EDR (Endpoint Detection and Response) and XDR (Extended Detection and Response) are two important cybersecurity technologies that organizations use to detect and respond to threats. While they have some overlap in capabilities, there are also key differences between EDR and XDR:
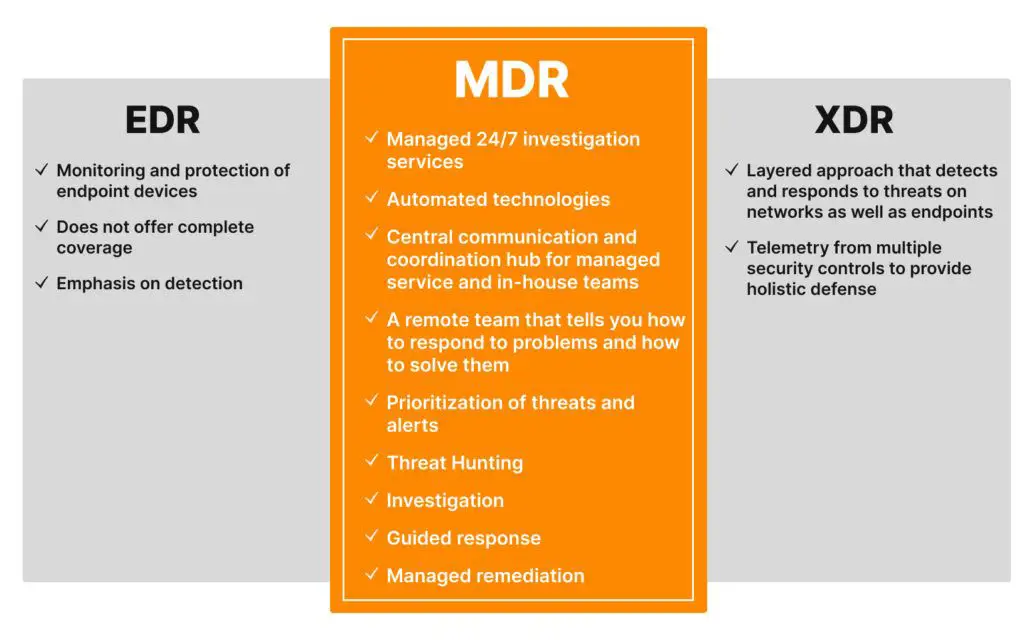
What is EDR?
EDR solutions are focused on monitoring and analyzing activity on endpoints like laptops, desktops, and servers. Key capabilities of EDR include:
- Monitoring endpoints for suspicious activity and anomalies
- Detecting malicious code execution, lateral movement, data exfiltration, and other threats
- Providing visibility into the scope and impact of threats across endpoints
- Enabling rapid response actions like isolating infected endpoints
EDR uses agents installed on each endpoint to collect detailed data like process activity, registry changes, network connections, and file activity. This data is sent to a central EDR server where it is analyzed using techniques like machine learning, behavior analysis, and threat intelligence to detect attacks.
EDR emerged as a critical security control to overcome limitations of traditional antivirus. Signature-based antivirus cannot reliably detect newer threats like fileless attacks, malware variants, and zero days. EDR provides more advanced behavioral threat detection across endpoints.
What is XDR?
XDR (extended detection and response) is a broader approach that expands detection and response capabilities beyond the endpoint. Key capabilities of XDR include:
- Ingesting and correlating data from multiple security layers – endpoints, network, cloud, etc.
- Analyzing security telemetry from diverse infrastructure using threat intelligence
- Identifying threats across kill chain stages – command and control, reconnaissance, lateral movement, etc.
- Centralized visibility of security alerts and incidents across environments
- Orchestrating and automating response across security layers
XDR aggregates alerts and data from EDR as well as other security controls like firewalls, secure web gateways, cloud access security brokers, and more. This provides broader visibility across hybrid environments. XDR leverages centralized threat intelligence for better detection of multi-stage attacks across security layers.
Key Differences Between EDR and XDR
While EDR and XDR have some common capabilities like threat monitoring, detection, and response, there are several key differences:
| EDR | XDR |
| Focused on endpoints | Aggregates data across multiple security layers like network, cloud, identity |
| Agent-based approach | Agent and agentless approach |
| Detects malicious behavior on endpoints | Correlates threats across endpoints, network, cloud, etc. |
| Isolates infected endpoints | Orchestrates response actions across security layers |
| Provides visibility into impacted endpoints | Provides broader visibility across hybrid environment |
In summary, while EDR is designed to monitor endpoint activity in depth, XDR aims to provide expanded visibility and threat detection across hybrid environments by ingesting data from multiple security controls.
EDR Use Cases
Here are some of the key use cases and benefits of EDR solutions for security teams:
- Faster threat detection: EDR uses behavioral analytics to quickly detect attacker behaviors like unusual process executions, privilege escalations, DLL injections that indicate malware or compromise.
- Rapid incident response: EDR allows security teams to quickly search across endpoints during investigations, determine scope of compromise, and take actions like quarantining infected machines.
- Blocking of exploit activity: When advanced techniques like process hollowing, pass the hash, or script-based attacks occur, EDR can block the suspicious activity using pre-defined policies.
- Threat hunting: The rich endpoint visibility provided by EDR allows security analysts to proactively hunt for IOCs, behavioral indicators, and anomalies to find advanced threats.
- Forensics and attribution: Detailed EDR data enables deep dive forensics into how an attack occurred and attribution to identify the attackers.
EDR is critical for detecting and responding to advanced endpoint threats emerging through vectors like phishing, malicious downloads, lateral movement, exploits, and insider attacks.
XDR Use Cases
Here are some of the key use cases and benefits of XDR solutions:
- Detecting sophisticated, multi-vector threats: XDR can correlate suspicious behaviors across endpoints, network, cloud, and users to uncover stealthy attacks moving across environments.
- Accelerated incident response: XDR centralizes alerts, data, and workflows – allowing faster investigation, containment, and remediation across on-prem and cloud deployments.
- Unified visibility and analytics: Security teams get a single comprehensive view of threats across hybrid environments rather than siloed visibility.
- Simplified operations: Converging EDR, NDR, SWG, CSPM, UEBA into XDR stack reduces tool sprawl, overlaps, and complexity for SecOps teams.
- Proactive threat hunting: Security analysts can pivot across enriched datasets from endpoints, network, logs, and cloud to uncover difficult-to-detect threats.
XDR enables organizations to achieve tighter security coverage, faster threat detection, and more automated response across today’s complex hybrid environments.
Factors to Consider When Comparing EDR vs XDR
Organizations should keep several factors in mind when evaluating EDR and XDR solutions:
- Deployment model: EDR typically relies on endpoint agents while XDR can ingest agent as well as agentless data. Agentless XDR provides broader coverage but may miss some endpoint activity.
- Breadth of visibility: XDR provides significantly broader visibility across hybrid infrastructure while EDR is focused on endpoint activity.
- Detection and analytics: The quality, accuracy, and sophistication of detection algorithms and analytics differ across EDR and XDR vendors.
- Response capabilities: Both EDR and XDR aim to provide automated response but maturity varies based on vendor capabilities.
- Integration and interoperability: XDR promises consolidation but some vendors take an open approach while others favor proprietary stacks.
- Operational overhead: Adoption of XDR aims to reduce operational complexity but oversight is required to maximize value.
Organizations should carefully evaluate product design, detection efficacy, automation capabilities, and operational considerations when comparing vendor solutions.
When to choose EDR over XDR?
Here are some scenarios where organizations may prefer implementing EDR solutions over XDR:
- When the main concern is monitoring and securing endpoints due to remote workforce, bring your own device (BYOD), and cloud adoption.
- When prevention-focused controls like antivirus, firewalls, sandboxing already exist and EDR is needed as a secondary detective control.
- When compliance requirements mandate endpoint threat detection and response specifically.
- In regulated industries like healthcare and finance where endpoint security is a critical requirement.
- When IT and security teams have limited staff to manage security operations – EDR is lighter weight than XDR.
- For organizations with primarily on-premise infrastructure making centralized visibility less critical.
For organizations focused heavily on endpoint security and already leveraging some network and cloud controls, implementing best-of-breed EDR can provide significant value without the added cost or complexity of XDR.
When does XDR make more sense over EDR?
Here are some scenarios where investing in XDR may provide stronger advantages compared to adopting only EDR:
- For organizations with complex hybrid environments including cloud IaaS, SaaS, multi-cloud, OT networks.
- When attackers are expected to leverage multiple entry points and move laterally across on-prem and cloud environments.
- When there are significant gaps in visibility across network, cloud, user behaviors, and endpoints.
- When multiple point security tools are creating data siloes, operational inefficiencies, and coverage gaps.
- For mature security organizations looking to optimize operations through tighter technology integration and automation.
- To enable proactive threat hunting across hybrid infrastructure via centralized data lake and analytics.
XDR can provide strong advantages for organizations that need unified visibility, advanced threat detection, and integrated response across their broader security architecture.
Deployment Options for EDR and XDR
EDR and XDR offer organizations flexibility in terms of deployment models:
EDR Deployment
- Agent-based: EDR relies on agents installed on each endpoint for maximum visibility. Agents are available across OS platforms like Windows, macOS, Linux.
- On-premises deployment: EDR server and console can be deployed internally where endpoint data is aggregated and retained based on organizational policies.
- Cloud-delivered: EDR capabilities can be delivered via vendor’s cloud platform for faster deployment while data remains within customer environment.
- Hybrid models: Combination of on-prem EDR servers as well as cloud-hosted console and analytics capabilities.
XDR Deployment Options
- Cloud-native deployment: XDR suite hosted and managed via vendor cloud platform. Provides faster time-to-value but some data residency concerns.
- On-premises deployment: XDR server reside on-premises, keeping data local while providing centralized visibility across endpoints, network, etc.
- Hybrid deployment: Blend of on-prem and cloud components. Sensitive data remains local while cloud enhances analytics, automation capabilities.
- Agent vs agentless: Agent-based for endpoint visibility. Agentless options for ingesting network, cloud, identity data.
Organizations should consider their specific infrastructure, use cases, and regulatory requirements when choosing EDR and XDR deployment architectures.
Top EDR Vendors and Solutions
Some of the leading EDR solutions include:
- CrowdStrike Falcon: Uses lightweight, cloud-scalable agents and an intelligent, cloud-based engine for next-gen EDR and managed threat hunting capabilities.
- SentinelOne Singularity: Leverages AI models trained on millions of samples to provide EPP and EDR via a single, autonomous agent.
- Microsoft Defender for Endpoint: Built into Windows 10 and Microsoft 365, Defender for Endpoint provides unified EPP and EDR natively.
- Cisco Secure Endpoint: Combines NGAV and EDR via continuous monitoring, behavioral analysis, isolation, and threat intelligence.
- Carbon Black Cloud: Uses predictive security models to offer EPP, EDR, managed threat hunting and incident response capabilities via the cloud.
Leading EDR vendors leverage automation, AI, and threat intelligence to accurately detect and quickly respond to targeted attacks, insider threats, and advanced malware across endpoints.
Leading XDR Security Platforms
Prominent XDR platforms include:
- Palo Alto Networks Cortex XDR: Integrates network, endpoint, and cloud data sources using machine learning and behavioral analytics for threat prevention and detection.
- Cisco SecureX: Unified platform stitches together capabilities from Cisco’s broad security portfolio into a cloud-native XDR solution.
- Microsoft Sentinel: Leverages AI to automate tasks like threat detection, hunting, and response across on-prem and cloud environments.
- Trend Micro Vision One: XDR solution that natively integrates Trend Micro security controls and third party products via open API.
- Cynet 360: Converges EDR, NDR, Deception, and UEBA using agentless approach and threat correlations to accelerate detection.
Leading XDR providers offer robust threat detection, consolidated visibility and control across hybrid infrastructure, and advanced analytics for security teams.
Choosing the Right EDR vs XDR Vendor
Here are some best practices for evaluating and choosing EDR and XDR vendors:
- Document your use cases, business requirements, and technical needs.
- Assess detection efficacy, false positives, transparency of ML/AI models.
- Review third party validation like MITRE ATT&CK, NSS Labs testing.
- Compare response capabilities – containment, remediation. automation features.
- Evaluate platform architecture – agent vs agentless, cloud vs on-prem.
- Assess vendor product vision and pace of innovation.
- Ensure integration capabilities with your existing security stack as needed.
- Consider vendor stability and viability for the long term.
Choosing the right EDR or XDR partner requires evaluating multiple dimensions from product capabilities to vendor characteristics. Work closely with vendors to prototype solutions before purchase.
Conclusion
EDR and XDR are both rapidly evolving technologies aimed at helping security teams enhance threat detection and response across modern environments.
EDR provides deep endpoint monitoring, behavioral threat detection, and rapid response capabilities for endpoint security. XDR expands this visibility across network, cloud, identity, and additional telemetry – providing a more holistic view of threats across hybrid infrastructure.
Organizations should consider factors like use cases, hybrid environment complexity, team skillsets, and integration requirements when deciding between EDR and XDR solutions. Vendor evaluation across multiple criteria can help identify the right platform for your requirements and risk profile.
While EDR has become a security staple, XDR adoption is growing steadily as organizations aim to consolidate visibility, improve threat lifecycle coverage, and enable tighter technology integration. The advanced analytics and automation of these emerging platforms allow lean security teams to more effectively combat increasing cyber risks.