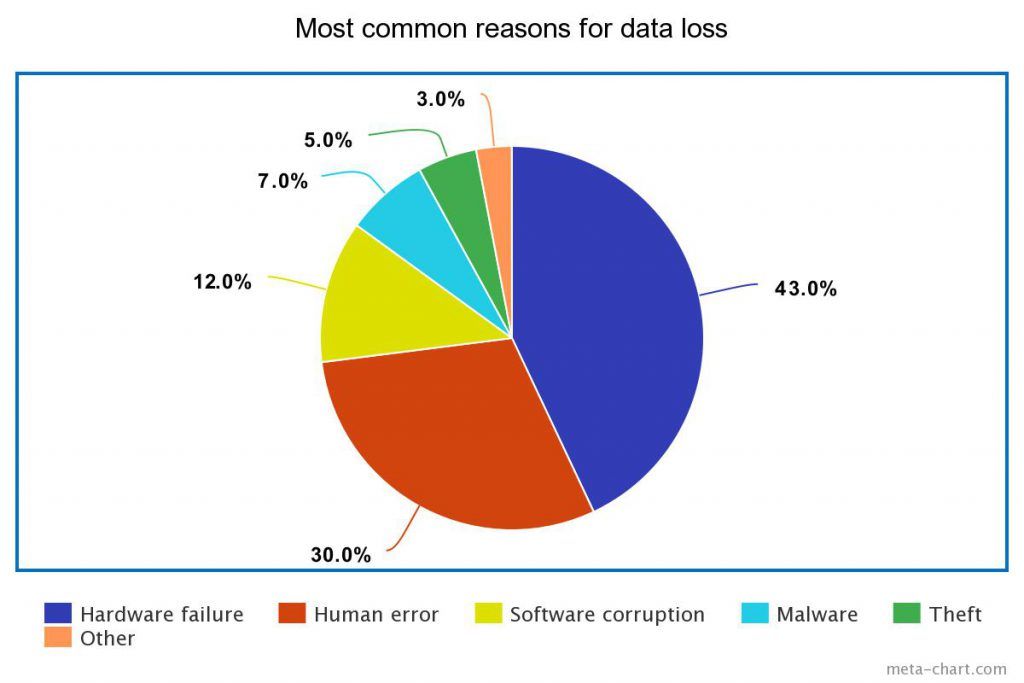
Data loss is a major problem for individuals and organizations alike. Losing important data can lead to significant disruption, downtime, and costs. Understanding the most common causes of data loss is the first step towards preventing it.
Conclusion
In summary, the most common causes of data loss are:
- Hardware failure – Hard drives and other storage devices can unexpectedly fail due to component issues or general wear and tear over time.
- Accidental deletion – Users may inadvertently delete files and later realize they still need them.
- Malware and ransomware – Malicious software is designed to damage, delete or encrypt data.
- Natural disasters – Events like fires, floods or earthquakes can damage or destroy storage devices.
- Human error – Mistakes made during upgrades, migrations or routine maintenance.
- Theft – Lost or stolen devices that contain important data.
While no single solution can fully prevent data loss, following best practices around continuous backups, security, redundancy, and user training can significantly reduce risk. Organizations should have a disaster recovery plan in place specifying how critical systems and data can be restored after an incident.
What causes hardware to fail?
Hardware failure is one of the top reasons for data loss. The components that make up storage devices are vulnerable to damage and degradation over time. Some common hardware failure causes include:
- Mechanical failure – Moving parts like disk platters and read/write heads eventually wear out.
- Electrical failure – Power surges, voltage spikes, lightning strikes or component issues can cause circuitry to malfunction.
- Firmware corruption – Bugs, crashes or attacks against firmware and low-level software.
- Factory defects – Imperfect manufacturing can leave flaws in hardware that lead to premature failure.
- Overheating – Excessive heat buildup can damage processors, memory and other circuitry.
- Water damage – Liquids spilled on devices can short circuit electronics.
Server hard disk drives (HDDs) have an annualized failure rate of around 4%, with higher rates as they age past 3 years. Consumer drives fail up to 10 times more often. Solid state drives (SSDs) are less prone to mechanical failure, but still have an expected lifetime around 5-10 years due to write exhaustion.
How can hardware failure be prevented?
Some steps to improve hardware reliability include:
- Choosing enterprise-grade components designed for 24/7 operation.
- Following manufacturer recommendations for temperature, humidity, vibration, dust control, etc.
- Regularly inspecting hardware for signs of wear and proactively replacing components.
- Using uninterruptible power supplies (UPS) and surge protectors.
- Enforcing hardware redundancy so single points of failure are eliminated.
- Purchasing extended warranty and support contracts for mission critical systems.
Why do users accidentally delete files?
Human error is a major contributor to data loss. Industry studies estimate between 20-30% of data loss incidents are caused by accidental deletion. Some common mistakes users make include:
- Misclicks – Deleting the wrong file or folder when hurriedly managing files.
- Assumed redundancy – Thinking a file exists elsewhere so deleting local copies to save space.
- Emptying recycle bin – Permanently erasing files considered useless but later found to be important.
- Formatting wrong drive – Not paying close attention and formatting the wrong partition or external drive.
Accidental deletion is not isolated to individual users. IT administrators may also inadvertently delete production databases and backup files during complex maintenance procedures if not extremely careful.
How can accidental file deletion be avoided?
Strategies to reduce accidental deletion include:
- Being cautious when managing files and not rushing deletion decisions.
- Moving files to recycle bin instead of permanently deleting when possible.
- Not relying on redundancy and maintaining known copies of critical files.
- Using confirmation prompts before formatting disks or deleting large batches of data.
- Following formal change management procedures for administrative tasks.
- Using backups to recover accidentally lost data.
What types of malware destroy data?
Cyber attacks have become an ever-present risk for organizations. Malware designed specifically to damage, delete or encrypt data can lead to severe data loss incidents. Common malware types include:
- Ransomware – Encrypts files until a ransom payment is made, though decryption is not guaranteed.
- Wiper malware – Seeks out and deletes or corrupts data and files on a network.
- Disk formatter – Malware that intentionally formats hard drives.
In addition to purpose-built data destruction malware, other types like viruses, worms, spyware and trojans can also cause file corruption as a side effect of their main behaviors.
Is it possible to stop malware from damaging data?
Malware defense is an ongoing battle as new threats emerge constantly. Steps organizations can take include:
- Training employees to identify social engineering and phishing attempts.
- Keeping all software up-to-date with the latest security patches.
- Using anti-virus/anti-malware tools and intrusion detection systems.
- Regularly scanning networks to identify threats.
- Blocking suspicious file extensions and websites via firewall policies.
- Implementing least privilege permissions to limit damage from threats.
- Backing up data regularly to offline, immutable storage.
How do natural disasters cause data loss?
Environmental catastrophes like fires, floods, earthquakes and severe storms are risks depending on geographic location. These events can damage or destroy storage infrastructure and equipment leading to data unavailability. For example:
- Fires – Heat, smoke and water used for suppression can render computer hardware unusable.
- Floods – Water damage from flooding can make systems inaccessible even after drying.
- Earthquakes – Vigorous shaking can knock disk drives out of alignment so data cannot be read.
- Lightning – Power surges can fry sensitive electronics and erase magnetic storage media.
Natural disasters typically damage hardware, but do not erase data from storage devices. However, if backups and redundant systems are also destroyed, the data may be unrecoverable.
How can data be protected from natural disasters?
Mitigating data loss risks from natural disasters involves steps like:
- Locating IT infrastructure and backups in geographically distinct areas.
- Building computer rooms with fire suppression, elevated floors, and leak protection.
- Waterproofing and securing IT equipment to withstand seismic events.
- Using fire/flood resistant storage media like optical discs.
- Contracting multiple internet providers to avoid single point of failure.
- Distributing cloud backups across regions and providers.
What human errors commonly lead to data loss?
Beyond accidental file deletion, human mistakes made during IT operations and data migrations are another key data loss vector. Examples include:
- Improper system configuration – Misconfiguring storage and backups leading to corruption or missing data.
- Failed upgrades – New software versions not installed properly.
- Erasing the wrong drive – Choosing the incorrect disk during partitioning or reformatting.
- Incorrect data handling – Mishandling backups and storage media leading to damage.
High-impact disasters have been caused by administrators unintentionally running deletions against production instead of test databases. Proper oversight and change control is crucial.
What safeguards help avoid data loss from human error?
Organizations can implement several safeguards including:
- Automated testing to catch errors before they impact production.
- Detailed rollback plans in case changes need to be reversed.
- Immutable backups and snapshots to recover from mistakes.
- Requiring peer reviews and approval for major changes.
- Audit logging to identify who made unauthorized modifications.
- Restricting access and permissions to minimize insider risks.
How does data theft and loss occur?
Theft of storage devices is still a relevant data loss avenue in the modern workplace. Laptops, USB drives and backup tapes containing sensitive data are especially vulnerable. Common data theft and loss modes include:
- Misplaced portable storage – USB drives, tapes, disks get lost or left behind in transit.
- Stolen laptops – Unsecured laptops get stolen, exposing any data stored locally.
- Theft from data centers – Servers or drives stolen by malicious insiders or intruders.
- Dumpster diving – Company data improperly disposed of in the trash.
In addition to overt theft, employees may accidentally or intentionally leak data in unauthorized ways that violate security policies.
How can organizations avoid data theft?
Safeguards against data theft and loss include:
- Encrypting data at rest and in transit.
- Restricting use of portable storage and requiring encryption.
- Securing laptops with cable locks, tracking software and remote wipe capabilities.
- Proper destruction of old hard drives and media using degaussing and shredding.
- Physical access controls and surveillance cameras for facilities.
- Security training for employees handling sensitive data.
- Data loss prevention systems to monitor and control data flows.
What backup strategies help recover from data loss?
While best practices around data security and risk reduction are invaluable, data loss cannot be completely eliminated in most environments. The ability to reliably restore lost data through backups is therefore critical. Backup types include:
Local Backups
- File copy – Manual or automated duplication of files to another disk.
- Snapshot – Point-in-time disk image capturing changes over time.
- Incremental – Only backs up changed files since prior backup.
- Disk cloning – Full copy of a disk volume to another disk.
Offsite Backups
- Remote servers – Backup transfer over WAN to distant facilities for geographic redundancy.
- Cloud storage – Data replication to managed cloud-based object storage.
- Physical media – Tapes or external hard drives rotated offsite.
A resilient 3-2-1 backup strategy is recommended – at least 3 copies, on 2 different media types, with 1 copy offsite. Test restoration regularly.
Backup Security Considerations
- Encrypt backups to prevent unauthorized access
- Use disconnected storage for offline backups not continuously exposed
- Immutable backups prevent deletion or encryption by malware
- Backups must have read-only permissions to limit tampering
With strong backup policies, processes, and security in place, organizations can confidently recover from almost any data loss scenario.
Conclusion
In summary, the most common causes of data loss are:
- Hardware failure – Hard drives and other storage devices can unexpectedly fail due to component issues or general wear and tear over time.
- Accidental deletion – Users may inadvertently delete files and later realize they still need them.
- Malware and ransomware – Malicious software is designed to damage, delete or encrypt data.
- Natural disasters – Events like fires, floods or earthquakes can damage or destroy storage devices.
- Human error – Mistakes made during upgrades, migrations or routine maintenance.
- Theft – Lost or stolen devices that contain important data.
While no single solution can fully prevent data loss, following best practices around continuous backups, security, redundancy, and user training can significantly reduce risk. Organizations should have a disaster recovery plan in place specifying how critical systems and data can be restored after an incident.