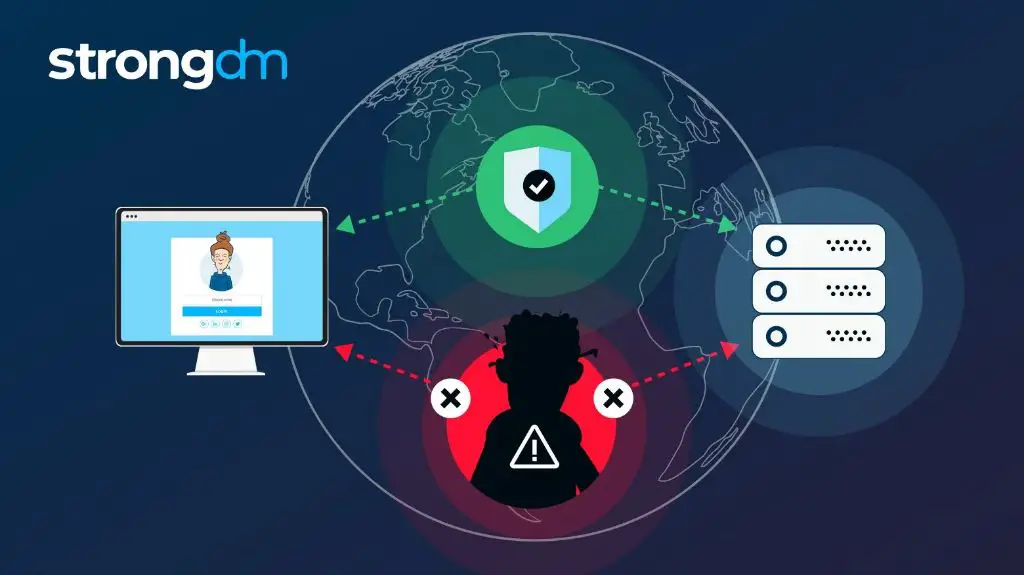
A man in the middle (MITM) attack is a form of cyberattack where the attacker secretly relays and possibly alters communication between two parties who believe they are directly communicating with each other. The attacker is able to intercept, send and receive data meant for the victims while being undetected.
An example of a MITM attack is when Alice wants to communicate with Bob, but Mallory sits between them and intercepts the communication. Alice thinks she is talking directly to Bob and Bob thinks he is talking directly to Alice, but in reality they are both communicating with Mallory who can now eavesdrop and modify the conversation without either of them realizing it.
How a MITM Attack Works
For a MITM attack to be successful, the attacker has to be able to intercept traffic between the victims. This can be achieved by different techniques:
- ARP spoofing – The attacker sends falsified ARP (Address Resolution Protocol) messages over the local network to link their MAC address with the IP address of the victim. This results in any traffic meant for the victim being sent to the attacker instead.
- DNS spoofing – The attacker provides a falsified DNS response to redirect traffic meant for the legitimate server to their own server instead.
- SSL stripping – The attacker intercepts an encrypted HTTPS connection and forces it to downgrade to an unencrypted HTTP connection so data can be read.
- WiFi eavesdropping – The attacker gains access to the same wireless network as the victims to intercept wireless traffic.
Once the attacker is able to intercept traffic, they can now act as a man in the middle and relay messages between the victims or even modify the contents of the communication.
Example Scenario
Here is an example scenario to illustrate how a MITM attack can work:
- Alice wants to access her bank account online and initiates a connection to her bank’s server.
- Mallory is connected to the same public WiFi network as Alice and employs ARP spoofing to trick Alice’s computer into sending data to Mallory instead of the bank’s server.
- Mallory establishes a separate connection to the bank’s server and now relays modified data between Alice and the bank, while intercepting the communication.
- When Alice tries to login, Mallory captures her login credentials and sends falsified responses back pretending to be the bank.
- Mallory is now positioned in the middle of the communication and has access to Alice’s account.
- Mallory can proceed to steal money, modify transaction records, intercept sensitive information etc. while Alice is unaware the communication has been compromised.
In this example, Mallory carried out a MITM attack by using ARP spoofing to intercept Alice’s connection to her bank. She was then able to position herself in the middle as a relay while also being able to view and modify any data sent between them. This allowed her to steal login credentials and access Alice’s bank account.
Real World Examples
There have been several real world examples of MITM attacks:
DigiNotar Attack
In 2011, Dutch certificate authority DigiNotar was breached by attackers who gained control of their systems to issue fraudulent SSL certificates. These certificates were then used to launch MITM attacks against Google services in Iran.
The attackers issued certificates for google.com and used them to impersonate Google servers. With the fake certificates they could intercept encrypted connections to Google services, decrypt the traffic and monitor Iranian users to censor or spy on them.
Around 300,000 Iranian users were impacted before the fraudulent certificates were revoked.
Lenovo Superfish Scandal
Between 2010-2015, some Lenovo laptops came preinstalled with adware called Superfish that included a potentially dangerous root CA certificate. This root certificate could be used to sign certificates for any website, allowing Superfish to perform SSL spoofing and intercept encrypted connections.
Even after Superfish was removed, the root certificate would still be trusted by the system, enabling attackers to use it for MITM attacks by signing forged certificates pretending to be legitimate servers. This exposed users to serious risks of malicious attacks, data theft and surveillance.
Operation Man-in-the-Middle
In 2011, it was reported that a cybercrime group called The Netragard Group was offering a Man-in-the-Middle attack service, referred to as “Operation Man-in-the-Middle”, targeting corporate executives while they traveled abroad.
The attackers would exploit vulnerabilities in hotel WiFi networks to position themselves between the victim and the internet. They could then steal credentials, inject malware into downloads, and access sensitive data including trade secrets sent over the connection.
Victims were often unaware their traffic had been compromised. The attacks highlighted risks from using public WiFi networks.
How to Prevent MITM Attacks
Here are some ways organizations and individuals can reduce risks of MITM attacks:
Use Encrypted Connections
Communicating over encrypted channels like HTTPS, SFTP or using a VPN can prevent third parties from reading intercepted traffic. However, MITM attacks can still work by downgrading or spoofing encrypted connections.
Verify Digital Certificates
Carefully verify the validity of SSL/TLS certificates to check for any signs of tampering. Ensure certificates are signed by a trusted certificate authority. Certificate pinning can also help prevent spoofing.
Use Strong Authentication
Multi-factor authentication and cryptographic authentication methods can make it harder for attackers to impersonate the server or bypass login protections.
Be Wary of Public WiFi
Avoid performing sensitive tasks like online banking over public WiFi networks as they make it easier to intercept connections. Use a cellular data connection or VPN if possible.
Use a Firewall
A network-based firewall can be configured to block suspicious activity like unexpected ARP traffic to prevent MITM techniques like ARP poisoning.
Monitor for Signs of Attack
Monitoring tools can check for anomalies like unusual spikes in network traffic, ARP entries changing unexpectedly, or suspicious DNS responses.
Employee Training
Training employees to recognize signs of MITM attacks and follow best practices for internet usage and online communication can improve defenses.
Conclusion
A man in the middle attack allows a malicious actor to intercept communications between two parties and compromise the integrity of the conversation. By relaying and even modifying traffic, the attacker can steal information or spread disinformation while remaining undetected.
Common techniques like ARP spoofing and SSL stripping can allow attackers to position themselves in the flow of data and eavesdrop on traffic meant to be secure. Real world examples have shown how criminals have leveraged MITM attacks to spy on users, steal credentials and sensitive information.
Using encrypted connections and being cautious on public WiFi networks can reduce exposure to such attacks. But ultimately organizations need layered defenses including firewalls, authentication methods, monitoring and employee training to address modern MITM techniques and risks.