Digital forensics is the process of preserving, collecting, validating, identifying, analyzing, interpreting, documenting, and presenting digital evidence derived from digital sources for the purpose of facilitating or furthering the reconstruction of events found to be criminal, or helping to anticipate unauthorized actions shown to be disruptive to planned operations.
What are the basic steps in digital forensics?
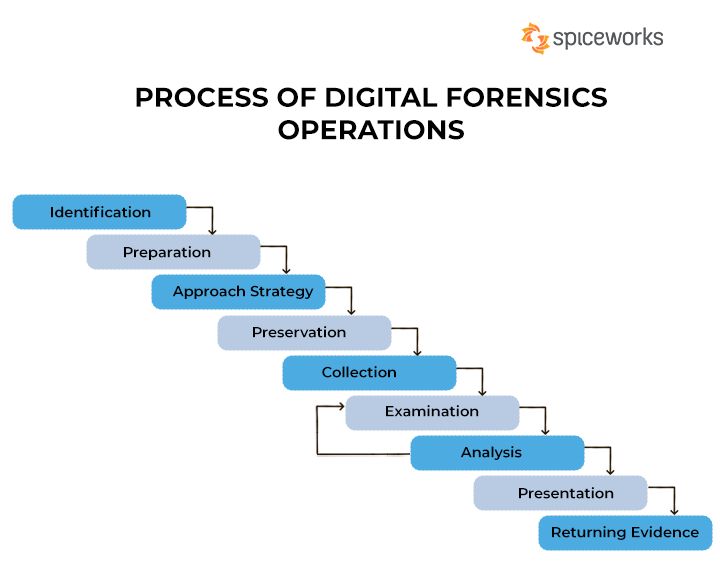
The basic steps in digital forensics include:
- Identification – Identifying sources of digital evidence such as computers, mobile devices, network logs, etc.
- Preservation – Securing and isolating the identified sources of evidence to prevent tampering or destruction.
- Collection – Gathering the digital evidence from the identified sources while maintaining integrity.
- Examination – Forensically analyzing the collected data using specialized tools.
- Analysis – Interpreting the results from the examination to reconstruct events.
- Documentation – Recording the processes and findings from the analysis.
- Presentation – Summarizing and explaining the implications of the findings.
What are the standard digital forensic investigation models?
Some standard models used in digital forensic investigations include:
- DFRWS Investigative Model – Developed by the Digital Forensics Research Workshop, this model involves Identification, Preservation, Collection, Examination, Analysis, Presentation, and Decision stages.
- NIST SP 800-86 Model – Developed by the National Institute of Standards and Technology, this model consists of Collection, Examination, Analysis, and Reporting phases.
- Enhanced Integrated Digital Investigation Process Model – Proposed by Baryamureeba and Tushabe, this model adds Preparation and Sharing stages to the basic four-step process.
- Ciardhuáin Model – Focuses on the Iterative process with Preparation, Iteration (Identification, Collection, Transport, Storage, Examination, Hypothesis, Presentation), and Closure stages.
What are the different types of digital evidence?
Types of digital evidence include:
- Network traffic and logs – Data from network connections, firewalls, IPs, and internet history.
- Digital communication – Emails, instant messages, voicemails.
- Documents and photos – Text documents, presentations, spreadsheets, diagrams, images.
- Databases – Corporate databases, phone records, sensitive internal data.
- Audit trails – User activity logs, access logs, surveillance data.
- Mobile devices – Cell phones, tablets, GPS devices.
- Computer systems – Servers, workstations, network drives.
- Cloud data – Social media, webmail, online file storage.
What are some key challenges in digital forensics?
Some key challenges faced in digital forensics include:
- Increasing size of storage media makes collection time consuming.
- Advanced encryption can prevent access to evidence.
- Anti-forensics like data hiding, destruction and booby traps.
- Complex formats and proprietary systems require advanced skills.
- Cross-jurisdictional legal and privacy issues.
- Rapidly changing technology like cloud computing adds complexity.
- Potential loss of volatile data if not captured live.
- Chain of custody maintenance can be difficult.
What are the different categories of digital evidence?
Digital evidence can be categorized into the following types:
- Active vs Passive – Active evidence contains current data such as files, network traffic, memory. Passive evidence has residual data like registry entries, logs, hidden files.
- Persistent vs Volatile – Persistent evidence is stored on permanent media like hard drives. Volatile evidence only exists while powered on, like RAM data.
- Direct vs Indirect – Direct evidence can directly establish a fact like child abuse photos. Indirect evidence provides support like internet search history.
- Incriminating, Exculpatory, Neutral – Incriminating evidence implicates the suspect. Exculpatory evidence exonerates the suspect. Neutral has no clear implication.
What are some key principles for digital evidence collection?
Principles for proper collection of digital evidence include:
- Handle original evidence as little as possible.
- Account for any change in evidence while in custody.
- Comply with rules of evidence like warrants and consent.
- Use forensically sound methods and tools.
- Maintain detailed notes on all procedures used.
- Follow chain of custody procedures strictly.
- Ensure integrity of evidence with hashing and signatures.
- Capture as much volatile and contextual data as possible.
- Duplicate evidence bit-for-bit for analysis.
What are some key forensic tools and techniques?
Key digital forensic tools and techniques include:
- Forensic imaging – Creating bitstream copies like dd, SafeBack, Encase.
- Write blockers – Hardware/software to prevent modification of evidence.
- Network tools – Capture network traffic with Wireshark, NetworkMiner.
- Mobile forensics – Extract data from mobile devices.
- Live analysis – Investigate systems from volatile memory using Helix.
- File recovery – Retrieve deleted files with Autopsy, Foremost.
- Password cracking – Access locked resources using Ophcrack, Cain & Abel.
- Steganalysis – Detect hidden data with Stegdetect, Stegbreak.
What are the different types of digital forensic investigations?
Types of digital forensic investigations include:
- Criminal – Support law enforcement in crimes like fraud, theft, hacking.
- Incident response – Internal investigations of policy violations, unauthorized activity.
- Malware analysis – Reverse engineering malware like viruses, ransomware.
- Intrusion investigation – Probe network intrusions and data breaches.
- Employee monitoring – Monitor and analyze insider actions.
- Civil litigation – Support lawyers in lawsuits and disputes.
- Electronic discovery (eDiscovery) – Identify and produce relevant electronic records.
What are some specialized branches of digital forensics?
Specialized branches of digital forensics include:
- Mobile forensics – Extracting evidence from mobile devices.
- Network forensics – Investigating network traffic and logs.
- Database forensics – Analyzing database tampering and misuse.
- Cloud forensics – Recovering cloud-based artifacts.
- Malware analysis – Reverse engineering malware.
- Memory analysis – Acquiring evidence from a system’s RAM.
- Threat intelligence – Gathering data to understand cyber threats.
- Multimedia forensics – Analyzing digital images, video and audio.
What are some ethical issues in digital forensics?
Ethical issues that can arise in digital forensics include:
- Respecting personal privacy rights.
- Revealing too much irrelevant personal information.
- Encryption limiting access to evidence.
- Jurisdictional differences in evidence rules.
- Obtaining proper legal authority for each stage.
- Keeping proprietary information confidential.
- Preventing incidental damage to systems.
- Ensuring qualified experts perform analysis.
- Disclosing exculpatory evidence fairly.
How do you ensure admissibility of digital evidence?
Ensuring the admissibility of digital evidence involves:
- Obtaining proper warrants and legal authority.
- Following proper evidence handling procedures.
- Thoroughly documenting all collection and analysis steps.
- Preserving chain of custody.
- Using forensically sound tools and methods.
- Verifying integrity with hashes and signatures.
- Having experts qualified to testify about methods used.
- Showing relevance and authenticity of the evidence.
- Proving reliability by showing no tampering or errors.
- Meeting any statutory technology-specific requirements.
What qualifications and skills make a good digital forensics expert?
Desirable skills and qualifications for a digital forensics expert include:
- Relevant education in computer science, criminal justice, etc.
- Specific digital forensics training and certification.
- Hands-on experience with various OS platforms and devices.
- Thorough knowledge of forensic tools and methodologies.
- Understanding of laws, policies, standards and ethics.
- Proficiency in recovering files and investigating networks.
- Excellent documentation and communication abilities.
- Skill with providing expert testimony in court.
- Strong attention to detail.
- Ability to think logically and critically analyze.
Conclusion
Digital forensics involves the scientifically derived identification, collection, validation, analysis, interpretation, documentation, and preservation of digital evidence. While a relatively new field, it builds on time-tested forensic principles and provides specialized methodologies and tools for evidence recovery from digital devices and networks while maintaining stringent evidentiary standards. With digital artifacts becoming ubiquitous in crimes and civil litigation, sound digital forensic capabilities are crucial for law enforcement, enterprises, and the legal system.