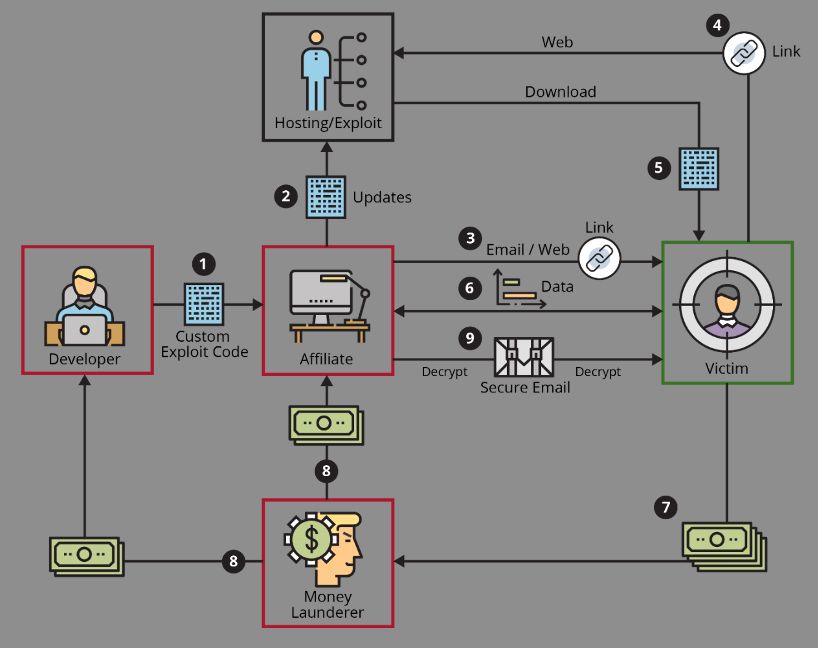
Ransomware as a service (RaaS) is a cybercrime model where malware creators sell or lease ransomware tools and infrastructure to other cybercriminals. This allows criminals with limited technical skills to easily deploy ransomware attacks. RaaS has made ransomware more accessible, fueling a rise in attacks. Understanding the RaaS model and its implications is key to defending against this threat.
What is ransomware?
Ransomware is a form of malicious software that encrypts files on a device or network, preventing access until a ransom is paid. Attackers demand payment, often cryptocurrency, in exchange for decryption keys to restore access. If victims refuse or cannot pay, they risk permanent data loss.
Some key features of ransomware include:
- Encryption of files, making them inaccessible
- Threats and demands for payment in return for decryption
- Time limits or threats of permanent data destruction
- Methods of payment difficult to trace, like cryptocurrency
Ransomware attacks can be highly disruptive, leading to loss of critical data and downtime. Industries like healthcare and government are common targets.
Evolution of the ransomware business model
Early ransomware attacks often involved basic malware distributed randomly via mass email campaigns. Attackers had limited ways to collect ransom payments.
Over time, ransomware became more sophisticated. Developers professionalized the ransomware business model by:
- Creating ransomware-as-a-service to sell to other criminals
- Using cryptocurrency to enable anonymous ransom payments
- Targeting victims strategically for greater impact
- Threatening leak of data as additional extortion
These shifts made ransomware much more lucrative for attackers while increasing risk for victims.
What is ransomware as a service?
Ransomware as a service allows cybercriminals to carry out ransomware campaigns without needing extensive expertise. RaaS works by means of a subscription model:
- Developers create ransomware tools and infrastructure
- They lease or sell access to “affiliates” for a fee or profit sharing
- Affiliates then execute attacks using the developer’s ransomware
Many RaaS programs operate via dark web marketplaces and cryptocurrency payments. The RaaS model provides crimeware to less technical criminals.
Key components of ransomware as a service
RaaS offerings often include some combination of:
- Customizable ransomware executable files
- Command and control hosting infrastructure
- Dashboards for managing infections and ransom payments
- Cryptocurrency wallets for receiving ransom
- Payment infrastructure for ransom collection
- Affiliate programs for recruiting partners
- Support services for affiliates
By leveraging RaaS, an affiliate can launch ransomware campaigns with minimal overhead. The RaaS developer handles most technical aspects.
Why is ransomware as a service so dangerous?
Ransomware as a service makes ransomware more accessible and scalable for criminals. Some key factors make RaaS a major security risk:
- Low barrier to entry – Affiliates can launch attacks with little technical know-how
- Specialization of labor – Developers improve ransomware quality while affiliates distribute it
- Scalability – RaaS allows ransomware campaigns to grow rapidly
- Ease of obfuscation – Cryptocurrency and hosting infrastructure hide criminal activity
- High reward potential – RaaS makes ransomware profitable for criminals
These factors have contributed to the ransomware explosion in recent years. Cybercriminals with varying skill levels can now wield potent ransomware.
RaaS drives ransomware proliferation
The RaaS model has proliferated advanced ransomware families like:
- REvil
- Conti
- LockBit
- Ragnar Locker
- DarkSide
These tools allow even low-skilled affiliates to target large enterprises. RaaS developers innovate new capabilities like initial access brokers, data leak extortion, and triple extortion.
Widespread RaaS adoption resulted in a 130% annual increase in global ransomware attacks from 2019 to 2020.
Case study: GandCrab RaaS
The GandCrab ransomware exemplifies the RaaS model’s success. Key facts include:
- Emerged in 2018 using a RaaS model
- Developers leased access to affiliates for 40% of ransom profits
- Affiliates executed over 50,000 attacks in 14 months
- Victims paid over $2 billion in ransom
- GandCrab shut down voluntarily in 2019
This case demonstrates how the RaaS model can produce highly profitable ransomware at massive scale. GandCrab helped pioneer RaaS for monetizing ransomware.
Real-world ransomware as a service campaigns
RaaS developers often run sophisticated operations, including:
Targeted marketing and sales
Developers recruit affiliates through dark web ads, listings, and affiliate programs. Marketing targets criminal forums frequented by hackers.
Tiered pricing and service packages
Platforms offer tiered pricing with levels of service. Basic tiers may be ~$400 per month with limited support. Higher tiers around $1,500 monthly provide premium ransomware and services.
Extensive customer support
Many RaaS developers offer robust technical support, making the ransomware easy to deploy for affiliates. Support guides and staff help affiliates execute campaigns.
User-friendly infection and management interfaces
Web-based dashboards allow affiliates to manage infections and ransom payments with ease. These tools remove technical barriers for novice cybercriminals.
Evasion of detection
Developers work to mask ransomware activity from security tools. Tactics include encryption, obfuscation, anti-analysis, and anti-forensics capabilities.
Threat actor division of duties
RaaS often divides duties across specialties:
- Developers build and refine ransomware
- Affiliates compromise networks and deploy ransomware
- Partners provide services like money laundering
This distribution of labor increases efficacy of operations.
Trends and developments in ransomware as a service
RaaS continues advancing in sophistication. Some emerging trends include:
Double and triple extortion tactics
Many ransomware groups now exfiltrate data before encrypting networks. Stolen data gets used for additional extortion:
- Encrypt network (1st extortion)
- Threaten data leak (2nd extortion)
- DDoS victim (3rd extortion)
With triple extortion, victims face escalating pressure to pay ransom demands.
Initial access brokers
Access brokers hack networks and sell that initial access to ransomware groups. This division of labor results in more ransomware infections.
Ransomware farms and builders
Some tools now semi-automate the creation of ransomware strains. Ransomware builders enable quick generation of new variants to evade security defenses.
Ransomware as a service pipelines
Experienced ransomware groups offer end-to-end RaaS pipelines. These fully managed offerings cover compromising networks, deploying ransomware, and negotiating payments all on behalf of affiliates.
Defending against the threat of ransomware as a service
Combating the growing RaaS threat requires proactive security measures across people, processes, and technology. A multi-layered defense is key, including:
User awareness training
Train employees to identify social engineering attacks, suspicious links/attachments, and other warning signs. Human errors often enable initial access.
Least privilege and segmentation
Limit user permissions and segment networks to restrict adversary lateral movement. This contains damage from ransomware.
Endpoint detection and response
Deploy EDR to continuously monitor endpoints. Machine learning can identify ransomware and other threats early.
Network traffic analysis
Analyze network patterns to uncover command and control activity, data exfiltration, and other malicious signals.
Backups and recovery planning
Maintain regular backups offline to enable restore after an attack. Test recovery procedures regularly.
Incident response planning
Have an IR plan for rapidly containing ransomware and investigating incidents. Practice the plan via threat simulations.
Blending these measures provides layered security against the diverse RaaS threat landscape.
The future of ransomware as a service
Ransomware as a service continues to pose severe risks due to its accessibility, scalability, and profitability for threat actors. Ongoing RaaS trends to watch include:
- Increasingly sophisticated evasion of security defenses
- Shifts to new platforms and extortion models
- Targeting of critical infrastructure sectors
- Creative social engineering to enable access
- Price wars and consolidation among ransomware groups
- Coordinated campaigns across ransomware families
As long as the RaaS model remains viable, ransomware shows no signs of slowing down. Organizations must remain vigilant and take proactive measures to manage the risk.
Conclusion
Ransomware as a service empowers criminals to deploy ransomware at an unprecedented scale. By providing easy-to-use ransomware infrastructure, the RaaS model drives much of today’s ransomware epidemic. Understanding this threat ecosystem equips organizations to enhance their defenses and resilience.
Combating RaaS necessitates a coordinated effort across security technologies, processes, and personnel training to protect networks. As ransomware tactics continue advancing, defending against RaaS ultimately requires constant vigilance and dedication across these facets of security.