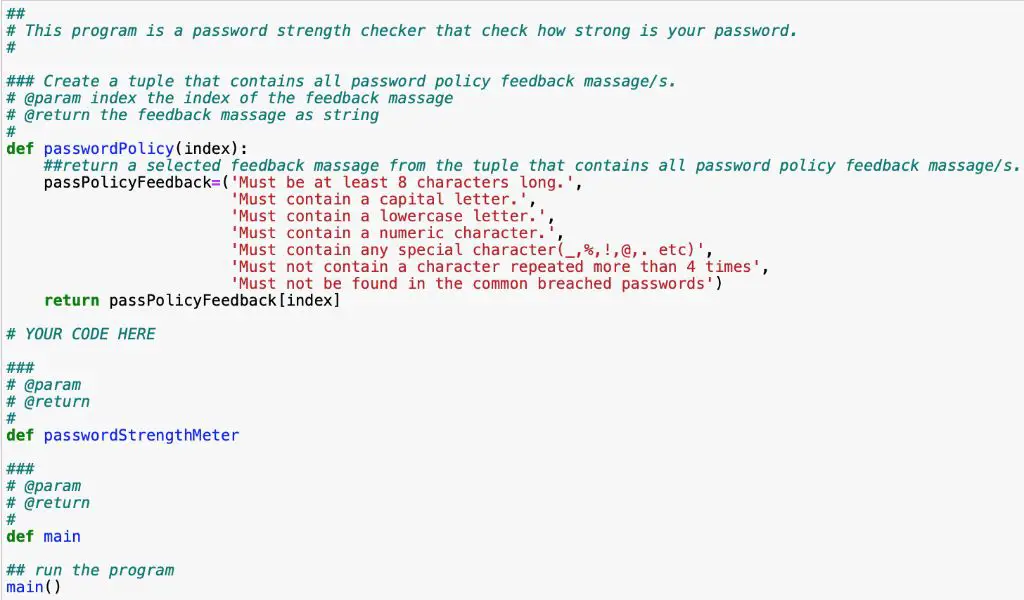
Passwords are an essential aspect of digital security, protecting access to sensitive information and systems. However, poorly constructed passwords are vulnerable to cracking attempts that can compromise accounts. Understanding common password cracking techniques can help inform stronger password policies and user education.
What is Password Cracking?
Password cracking refers to different methods attackers use to gain unauthorized access to password-protected systems. The goal is to determine valid login credentials, usually a username and password combination, that will grant access to a system or account. Attackers utilize a variety of automated tools and techniques to crack passwords. Once a password is compromised, the attacker can then gain access and potentially obtain sensitive data, launch further attacks on connected systems, or cause other forms of damage.
Common Password Cracking Techniques
There are several approaches commonly used to crack passwords, taking advantage of vulnerabilities in password strength, storage, and management. Common password cracking techniques include:
- Dictionary attacks – These attacks use dictionaries of common passwords and words to try different password combinations. Dictionaries may include keywords, common passwords like “password123”, names, fictional characters, keyboard patterns, and other terms that users often employ in passwords.
- Brute force attacks – Brute force attacks work through all possible alphanumeric combinations until the correct password is discovered. Every potential password combination is attempted in succession.
- Hybrid attacks – Hybrid attacks combine elements of dictionary attacks and brute force attacks. For example, a dictionary core password may be coupled with brute force combinations of numbers and special characters.
- Rainbow table attacks – Rainbow tables store pre-computed hashes for common passwords. Hashes extracted from a password database can then be compared to these tables to crack their actual values.
- Keylogging – Keylogging records keystrokes on a compromised machine to capture user passwords and other input.
- Phishing – Phishing scams trick users into revealing their passwords through fraudulent emails, websites, phone calls, or other means.
- Shoulder surfing – Shoulder surfing is a direct observation technique that spies on a user entering passwords or PINs on a device.
- Social engineering – Social engineering exploits human psychology to manipulate people into divulging passwords or other sensitive information.
- Credential stuffing – Credential stuffing is the use of leaked username and password pairs, usually sourced from third-party data breaches, that are tested on other sites and systems.
Using All Possible Character Combinations
One password cracking approach is to systematically test every possible combination of keyboard characters. This exhaustive brute force technique will eventually yield the password, given sufficient time and computing resources. The search space includes:
- All letters a-z and A-Z
- The digits 0-9
- Special characters like !, @, #, $, etc.
Trying every permutation of these allowed characters will crack the password by uncovering the right sequence. The difficulty depends greatly on password length and complexity. Longer passwords with more random character combinations require far more guesses and time to crack. Some estimates based on average computing power:
| Password Length | Possible Combinations | Estimated Crack Time |
| 6 characters | 56 billion | Seconds |
| 8 characters | 218 trillion | Hours to Days |
| 10 characters | 10 quadrillion | Months to Years |
| 12 characters | 5 sextillion | Centuries |
Rainbow table attacks can crack some passwords almost instantly if a hash match is found. Less complex passwords with common keyboard patterns or dictionary words are also vulnerable to very quick cracking times. But longer, more randomized passwords require a substantially increased effort.
Ethical Considerations
While understanding password cracking techniques is useful for improving security, actively cracking passwords without authorization raises major ethical and legal concerns. Malicious password cracking violates privacy, destroys trust, and can enable crimes like theft and fraud. Always respect user rights and system controls when evaluating passwords.
Preventing Password Cracking
Strong password policies and thoughtful system design are key to limiting password cracking risks. Best practices include:
- Enforce lengthy, complex password requirements
- Block common passwords and dictionary words
- Apply multi-factor authentication
- Use cryptographic password hashing
- Limit login attempt failures before lockout
- Monitor for suspicious login activity
- Regularly change critical passwords
- Educate users on password security
No password policy can prevent all cracking attacks. But following cybersecurity best practices will substantially increase the time, resources, and skill required for an outside attacker to illegally gain credentialed system access.
Conclusion
Password cracking attempts to determine valid login credentials by exploiting common password vulnerabilities. Techniques like brute force, dictionaries, rainbow tables, and keylogging automate the process of testing possible passwords. Using every potential keyboard character combination is one exhaustion approach. Proper password complexity, multi-factor authentication, cryptographic hashes, and other security measures are key to protecting against most cracking attacks. Understanding the risks can help inform strong password policies and system protections to safeguard user accounts.