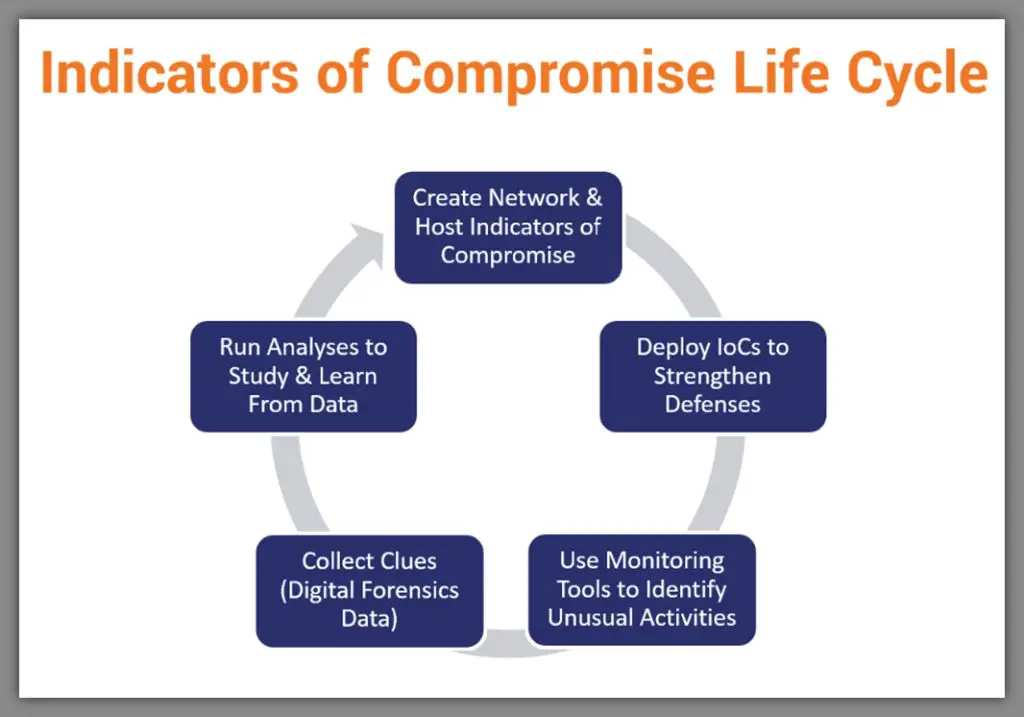
An indicator of compromise (IOC) is a forensic artifact or evidence that signifies a potential security breach or intrusion on a network or system. IOCs provide valuable threat intelligence that can be used to detect, respond to, and prevent cyber attacks. Some common examples of IOCs include:
IP Addresses
Suspicious IP addresses that have been associated with malware, botnets, phishing sites, or other malicious actors can act as IOCs. Security analysts watch for communications with known bad IP addresses as an indication that a system may be compromised.
Domain Names
Domain names involved in spear phishing campaigns, hosting malicious downloads, or linked to command-and-control servers are also good IOCs to monitor. DNS request logs can be checked for lookups of malicious domains.
Email Senders and Subject Lines
Watching for emails from suspicious senders, containing particular keywords in the subject, or with attachments matching known malware file hashes can reveal targeted phishing attempts and recipients who may have been compromised.
Malicious Files
File hashes, signatures, metadata, and behaviors can indicate malware. When hostile files are detected, it signals an attack attempt and/or a successful intrusion. Collecting details around malicious files provides data to block future infections.
Registry Keys
Registry changes are often made by malware to add persistence or enable malicious behaviors. Tracking additions or alterations to registry keys can reveal compromised hosts.
Mutex Objects
Malware frequently uses mutual exclusion (mutex) objects to signal and synchronize behaviors between malicious processes. The presence of known hostile mutexes is an indicator that a system has been infected.
Clipboard Contents
Some types of malware collect sensitive information from a compromised computer and copy it to the clipboard. Monitoring clipboard contents can help catch data exfiltration attempts.
Process Injection
Malicious code often injects into legitimate running processes as a way to disguise its presence and gain privileged access. Unusual code injections can serve as evidence of a compromise.
Webshells
Webshells are scripts planted on web servers that enable remote administration over HTTP or HTTPS. Their presence represents a breach of a web application and control over the server.
Lateral Movement
Attackers will often move laterally across a network to infect additional hosts after the initial breach. Signs of unauthorized internal connections, service usage, or account logins point to compromise and ongoing malicious activity.
Data Exfiltration
Increased outbound network traffic, particularly over encrypted connections, may indicate an attacker extracting stolen data from the environment.
Anti-Analysis Techniques
Advanced malware employs evasion and misdirection techniques specifically designed to avoid detection and analysis. Signs of anti-debugging, sandbox avoidance, and fileless execution provide valuable behavioral IOCs.
PowerShell Commands
Hackers often abuse PowerShell for execution of malicious code. Logging PowerShell usage can provide both file-based and behavioral indicators to identify compromised hosts and users.
Rare Processes
The appearance of unusual processes on a system that are rarely or never seen before can signify malicious activity. Attackers may rename files and tools to mask their presence.
System Configurations
Altered system settings like disabled firewalls, terminated processes, removed logged entries, and open ports may indicate a compromised host. Attackers modify configurations to avoid defenses and maintain persistence.
Unauthorized Software
The introduction of hacking tools, backdoors, rootkits and other unauthorized software points to a breach. Closely monitoring software inventories can uncover malicious components.
Service Stoppages
Malware and attackers will often disable security services like antivirus, logging and auditing to prevent detection. Service interruption can confirm a successful intrusion is underway.
Suspicious User Activity
Unusual login locations, timestamps and commands executed by users suggests account compromise. Monitoring user behaviors and activity patterns spots imposters.
Trusted Relationship Exploitation
Threat actors target trusted relationships between systems and accounts to expand access. Unexplained communication between networks, domains and users warrants further scrutiny as a possible IOC.
System Crash Dump Analysis
Inspecting memory and disk images from crashed systems can uncover infection artifacts like injected code, hidden registry keys, and malicious files that evaded defenses.
Third Party Detections
Signals from threat feeds, security researchers, law enforcement, and industry partners connected to an organization’s assets help confirm live incidents.
Conclusion
Indicators of compromise come in many forms, but all provide valuable threat intelligence to bolster defenses. Technical IOCs like file hashes and IP addresses detect known bad actors, while behavioral anomalies highlight emerging tactics. Rapidly understanding and leveraging IOCs is key for effective detection, response and prevention.
Example Table of Common IOCs
| IOC Type | Examples |
|---|---|
| IP addresses | 194.177.21[.]181 103.255.61[.]39 |
| Domain names | loadservice[.]space freescanav[.]com |
| Email sender / subject | anomaly@notification[.]email Your Payment Details |
| File hashes | 8cab57290915f80f921a341e9d23c0e 325adf4c9ab80facd5ab555c1e720fd |
| Registry keys | HKLM\SOFTWARE\Policies\Microsoft\Windows\Safer\CodeIdentifiers\0\Hashes\8CAB572 HKCU\Software\classes\clsid\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InProcServer3 |
| Mutex objects | Global\MsWinZonesCacheCounterMutexA0 Global\_DecryptFile0 |
| Processes | notifier.exe sqlservr.exe |
| Accounts | malwareservice tempuser02938 |
This table provides examples of common IOC types that can indicate malicious activity on a network or system. Tracking and correlating observables like these enables rapid detection of compromises and targeted attacks.
Real World Example of Using IOCs
In December 2020, the cybersecurity firm FireEye reported that it had suffered a breach by a sophisticated state-sponsored attacker. FireEye’s public disclosure included over 100 IOCs related to the incident.
These IOCs included details such as:
- Yara rules identifying unique malware files used by the attacker
- MITRE ATT&CK techniques observed being used
- Malicious domain names and IP addresses contacted by the attacker
- Compromised credentials exploited
- False digital certificates used to sign malicious tools
Equipped with this information, organizations were able to check their own networks and systems for matching IOCs that could indicate they were also victims of related intrusions.
Many were able to identify signs of compromise. For example, the cybersecurity firm Volexity used the IOCs to uncover that it had been targeted by the same threat actor as part of a wider campaign. The attacker had exploited a vulnerability in Volexity’s VPN gateway to gain access.
By quickly leveraging the indicators released by FireEye, Volexity was able to find, respond to, and remediate the breach before the attackers were able to complete their objectives. Rapid IOC sharing and matching empowered them to take action against the threat.
Key Takeaways
- IOCs provide valuable threat intelligence by signaling intrusions and attacks
- Technical artifacts like file hashes can detect known threats
- Behavior anomalies highlight novel attacker tactics
- Public IOC sharing enables collaborative community defense
- Rapid intake and usage of IOCs improves security outcomes
Frequently Asked Questions
What are some common sources of IOCs?
IOCs can come from various sources, including:
- Security vendors and researchers
- Public threat feeds and repositories
- Law enforcement and government agencies
- Industry groups and ISACs
- Malware repositories and sandboxes
- Incident response activities
- IT and security monitoring controls
- Open source intelligence (OSINT)
What are some ways to leverage IOCs for security?
Organizations can use IOCs in various ways to bolster their security, including:
- Blocking malicious IP addresses and domain names
- Detecting files and executables via signature scanning
- Identifying anomalies through behavioral analytics
- Enriching security events with threat intelligence
- Alerting on high-fidelity indicators of attack
- Proactively hunting for breaches and lateral movement
- Prioritizing patching and mitigations based on exploitability
What are some challenges with sharing and using IOCs?
Some potential challenges include:
- Massive volume of IOCs generated daily
- Difficulty identifying the most high-fidelity IOCs
- Inability to operationalize IOCs across disparate security tools
- Limited context provided with raw technical IOCs
- Onerous manual efforts to continually update defenses
- Delayed public disclosure of IOCs by attacked entities
How can organizations improve their utilization of IOC intelligence?
Steps organizations can take include:
- Seeking IOCs from both public and private sources
- Automating ingestion and updating of IOCs into security controls
- Focusing on IOCs with greater context and high confidence ratings
- Leveraging standards like STIX/TAXII for maximal sharing
- Enabling IOC matching across previously siloed tools
- Dedicating resources to monitoring emerging IOCs full time
- Proactively threat hunting using IOC analytics
Conclusion
Indicators of compromise empower organizations to detect malicious activity faster and respond quickly to minimize damage. However, IOCs are only as effective as an entity’s ability to rapidly intake intelligence and act upon it across their environment. Developing robust mechanisms to operationalize IOC observables from diverse sources into defenses is key to maximize their value.