key for encryption and decryption. Both parties need access to the secret key. Examples include AES and Blowfish.
Asymmetric encryption
Asymmetric or public key encryption uses a public key to encrypt data and a private key to decrypt it. Public key systems allow distributing the public key widely while private key is kept secret. RSA is a common public key algorithm.
Hybrid encryption
Hybrid schemes combine symmetric and asymmetric cryptography. Data is encrypted with a symmetric algorithm while the symmetric key is encrypted with asymmetric encryption. Provides performance benefits and additional security.
Why is encryption important?
Encrypting data provides the following key benefits:
- Prevents unauthorized access – Only people with the key can decrypt data
- Protects confidentiality – Sensitive data like financial or medical records can remain private
- Secures data in transit – Encrypts data going over networks to prevent eavesdropping
- Required for regulatory compliance – Regulations require encryption for certain types of data
- Defends against data theft – Encrypted data is useless if stolen or compromised
For these reasons, encryption is an essential technology for security and privacy in the digital age.
How can I encrypt my files?
You have several options for encrypting your own files and disks:
BitLocker
BitLocker is built into Windows Pro and Enterprise editions. It can encrypt entire disk volumes. Enable BitLocker via the Control Panel.
Windows Encrypting File System (EFS)
EFS encrypts files and folders on NTFS drives. Right-click files or folders to encrypt and select Properties > Advanced Attributes > Encrypt contents to secure data.
VeraCrypt
VeraCrypt is a free open source disk encryption utility. It can create encrypted containers or encrypt entire partitions. Provides stronger security than BitLocker.
GPG and GPG4Win
GPG or GNU Privacy Guard is used to encrypt files and messages. GPG4Win integrates GPG with Windows.
7-Zip
The free 7-Zip utility supports encrypting archived Zip files with AES-256 bit encryption. Just add password protection when creating an archive.
Encryption software
Many security and encryption programs, such as Symantec Drive Encryption, can encrypt disks, files, folders, and external media. Such software provides centralized management and enhanced features.
How do I decrypt encrypted files?
The specific steps to decrypt encrypted files depends on the encryption used:
BitLocker
To unlock a BitLocker encrypted drive, select the drive in Explorer and enter the BitLocker recovery key. Or log into Windows with the Microsoft account associated with BitLocker.
EFS Encryption
To decrypt EFS encrypted files, right-click the file, select Properties > Advanced Attributes > Decrypt contents to data. You may need to provide an encryption certificate.
Ransomware Encryption
For ransomware, restoring your files from a backup is the best method for decrypting your files without paying. Alternately, try malware decryption tools.
VeraCrypt
Mount your VeraCrypt volume and enter your password. VeraCrypt will decrypt and provide access to encrypted containers or partitions.
GPG Encryption
Use GPG commands like gpg –decrypt
7-Zip Encryption
Open your encrypted 7-Zip archive by providing the password when prompted. 7-Zip will then decrypt the archive contents.
Encryption Software
Follow the prompts from your encryption application to unlock encrypted volumes or files. You may need to provide keys, passwords, or certificates.
Can lost encryption keys be recovered?
If you lose the encryption keys or passwords for your files, recovery options are limited:
- Recovery keys – Software like BitLocker provides recovery keys to unlock encryption if you lose your password. These keys are critical.
- Key escrow – Some organizations keep copies of employees’ encryption keys in escrow. IT may be able to recover your key.
- Password reset – For encrypted archives like 7-Zip, the software can optionally reset passwords.
- Password cracking – A security firm may attempt to crack encryption by guessing the password. This is an expensive service with no guarantee of success.
- Data recovery service – For hardware encrypted drives, a recovery service can attempt to extract raw data off the drive bypassing encryption. Also expensive and not guaranteed.
As a lesson, always keep copies of encryption keys and passwords safe in case of loss! Losing the ability to decrypt data can lead to permanent data loss.
Can encryption be cracked?
Modern encryption methods like AES and RSA are considered unbreakable when implemented correctly. However, there are still ways determined attackers can potentially crack encryption:
Brute force attacks
Trying every possible password to crack encryption keys. Can be effective if weak passwords are used.
Cryptanalysis
Studying the algorithm to find mathematical weaknesses. Applies more to older outdated algorithms.
Quantum computing
Quantum computers may one day be able to quickly solve math problems used in cryptography. This could make cracking long keys feasible.
Backdoors
Secret backdoors implanted in encryption software by developers could bypass encryption. Backdoors are security risks if discovered.
Poor implementation
Badly implementing encryption protocols and using improper security parameters makes cracking easier. Proper implementation is vital.
While cracking modern encryption is unlikely, for extremely sensitive data additional protective measures like multi-layer encryption are warranted.
How can I prevent ransomware encryption attacks?
Ransomware poses a major threat, encrypting files and demanding payment for decryption keys. Here are tips to avoid ransomware attacks:
- Keep all software up-to-date since vulnerabilities enable most ransomware
- Exercise caution when opening emails and attachments from unknown senders
- Avoid visiting questionable websites and don’t download programs from sketchy sources
- Turn off macros in Microsoft Office to block malware
- Backup critical files regularly offline to enable restores after an attack
- Use security software with ransomware protection to detect threats
- Enable system shields like Microsoft Windows Defender Controlled Folder Access
Proactively protecting your data from ransomware is essential. Attack prevention is much easier than file decryption after the fact.
Conclusion
Finding your files mysteriously encrypted can be alarming at first. But understanding what causes file encryption and mastering decryption techniques helps overcome this situation. Encryption is also an important tool you can use to secure sensitive data if applied correctly. With the right knowledge, you can both prevent attacks and utilize encryption to keep your own files safe.