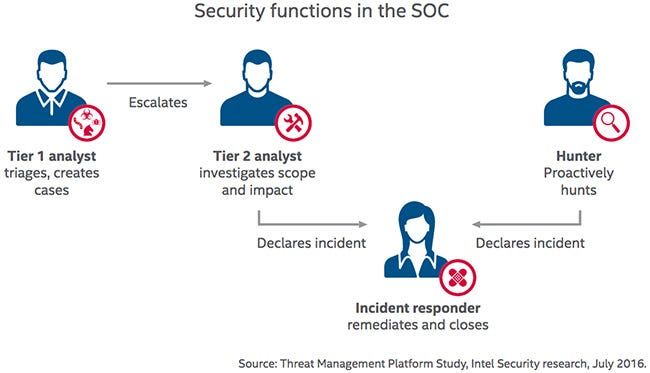
What is Triaging in SOC?
Triaging in the context of a security operations center (SOC) refers to the process of detecting, validating, and prioritizing security events and alerts as potential incidents requiring investigation and response (CCS Learning Academy, 2023). It involves reviewing alerts and events from various security tools and systems, analyzing and correlating the data to determine the severity and priority of threats.
Triaging is a critical function of SOCs as it enables quick identification of real threats from the thousands of alerts generated daily. Through triaging, analysts can focus investigation and response efforts on the most critical incidents first. Rapid triaging minimizes potential damages by initiating containment and remediation early in the cyber kill chain. It also provides valuable context to guide further analysis and decision making during incident response.
Effective triaging is essential for SOCs to efficiently detect and respond to security incidents within their limited resources. It allows them to optimize analyst time and reduce risks by promptly addressing the most imminent and impactful threats.
Triaging Process
The triaging process in security operations centers (SOCs) involves going through incoming security alerts and events to determine their priority for investigation and response. The key steps involved in triaging typically include:
1. Establish a triage process – Define the workflow, criteria, and tools to be used for reviewing and prioritizing alerts.
2. Prioritize alerts – Review alerts as they come in and assign priority levels based on criteria like criticality of affected assets, severity ratings, confidence levels etc. Critical alerts get addressed first.
3. Collect contextual information – Gather additional details about the alert such as affected assets, timestamps, user accounts etc. to aid in analysis.
4. Analyze the alert – Using the priority level, contextual information and security analysts’ expertise, determine if the alert signifies a security incident.
5. Categorize the alert – Categorize valid alerts as true or false positives. True positives are further categorized as critical, high, medium or low priority for SOC response.
Triaging enables SOCs to quickly identify the most critical threats facing the organization’s infrastructure, systems and data. By systematically reviewing and prioritizing a high volume of security alerts, triaging ensures that analyst time and effort is focused on investigating and responding to the most significant incidents first.
Goals of Triaging
The primary goals of triaging in SOC are to:
- Reduce noise and false positives – Triaging helps filter out alerts that aren’t indicative of real threats, reducing unwanted noise and allowing analysts to focus on legitimate attacks.
- Identify real threats quickly – By establishing severity levels and prioritizing alerts, triaging enables rapid identification of the most critical threats needing urgent response.
- Prioritize response efforts – Triaging ranks incidents by importance and urgency so that analysts know where to focus first. This ensures the most dangerous threats are addressed immediately.
As stated in the article from CCS Learning Academy, effective triaging provides “faster detection, response, and resolution of threats.” Analysts must act quickly, and triaging gives them the focus and priorities needed for rapid response.
Triaging Models
There are a few triaging models that help security teams prioritize and respond to threats efficiently. Two popular models are the pyramid of pain and the 1-10-100 rule.
The pyramid of pain categorizes threat intelligence into different tiers based on the time and resources required for adversaries to recover from disruption. The bottom levels like hashes and IP addresses are easiest to change, while the top levels like tools and infrastructure require more time and effort to replace. Focusing higher up the pyramid creates more lasting impact.
The 1-10-100 rule states that it takes 10 times more effort to contain a threat than to detect it, and 100 times more effort to eradicate a threat than contain it. This model emphasizes the importance of early detection and rapid containment before threats spread and cause greater damage.
Both models provide frameworks to identify threats that are higher risk, more severe, and have broader impact. By guiding security teams to prioritize disruptive actions higher up the pyramid or earlier in the cyber kill chain, these models enable more effective use of resources.
Triaging Tools
Tools play a critical role in facilitating and automating the triaging process in a SOC. Common tools used for triaging include the SIEM, ticketing system, and specialized triage platforms.
The SIEM (Security Information and Event Management) system collects and correlates log data to detect threats. It will generate alerts that security analysts will need to triage to determine if they require further investigation. SIEMs like Splunk, IBM QRadar, and AlienVault provide capabilities to view, filter, and analyze alerts during triaging.
Ticketing systems like ServiceNow are used to create, assign, and track security incidents. Tickets are generated for alerts that require further action after triaging. The ticketing system provides important context during triaging like previous tickets related to an alert.
Specialized triaging tools like Cyber Triage are emerging to optimize and automate parts of the triaging workflow. These platforms use techniques like machine learning to prioritize alerts, accelerate data collection, and determine the appropriate response.
By leveraging the right tools, SOC analysts can triage large volumes of daily alerts more efficiently. The tools facilitate filtering, correlation, documentation, and other key triaging capabilities.
Triaging Techniques
There are several techniques security analysts use during the triaging process to help sort through and prioritize alerts efficiently. Some common triaging techniques include:
Clustering – Clustering involves grouping related alerts together based on common attributes like source IP, destination IP, signature, etc. Clustering helps analysts identify campaigns of attacks and focus on the most prevalent threats first. According to a report by Axonius, clustering reduced alert triage time by 15% for many organizations.
Tagging – Tagging alerts with relevant metadata like categories, severity levels, indicators of compromise etc. allows analysts to filter and search alerts more easily. Proper tagging improves focus on the highest priority threats during triaging. As per research by LinkedIn, tagging accounts for a 20% improvement in triage productivity.
Rules – Creating event rules and custom signatures helps auto-categorize incoming alerts, separating noise from alerts that require human analysis. This removes a significant triaging burden from analysts. According to Blueteamresources, well-defined rules can decrease manual triaging time by 30-40%.
Overall, leveraging techniques like clustering, tagging, and rules tuning allows analysts to cut through the noise and focus their efforts on critically analyzing and responding to the most potentially malicious threats. This results in a more efficient triaging process.
Triaging Challenges
Security operations center (SOC) analysts face several key challenges when triaging alerts that can impact their efficiency and effectiveness:
Large volume of alerts – According to Swimlane, “44% of an analyst’s day can be spent triaging alerts” due to the overwhelming volume they receive https://swimlane.com/blog/top-soc-analyst-challenges/. Sorting through this flood of alerts to identify the highest priority threats is extremely time consuming.
Tuning out false positives – Many alerts turn out to be false alarms, yet analysts still have to dedicate time to analyzing and dismissing them. This wastes resources better spent investigating legitimate threats https://www.ncbi.nlm.nih.gov/pmc/articles/PMC8344134/.
Lack of context – Alerts often provide limited information about the nature of the potential threat. Without sufficient context, analysts may struggle to accurately triage alerts and determine the appropriate response.
Improving Triaging
There are several ways to improve the triaging process in a security operations center (SOC), including leveraging threat intelligence, security automation, and enriching alerts with context.
Leveraging threat intelligence can help analysts make faster and more accurate triaging decisions by providing additional context about threats. Threat intelligence platforms aggregate data from various sources to identify indicators of compromise and connect related threats. Integrating this data into the SOC’s security information and event management (SIEM) system allows analysts to see threat intelligence linked to specific alerts during triage (Source). This context helps them prioritize which alerts need immediate response.
Security automation can take over repetitive triaging tasks, reducing the burden on analysts. Playbooks can be created to automatically gather data and perform analysis on common alert types. Orchestration engines can run playbooks when predefined conditions are met, taking initial triaging steps without human intervention. This gives analysts more time to work on complex, priority alerts (Source).
Enriching alerts during triaging by adding supplemental data makes it easier to understand and prioritize threats. Integrations can pull in asset context, user information, geolocation, network data, and more. Visual linking charts can illustrate connections between alerts and affected assets. With enhanced context, analysts can make faster triaging decisions and escalate the most critical threats (Source).
Triaging Best Practices
Documenting triaging processes is critical for maintaining consistency and enabling continuous improvement. The triage process should be clearly outlined, detailing the steps analysts take when reviewing and prioritizing alerts. Having a standardized methodology makes it easier to train new analysts and ensures alerts are handled appropriately.https://blueteamresources.in/soc-alert-triage-process/
Balancing automation and human analysis is also important for an efficient triage process. Automation tools can help filter out false positives and surface priority alerts. However, human expertise is still needed to fully investigate and understand complex alerts. The best approach utilizes automation to augment and empower human analysts.https://www.secureworks.com/blog/soc-processes-best-practices-explained
Continuously tuning alert rules is critical to improving the signal-to-noise ratio. Analysts should regularly review alerts generated and fine-tune rules to weed out false positives. Keeping alert logic updated for the evolving threat landscape allows analysts to focus on the most critical threats.
Conclusion
Triaging is a critical process in the security operations center (SOC) that allows analysts to prioritize and process the high volume of security alerts they receive on a daily basis. Effective triaging ensures that the most critical threats are identified and responded to quickly, while less severe issues can be queued for later investigation.
There are several triaging models SOC teams can follow, such as a simple priority matrix or more advanced clustering methods. Using the right triaging tools and techniques is key, whether it is machine learning algorithms that help automatically prioritize alerts or collaborative triaging to leverage team expertise. While triaging can be challenging, especially with alert overload and fatigue, there are best practices teams can implement to improve efficiency and accuracy.
To recap, triaging enables SOC analysts to focus their limited time and resources on the most imminent threats. By leveraging the right models, tools and techniques – and constantly optimizing their processes – SOCs can become more effective at managing and mitigating security risks.